A WiFi router provides WiFis with their own IP configuration to several WiFi clients via its integrated access point. For this purpose, the WiFi router has a DHCP and DNS server.
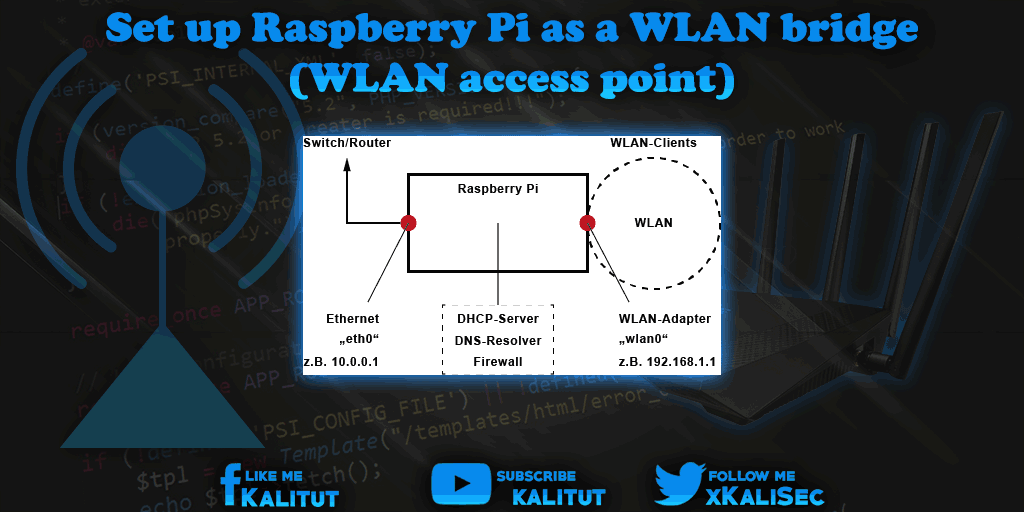
An alternative for this WiFi access point is a WiFi bridge. Here, Raspberry Pi serves only as a network bridge for two network segments. On one side the WiFi and on the other side the wired network.
task
- Determine which components and prerequisites are necessary for the operation of a WiFi router.
- Determine the necessary IP configuration.
- Set up the WiFi access point.
- Set up a DHCP server.
- Set up the router functions.
Note: Name of the network interfaces
Since Raspbian Stretch, the Ethernet and WiFi network interfaces have different names. So no longer “eth0” and “wlan0”, but “enx …” and “wlx …”. This concerns USB-connected network adapters whose names differ from the designations mentioned here. This means that one must first determine the individual name or change the naming to the old method.
Check requirements
To avoid setup problems, it is recommended to use a fresh Raspbian image. A Raspbian Jessie Lite is sufficient. In addition, you should make sure that the wireless adapter used with Raspberry Pi basically works and controls the access point mode. It works with the internal WiFi adapter in Raspberry Pi 3.
First of all, let’s see if the intended WiFi adapter is in AP mode. To check this, the wireless tools must be installed.
sudo apt-get install iw
iw list | grep AP
If this command ejects one or more lines with “AP”, then everything is in the green zone and the WiFi adapter dominates the access point mode. Then the WiFi adapter is suitable for our task. If not, then you should get another WiFi adapter.
Network Configuration
In Raspbian Jessie, a DHCP Client Daemon (DHCPCD) is enabled by default. The network configuration is done in the file ” /etc/dhcpcd.conf “. For a part of the configuration of the network bridge we use the file “/ etc / network / interfaces” here.
sudo nano /etc/network/interfaces
Here we enter the following lines:
# Localhost
car lo
iface lo inet loopback
# Ethernet
car eth0
iface eth0 inet manual
# WLAN interface
allow-hotplug wlan0
iface wlan0 inet static
address 192.168.1.1
netmask 255.255.255.0
In this IPv4 configuration, the WiFi interface has a static IPv4 address. We need this for the operation of the DHCP and DNS server.
It would also be conceivable to give the Ethernet interface a static IP configuration. This need not be. In this form, the WiFi router has the advantage that it works in any local area network when the IPv4 configuration is delivered via DHCP to the Ethernet interface. If IPv6 is enabled then it works as well.
Save and close with Ctrl + O, Return, Ctrl + X.
