Wireshark is the world’s most advanced network protocol analyzer. It allows you to see at the microscopic level what is happening in your network. today we will learn how to use wireshark filter
by Kalitut
Wireshark is the world’s most advanced network protocol analyzer. It allows you to see at the microscopic level what is happening in your network. today we will learn how to use wireshark filter

by Walid Salame
Many users do not even realize that by filling in the login and password when registering or authorizing on a closed Internet resource and pressing ENTER, this data can easily be intercepted. Very often they are transmitted over the network in a non-secure manner. Therefore, if the site on which you are trying to log in uses the HTTP protocol, it is very easy to capture this traffic, analyze it using Wireshark and then use special filters and programs to find and decode the password so how to capture passwords with wireshark.
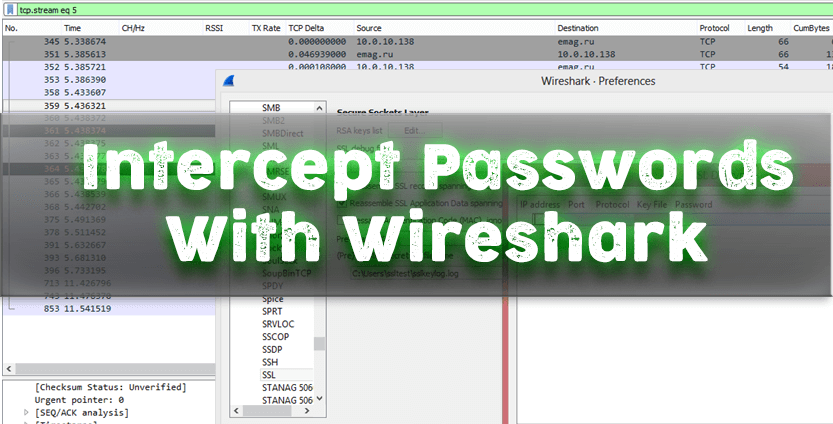
The best place to intercept passwords is the core of the network, where all users’ traffic goes to closed resources (for example, mail) or in front of the router to access the Internet when registering with external resources. Adjust the mirror and we are ready to feel like a hacker.
[Read more…] about How to capture passwords with wiresharkby Kalitut
Decrypt WPA traffic in Wireshark
Let’s start with the theory to understand why the process of decrypting WiFi traffic in Wireshark requires some effort and why one cannot simply decrypt any captured WiFi traffic even if there is a password from the Access Point.
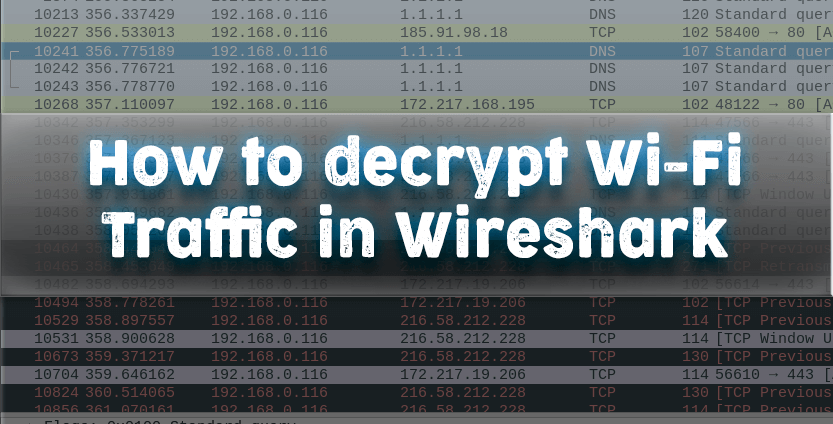
When transmitting over WiFi, the traffic is encrypted using PTK (the Pairwise transient key can be translated as a Pair of Transition Key). At the same time, PTK is dynamic, that is, it is created anew for each new connection. Thus, it turns out that WiFi traffic for each connection in the same Access Point is encrypted with different PTK, and even for one Client after reconnection, PTK changes. To calculate PTK, you need data from a four-stage handshake, as well as a password from a WiFi network (in fact, you also need other information, such as the network name (SSID), but obtaining this data is not a problem).
[Read more…] about How to decrypt wifi traffic wiresharkby Kalitut
we will use wireshark and GeoIp to make an ip geolocation map, If Wireshark is compiled with GeoIP support and you have free Maxmind databases, then the program can determine the location of computers by their IP addresses. Check in About | Wireshark , that the program is compiled with the version that you have available. If GeoIP is on the list, then check the availability of GeoLite City, Country, and ASNum databases on the disk.

How to use the Maxmind GeoLite database to generate a ip geolocation map …
example made on Linux ( Kali Linux ) … it will work the same way on windows
we will generate the map by analyzing a pcap file using Wireshark and GeoLite database to locate every IP the map.
