Decrypt WPA traffic in Wireshark
Let’s start with the theory to understand why the process of decrypting WiFi traffic in Wireshark requires some effort and why one cannot simply decrypt any captured WiFi traffic even if there is a password from the Access Point.
When transmitting over WiFi, the traffic is encrypted using PTK (the Pairwise transient key can be translated as a Pair of Transition Key). At the same time, PTK is dynamic, that is, it is created anew for each new connection. Thus, it turns out that WiFi traffic for each connection in the same Access Point is encrypted with different PTK, and even for one Client after reconnection, PTK changes. To calculate PTK, you need data from a four-stage handshake, as well as a password from a WiFi network (in fact, you also need other information, such as the network name (SSID), but obtaining this data is not a problem).
The main thing you need to understand: to decrypt WiFi traffic, you need a four-landmark handshake. And not any, but exactly the one that happened to transmit the traffic that needs to be decrypted. But to use the captured handshake you need a password from the WiFi network.
So, to decrypt WiFi traffic is needed:
- a handshake that occurred between the Client and the Access Point immediately prior to the exchange of decrypted information
- for this we need Monitor Mode WiFi adapter
- password to connect to the Access Point
Next will be shown two examples of capturing WiFi traffic and its decryption. The first data capture is performed using Airodump-ng , and then the wireless traffic will be decrypted in Wireshark. In the second example, the data will be captured and decrypted using only Wireshark .
Capture WiFi traffic using Airodump-ng
In order for the data to be suitable for decryption, it is necessary that the WiFi card does not switch channels, but to capture information on one channel on which the target Access Point operates. Therefore, we start by collecting information about the target access point.
We look at the names of wireless interfaces:
iw dev
We translate the INTERFACE into the monitor mode with commands like this:
sudo ip link set INTERFACE down
sudo iw INTERFACE set monitor control
sudo ip link set INTERFACE up
Change INTERFACE with your WiFi adapter name
Run airodump-ng with a command like:
sudo airodump-ng wlan0mon
For example, I want to capture and decrypt traffic for the Kali Access Point, which operates on channel 5.
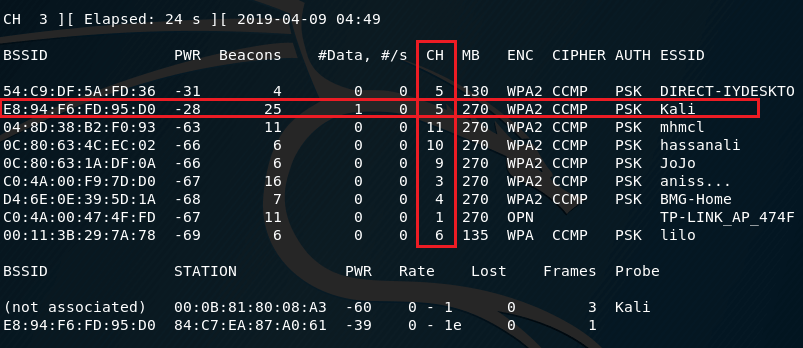
Then I need to restart airodump-ng with a command like this:
sudo airodump-ng wlan0mon --channel CHANNEL --write FILE NAME
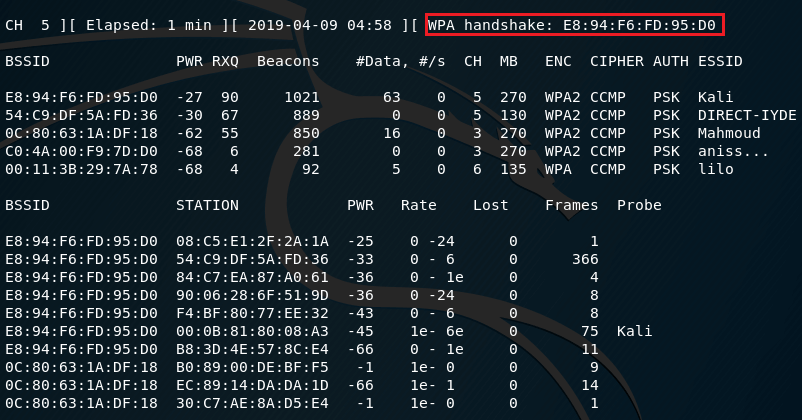
The WPA handshake inscription says that a four-stage handshake was captured. It means that:
