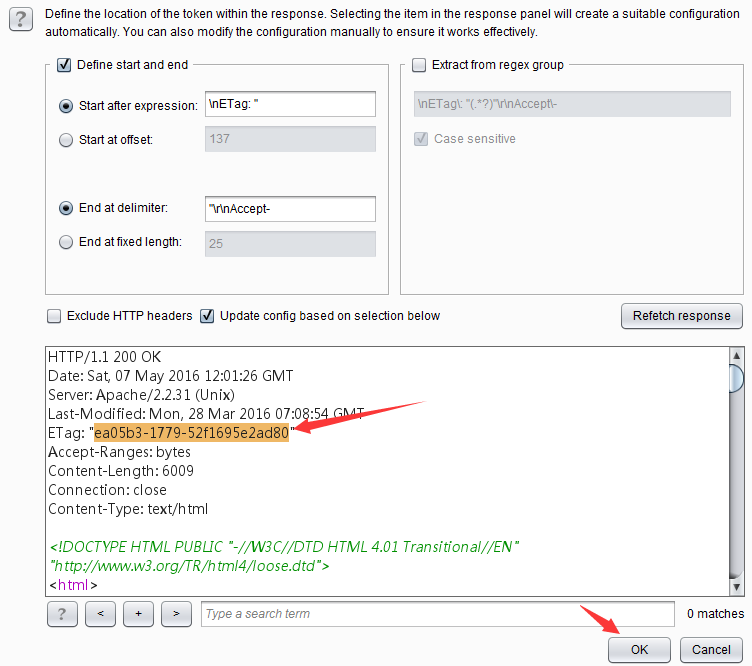
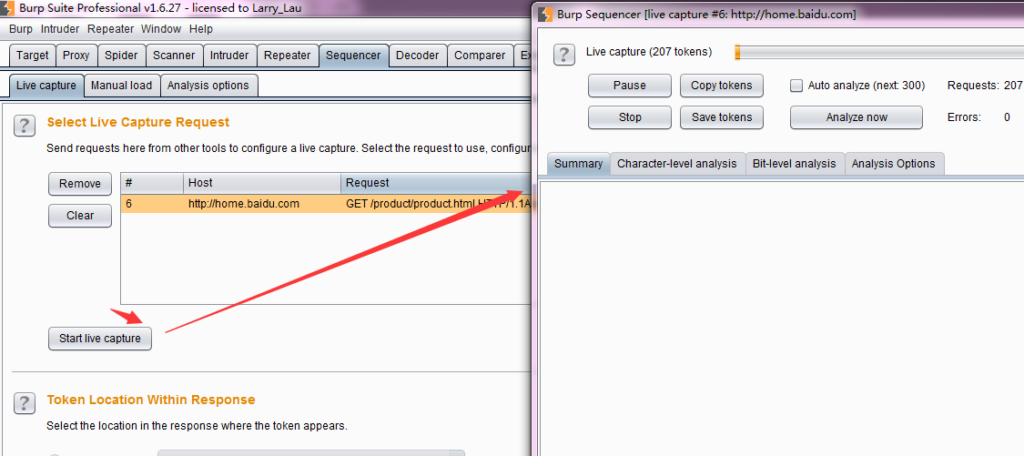
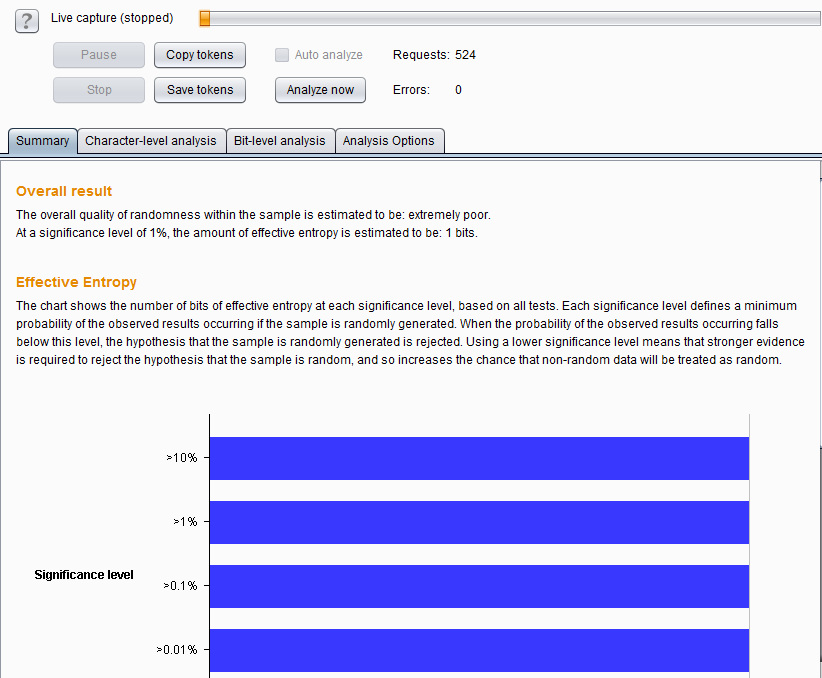
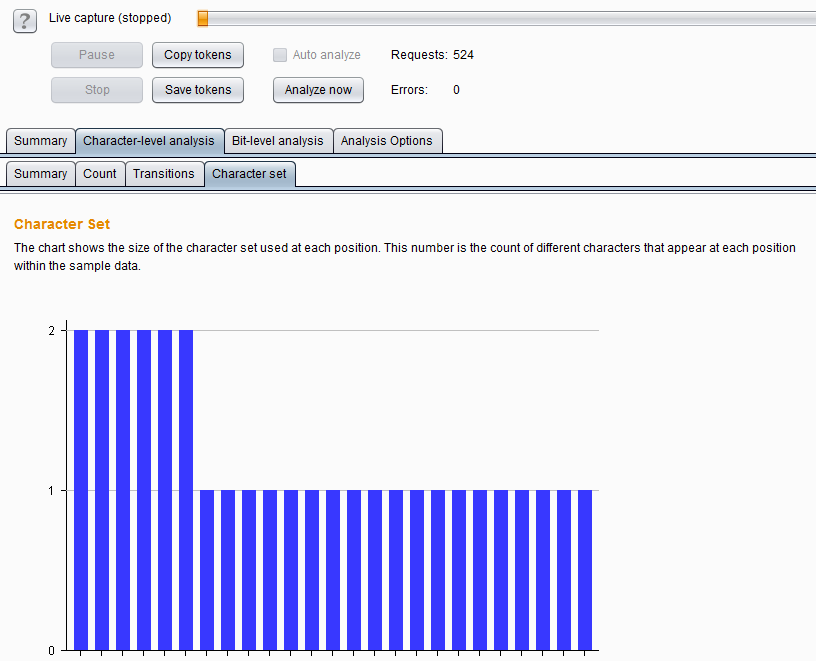
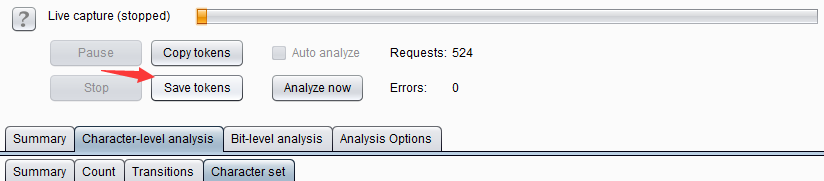
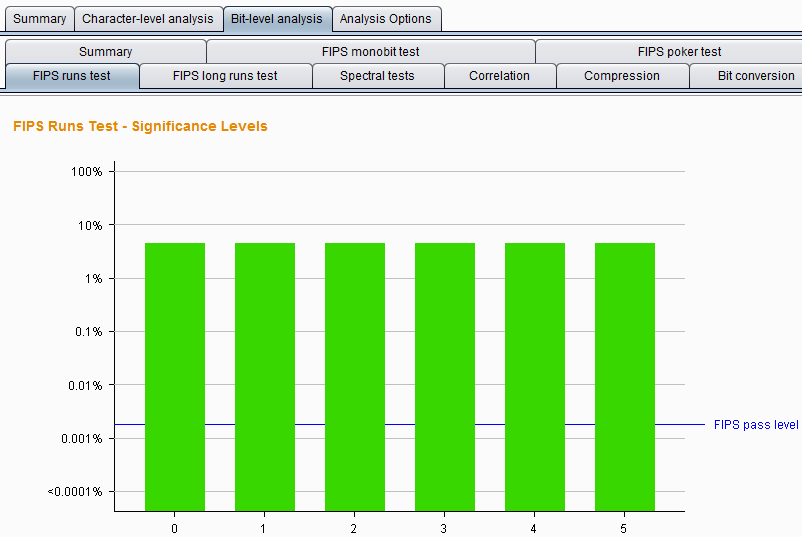