- Now we can decrypt the WiFi data (if we have the key to the WiFi network)
- we can only decrypt data for a specific client (with which a handshake was made)
- we will be able to decrypt the data that was sent only after this captured handshake
Decryption of WiFi traffic using Wireshark
Open the capture file in Wireshark. In its original form, traffic looks like this:
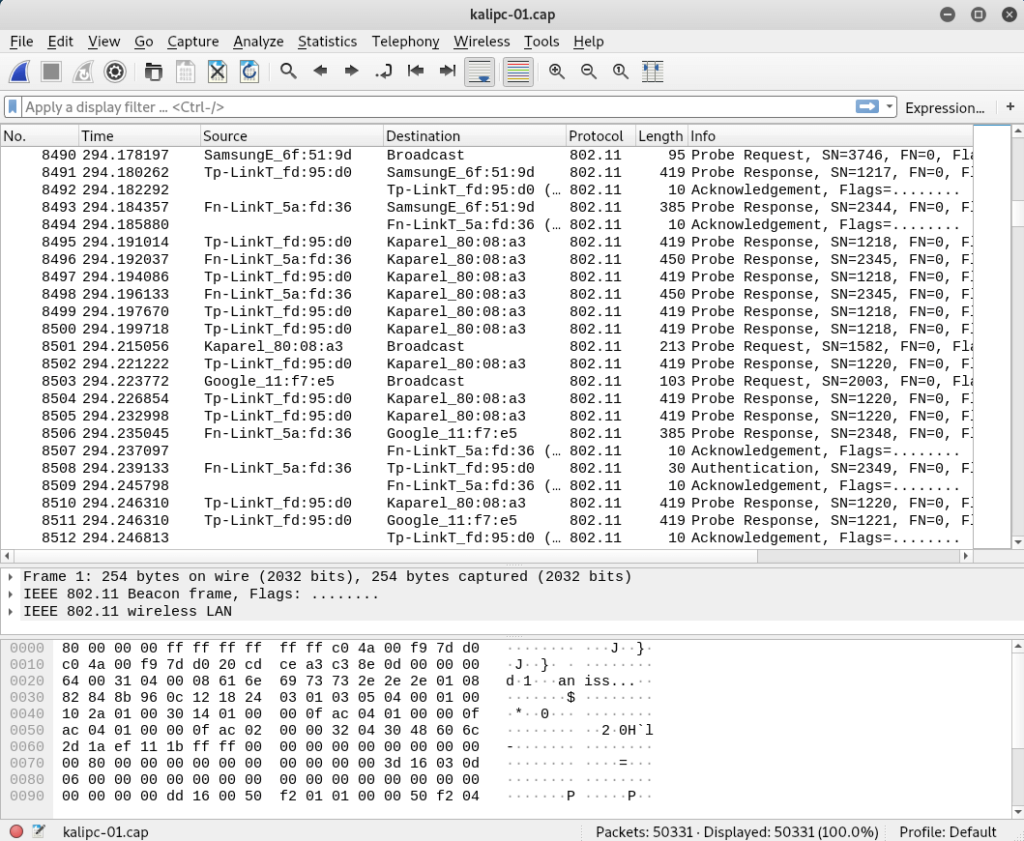
That is, without decryption, we see only the MAC addresses of the data transfer participants, some types of packets, as well as data packets — in which the payload is encrypted.Before decoding, make sure that there is a handshake, otherwise there is no point in continuing:
eapol
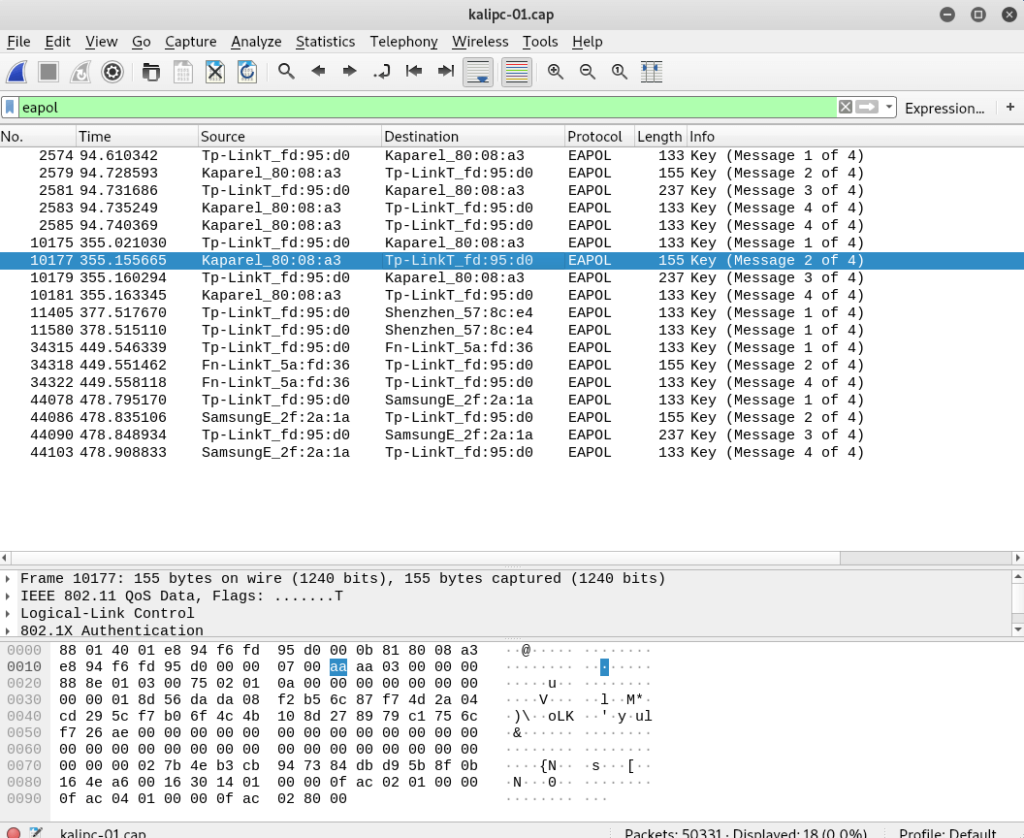
Before decoding, we need to make some changes in the IEEE 802.11 protocol settings.
Go to Edit → Preferences , expand the protocol section and select IEEE 802.11 . The settings should be:
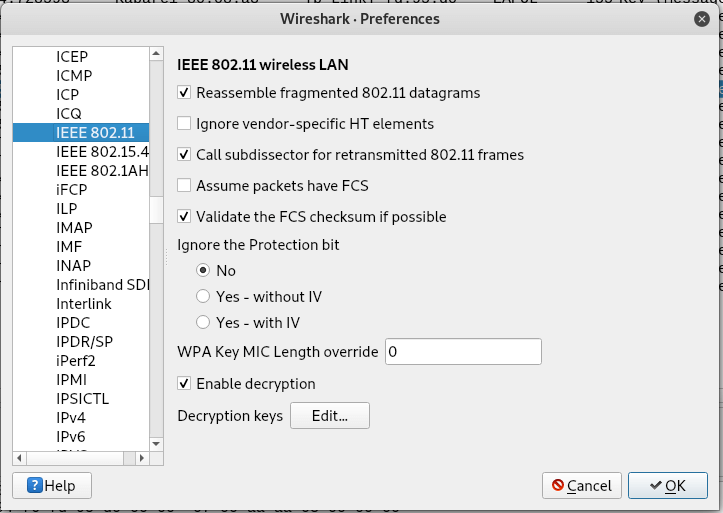
make sure you have the same settings as in the previous screenshot, click on the Edit button next to Decryption Keys (to add a WEP / WPA key):
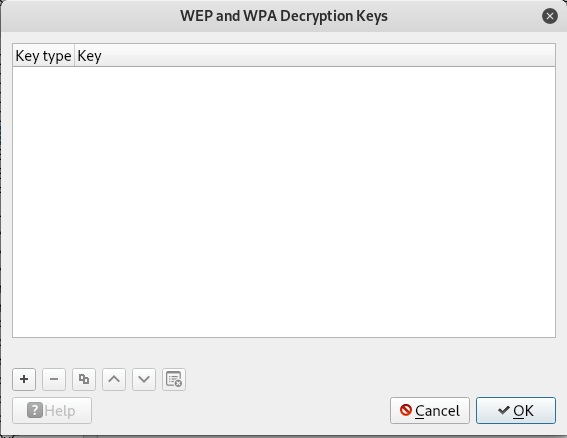
Click the Create button . In the window that opens, in the Key type field, select wpa-pwd , enter the password for the WiFi network, and after the colon, enter the network name (SSID) and click OK.