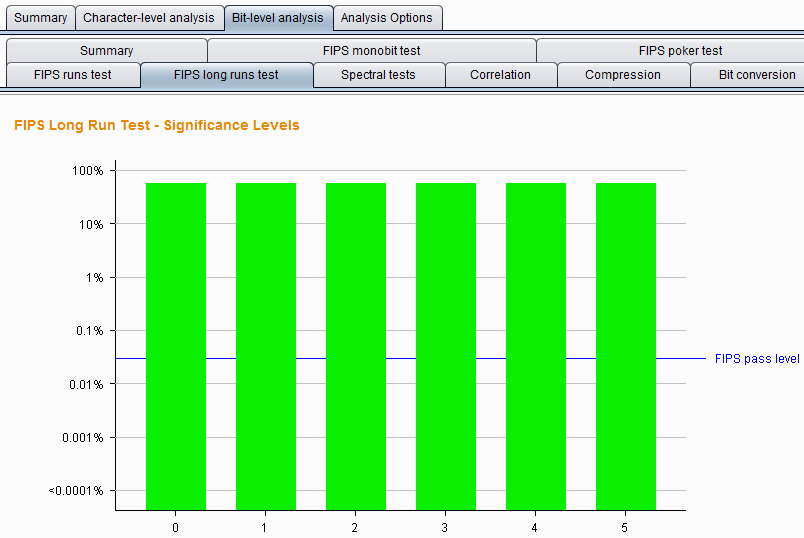
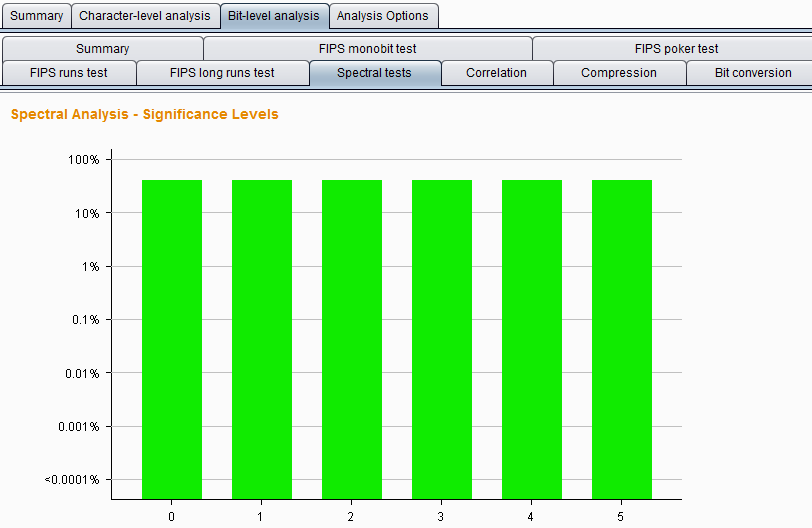
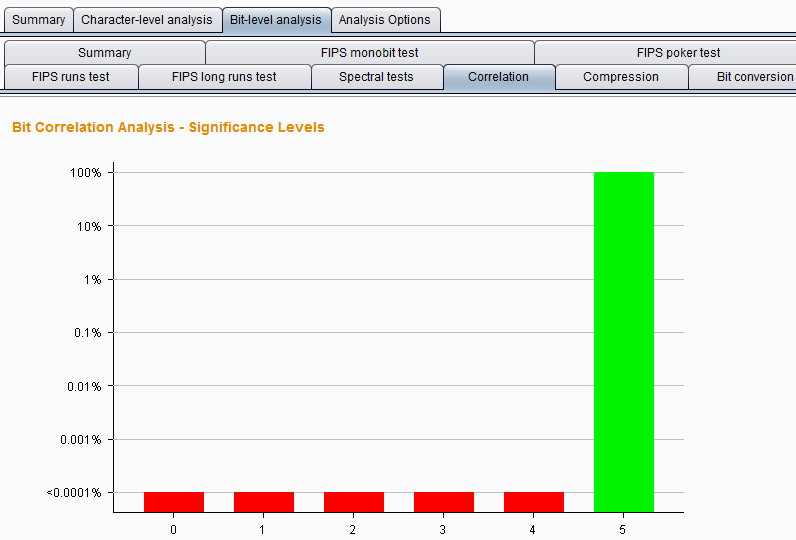
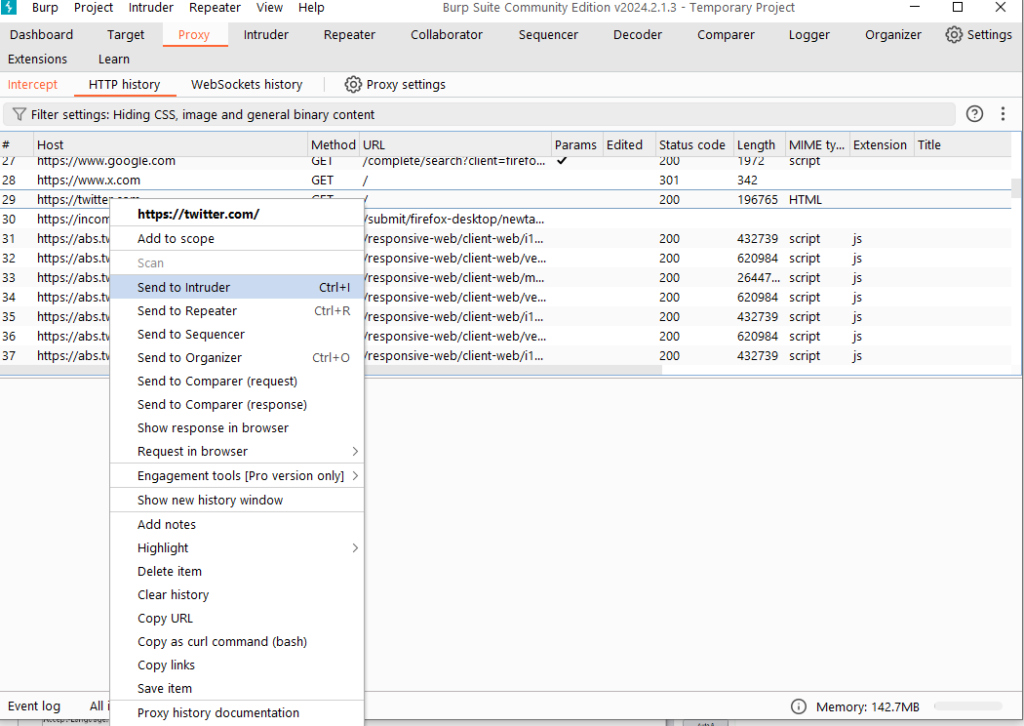
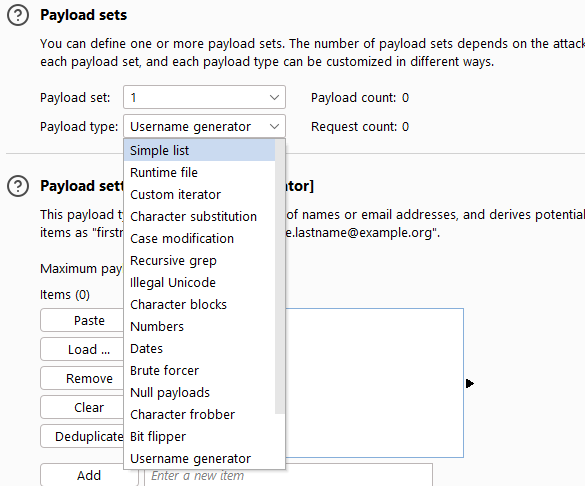
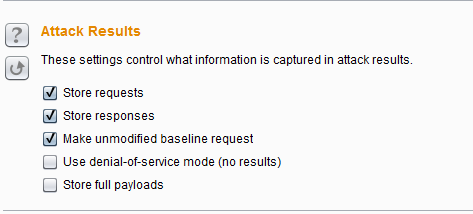
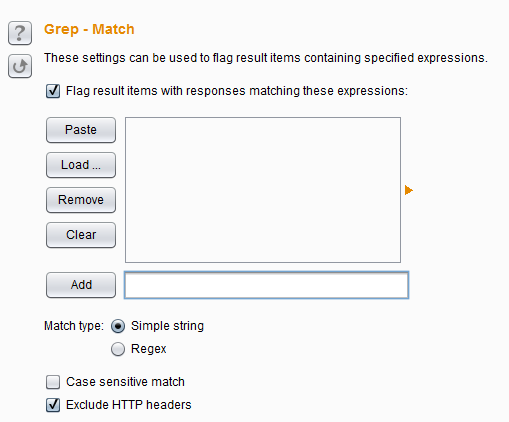
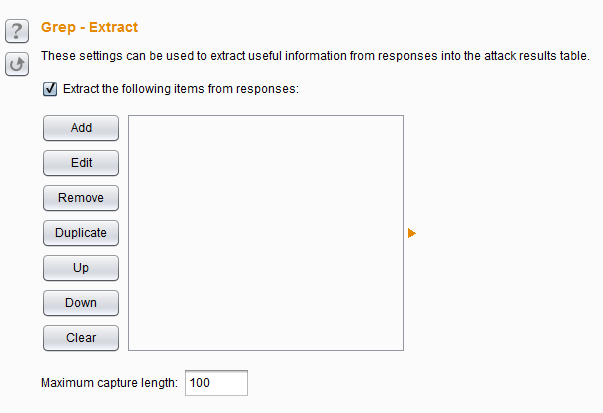
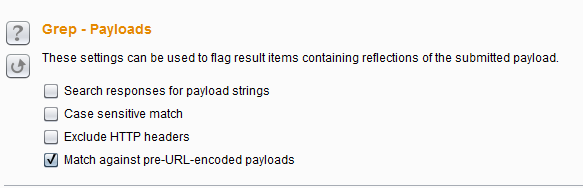
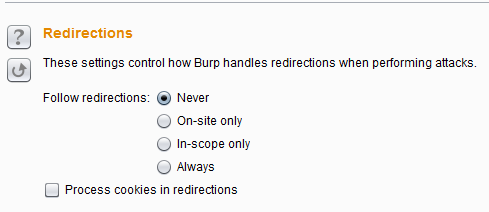
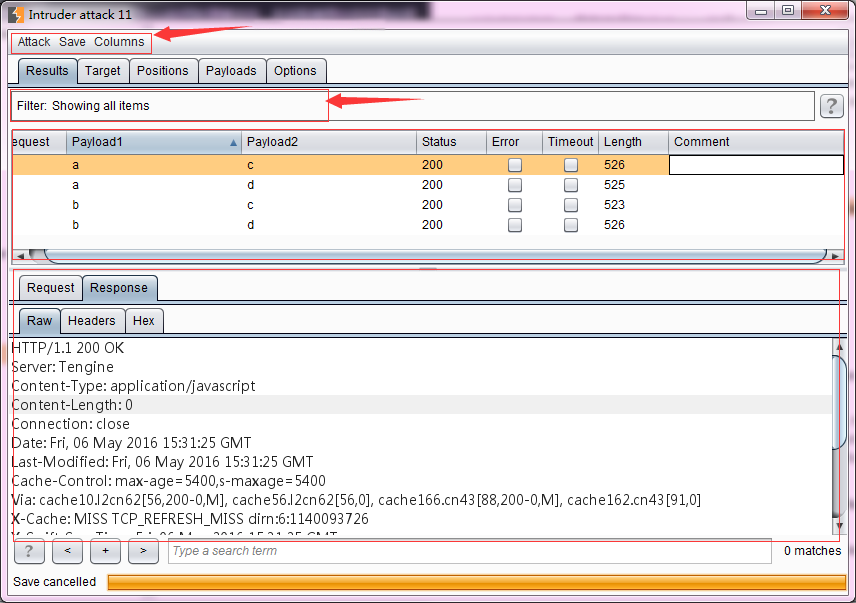
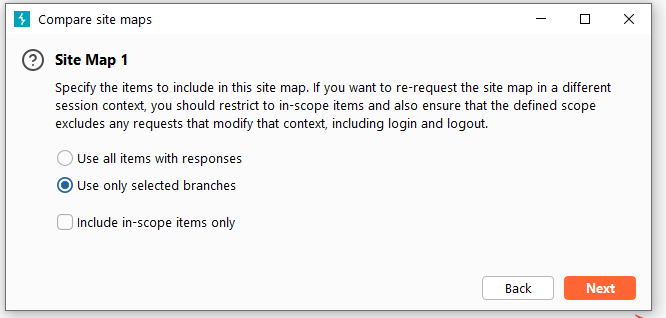