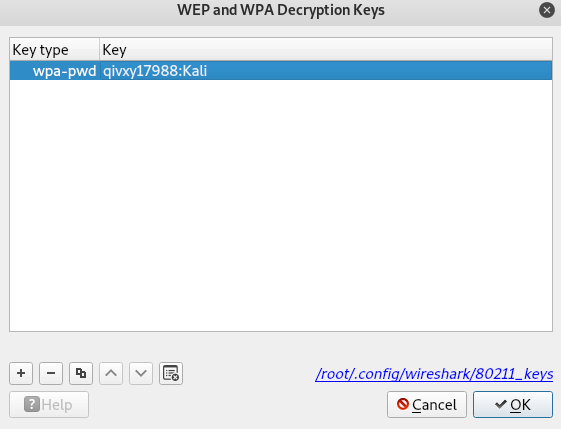
For example, in my case, the password is qivxy17988, and the network name is Kali, then I enter:
qivxy17988:Kali
Click Apply :
Traffic will be decrypted:
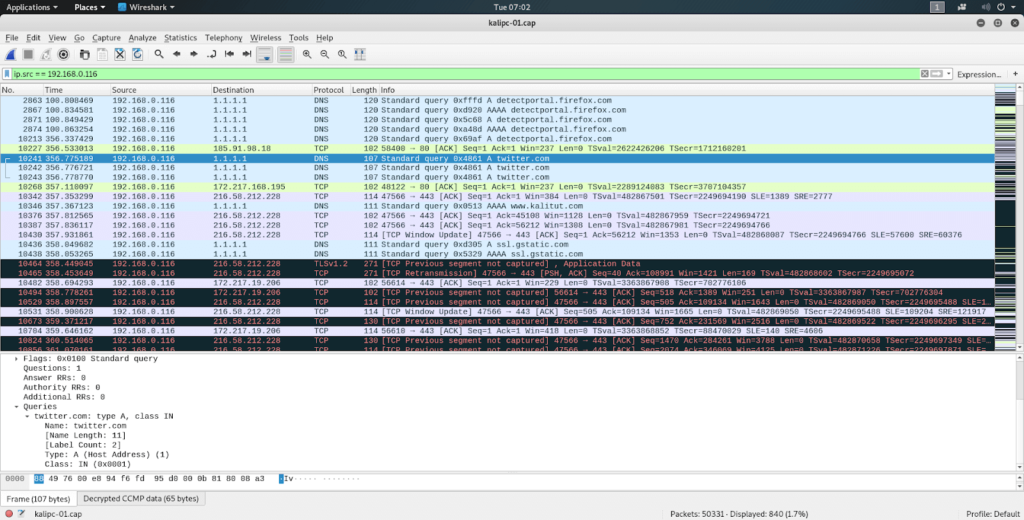
Now there are visible DNS, HTTP requests and responses, as well as other network packets.
If traffic is captured not only for this network, but also for other networks operating on the same channel, or for this network but other clients for which no handshakes are taken, then this traffic will not be decrypted.
Capture wifi traffic with wireshark
WiFi traffic can be captured directly in Wireshark.
But we first need to switch the WiFi card to the same channel as the target Access Point. This is done by commands like:
sudo ip link set INTERFACE down
sudo iw INTERFACE set monitor control
sudo ip link set INTERFACE up
sudo iw dev INTERFACE set channel
The subsequent decryption is performed in exactly the same way as shown above.
Conclusion
To decrypt WEP WiFi traffic, you only need to know the password.

Merci
Hi Naciri,
thank you for this tutorial. I tried to sniff half hour of my home wifi. Actually when I put the passphrase I could descript ip adresses.
But I was very sad to see that the IP addresses are the only information I can see. In fact I can’t see any URL or other plain text information. I also tried to navigate on http sites and I tried to use other devices but I couldn’t see nothing in plain on wireshark… Moreover I noticed that I couldn’t see any DNS or TCP messages in wireshark…
Is there any way to capture something interesting more than simple IP?