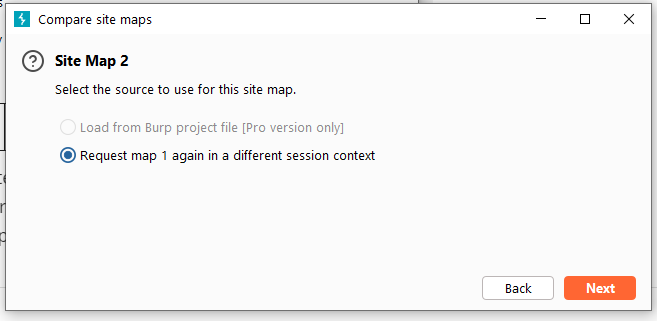
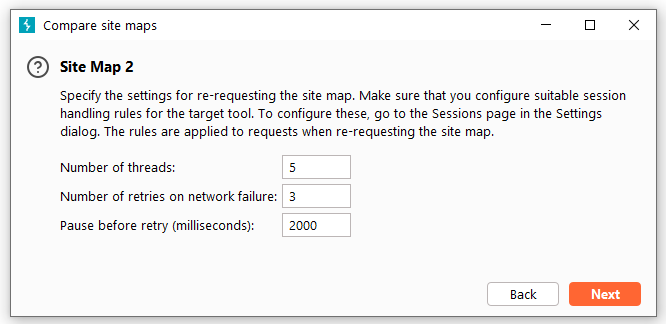
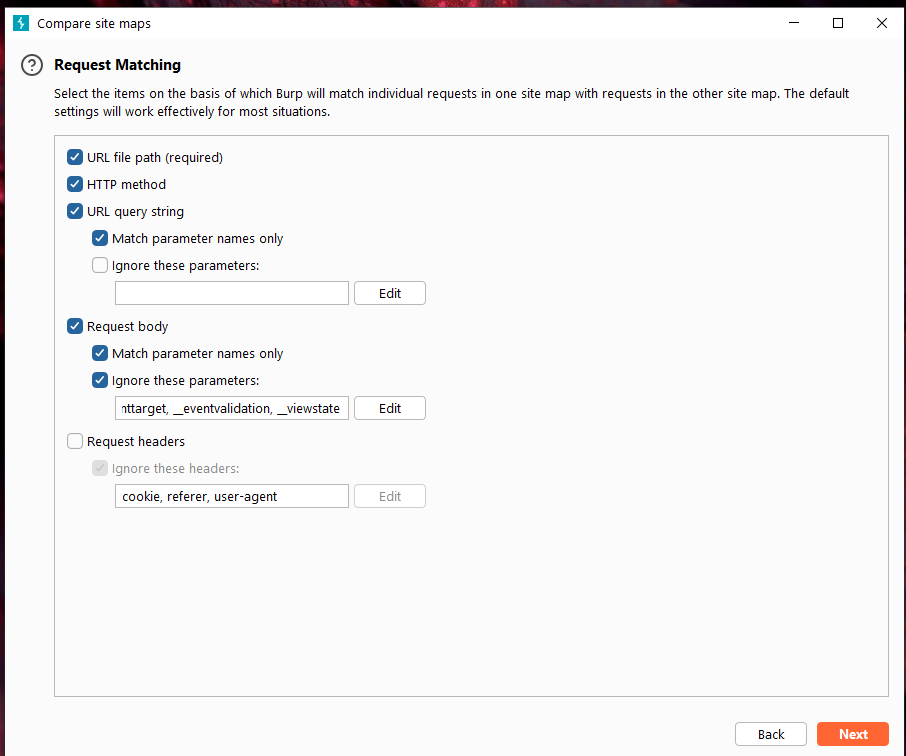
Burp Decoder: Tool for decoding and encoding various data formats, such as Base64, URL encoding, and hexadecimal, for web security testing.
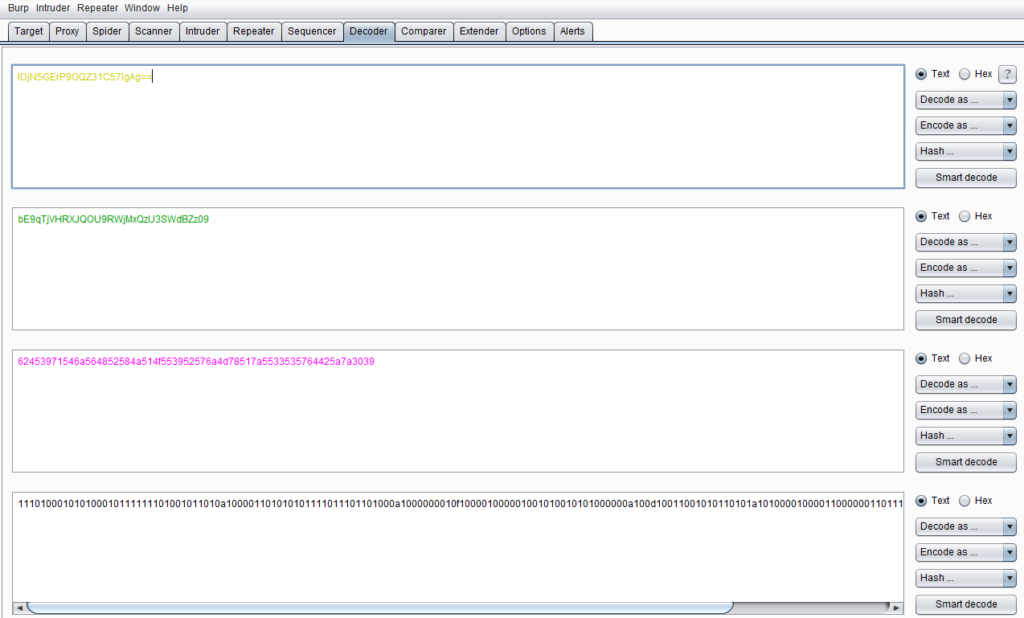
The function of Burp Decoder is relatively simple. As a coding and decoding tool in Burp Suite, it can convert raw data into various encoding formats and hashes. The interface is as shown below, which mainly consists of three parts: input field, output field, and encoding and decoding options.
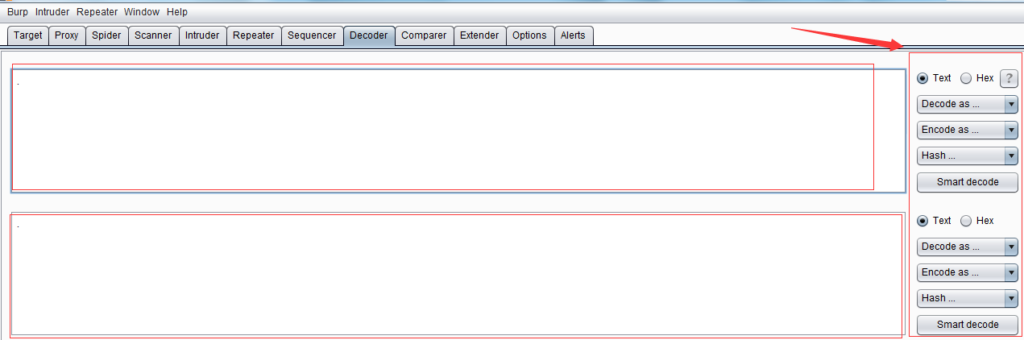
The input field is to input the original data that needs to be decoded. You can fill in or paste it directly here, or you can use [Send to Decoder] in the context menu of other Burp tools; the output field is to display the result of decoding the input field. Both the input field and the output field support both text and Hex formats.
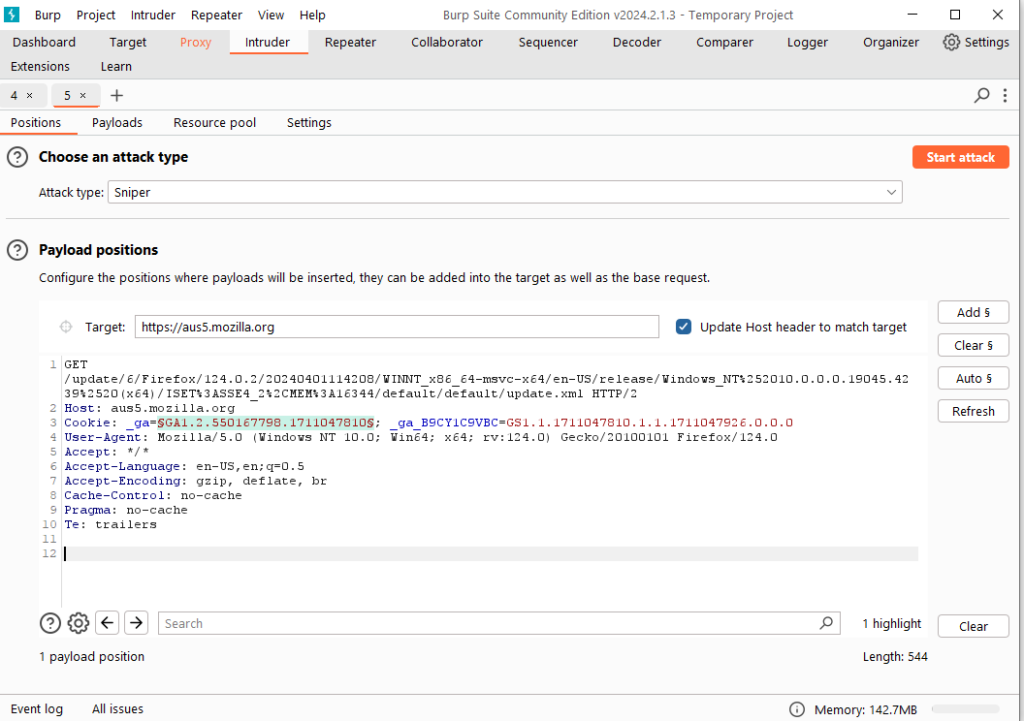
The encoding and decoding options consist of three options: Decode as, Encode as, and Hash. In actual use, it can be set according to the needs of the scene. For encoding and decoding options, currently eight forms of format conversion are supported: URL, HTML, Base64, ASCII, hexadecimal, octal, binary, and GZIP. Hash hashing supports SHA, SHA-224, SHA-256, Conversion of SHA-384, SHA-512, MD2, and MD5 formats. More importantly, for the same data, we can perform multiple encoding and decoding conversions on the Decoder interface. As shown below:
How to use Burp Comparer
Burp Comparer: A feature in Burp Suite for comparing two HTTP responses or requests to identify differences, aiding in vulnerability analysis.
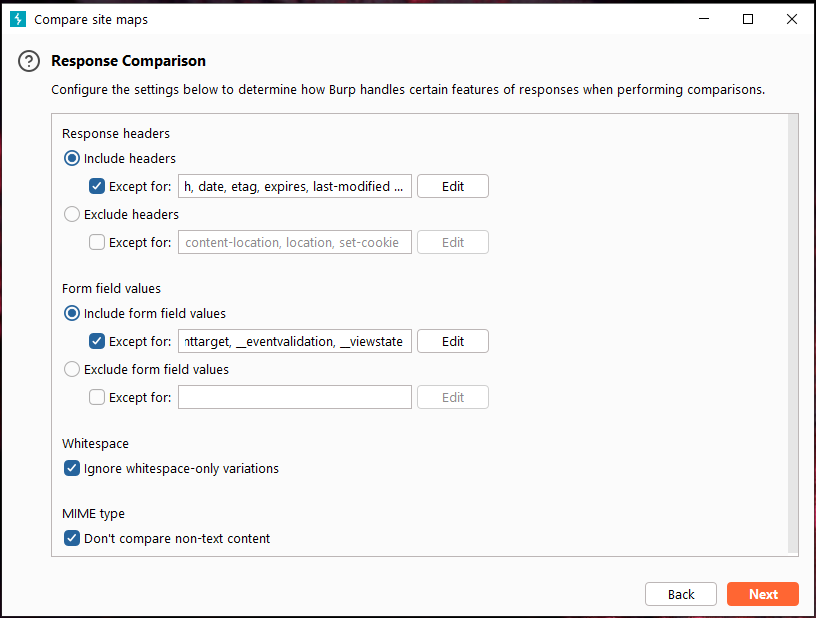
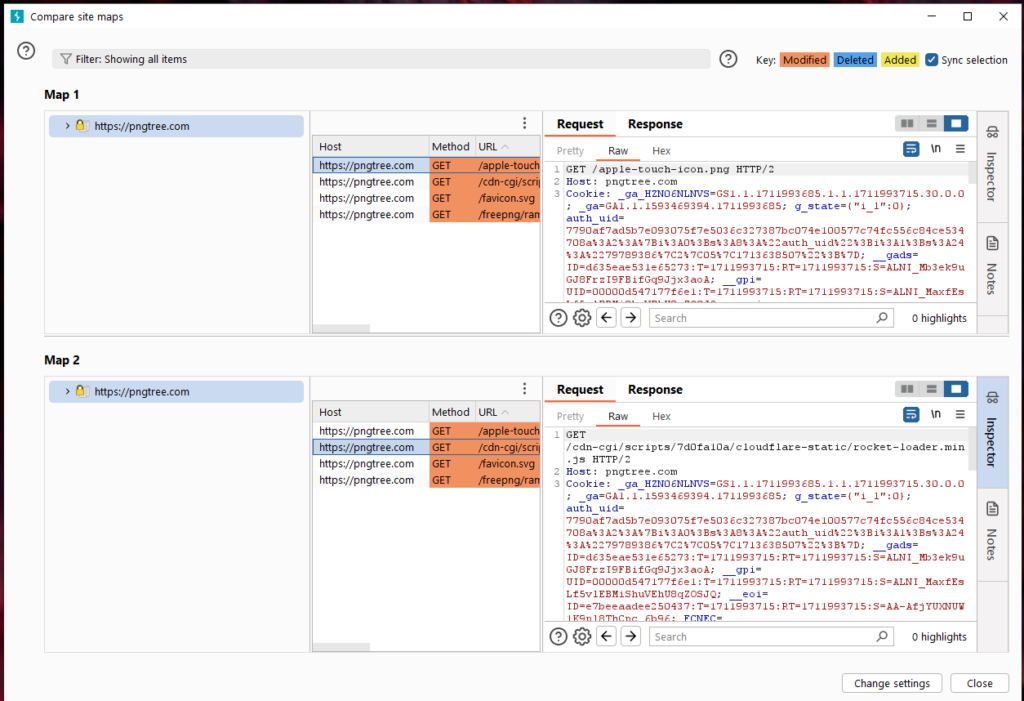
Burp Comparer mainly provides a visual difference comparison function in Burp Suite to compare and analyze the difference between two data. The scenarios in use may be:
- During the process of enumerating user names, compare and analyze the difference in the server-side feedback results when the login is successful and failed.
- When using Intruder to attack, for different server-side responses, you can quickly analyze the difference between the two responses.
- When performing blind injection testing of SQL injection, compare the difference between the two response messages and determine the relationship between the response results and the injection conditions.
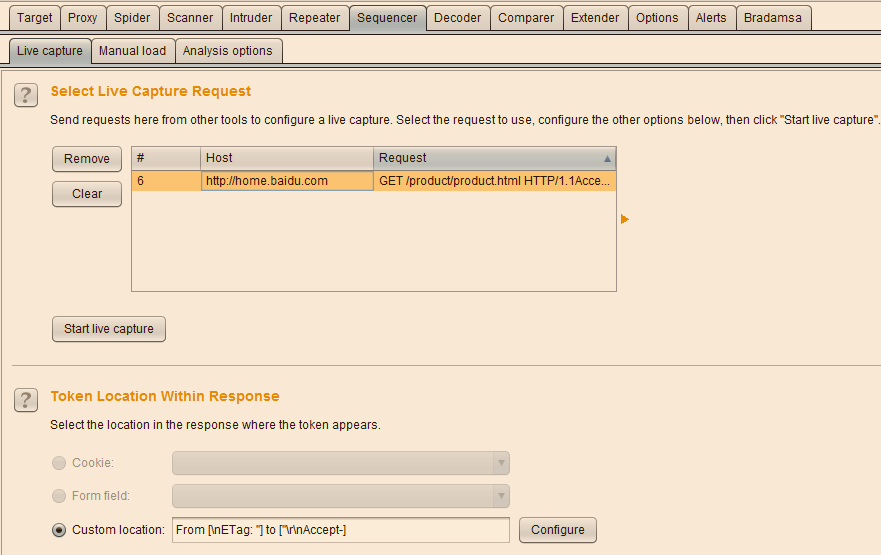
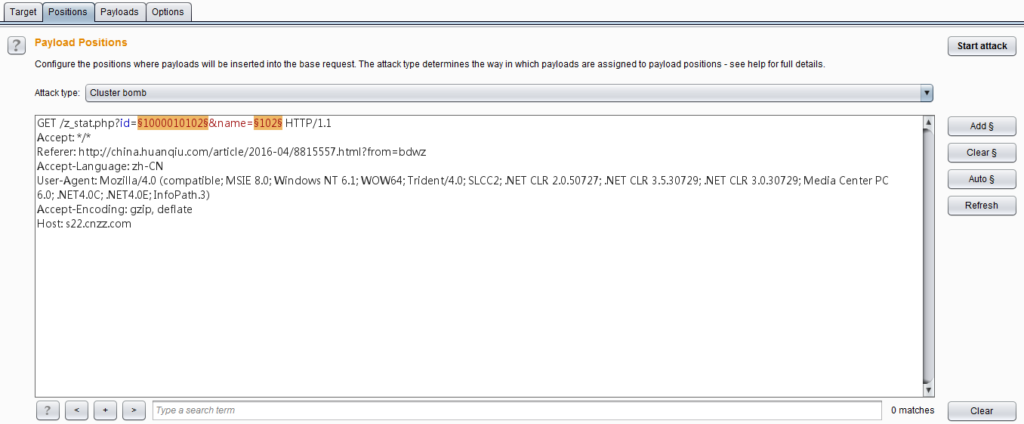
The interface is as shown below:
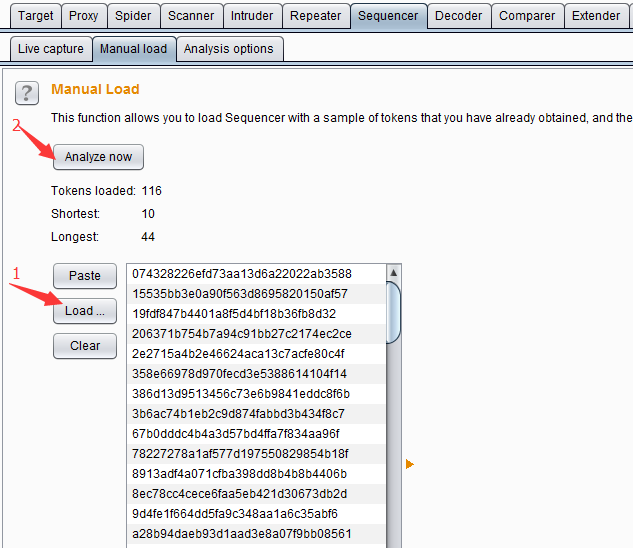
The use of Comparer mainly consists of two links, first data loading, and then difference analysis.
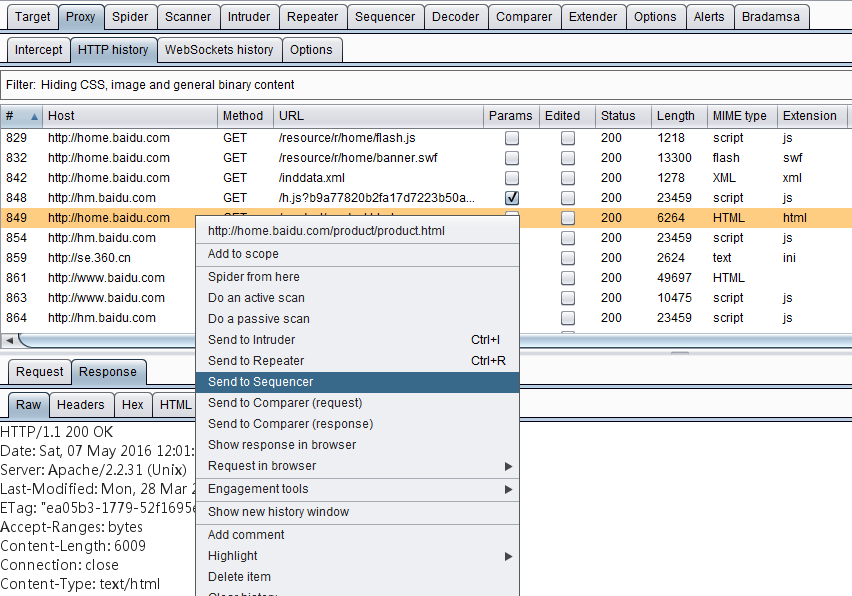
Commonly used methods for loading Comparer data are: forwarding from other Burp tools through the context menu, pasting directly, and loading from files. When loading is complete, if you select two different request or response messages, the issued comparison button will be activated, and you can choose text comparison or byte comparison. As shown below:
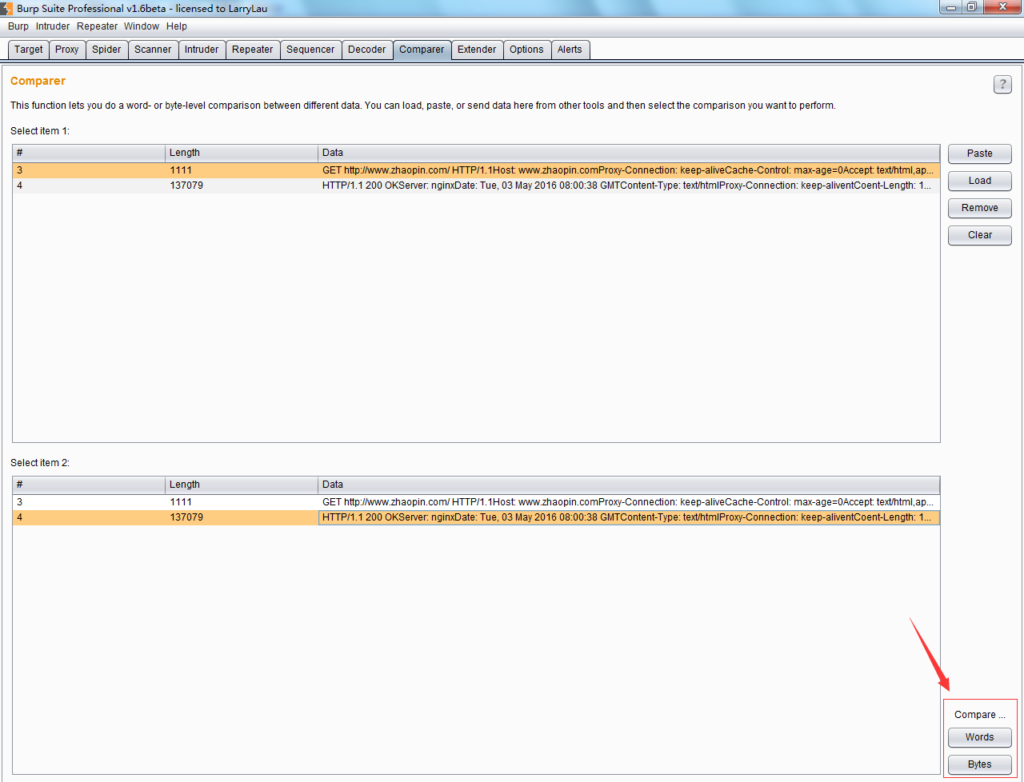
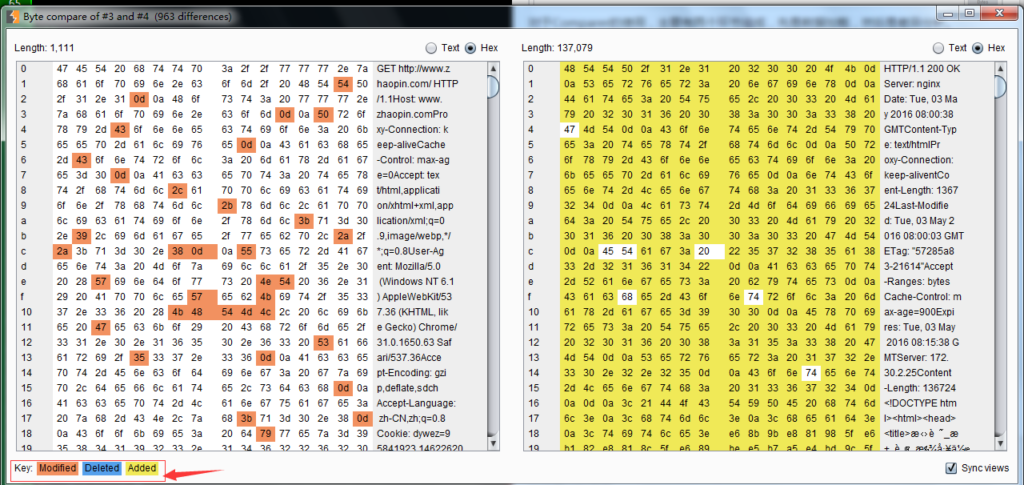
If you click [words] or [bytes], you will enter the comparison interface, and the page will automatically display the difference in data through the background color. As shown below:
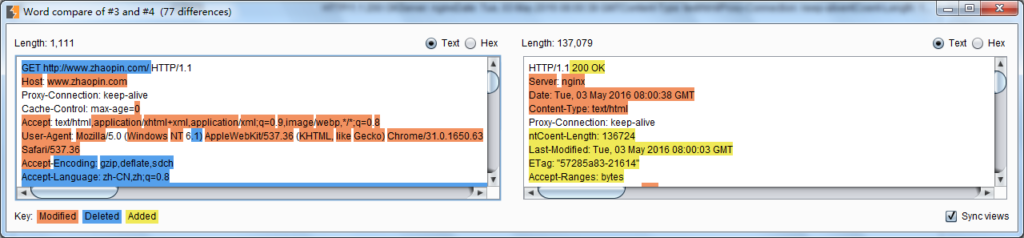
Among them, text comparison (words) refers to comparing the difference between two data through text, such as HTML; and byte comparison (bytes) refers to comparing twice through hexadecimal form. content differences. As shown in the picture below, pay attention to the color marking of different contents.