Now check whether the “dhcpcd” is active.
sudo systemctl status dhcpcd
If so, we add the following line to its configuration.
sudo nano /etc/dhcpcd.conf
denyinterfaces wlan0
After making the changes you can save and close the file: Ctrl + O, Return, Ctrl + X.
However, the changes have not yet been incorporated into the current network configuration. Basically, a reboot is recommended here, if you have made the configuration via SSH.
sudo reboot
Then we have to make sure that both the Ethernet interface (eth0) and the WiFi adapter (wlan0) are working and in place.
ip a
Both network interfaces (eth0 and wlan0) must be present and have an IPv4 configuration.
Update system
If Raspberry Pi and the Wi-Fi adapter meet all requirements, then we can get started. We start with the installation of the necessary software. Before that we do a system update.
sudo apt-get update
sudo apt-get upgrade
DHCP server and DNS cache setup (dnsmasq)
Next, we set up the DHCP server and DNS cache. The DHCP server ensures that the WiFi clients receive all necessary information for the IP configuration after logging on. The DNS service takes over the name resolution. Both take care of “dnsmasq”.
sudo apt-get install dnsmasq
After that we have to configure “dnsmasq”. To do this, we open the file “/etc/dnsmasq.conf”.
sudo nano /etc/dnsmasq.conf
There we enter the following lines as minimal configuration:
# DHCP server active for WLAN interface
interface = wlan0
# DHCP server not active for existing network
no-dhcp-interface = eth0
# IPv4 address range and lease time
dhcp-range = 192.168.1.100,192.168.1.150,24h
# DNS
dhcp-option = option: dns-server 192.168.1.1
Here the DHCP server and the DNS forwarding for the network interface “wlan0” is activated and for the interface “eth0” only DNS, but no DHCP is served. In addition, it is specified that in the WiFi, the IPv4 addresses are assigned from 192.168.1.100 to 192.168.1.150 for the clients and the address of the DNS server is specified.
Check DHCP server and DNS cache and put into operation (dnsmasq)
Before commissioning, it is recommended to test the configuration.
dnsmasq --test -C /etc/dnsmasq.conf
The syntax check should succeed with “OK”.
Restart DNSMASQ:
sudo systemctl restart dnsmasq
Show DNSMASQ status:
sudo systemctl status dnsmasq
Start DNSMASQ at system startup:
sudo systemctl enable dnsmasq
If you want, then you can log on to the WiFi AP again with a wireless client and check if you got an IPv4 configuration.
Set up wireless AP host (hostapd)
Then we install the host access point daemon, “hostapd” for short. This is a WiFi authenticator. He takes care of offering encrypted WiFi functions and the required authentication of the WiFi clients.
sudo apt-get install hostapd
After the installation, we set up “hostapd”, which operates the WiFi access point for the router.
The configuration of the wireless AP host:
sudo nano /etc/hostapd/hostapd.conf
The file should not exist yet and be empty. If the file does exist, then you should completely override it.
In the file we enter the following minimal configuration. Of course, there are even more parameters that are irrelevant in this case.
# Wireless router operation
# Interface and driver
interface = wlan0
# Driver = nl80211
# WLAN configuration
ssid = Wlanrouter
channel = 1
hw_mode = g
ieee80211n = 1
ieee80211d = 1
country_code = EN
wmm_enabled = 1
# Wi-Fi encryption
auth_algs = 1
wpa = 2
wpa_key_mgmt = WPA-PSK
rsn_pairwise = CCMP
wpa_passphrase = test test
Three settings have to be made individually. These are the WiFi name (“ssid”), the channel (“channel”), which can be freely configured from 1 to 13, but you do not have to change anything here. You may have to change the channel here, if a WiFi analysis shows that already several other WiFis occupy this channel. In principle, several WiFis can occupy the same channel. This is better than when the channels overlap.
- More information about WiFi frequencies and channels and the correct channel assignment
The third parameter is the WiFi password (“wpa_passphrase”). Here you should enter a password of at least 8 characters in clear text.
Note on the WiFi driver: There is the parameter “driver” in this configuration file, which is commented out (#). Normally “hostapd” automatically loads the correct driver. Of course, that does not work. Then you have to explicitly specify the correct driver here.
Then save and close with Ctrl + O, Return, Ctrl + X.
Because this file contains the WiFi password in plain text, only the user “root” should have read access to this file.
sudo chmod 600 /etc/hostapd/hostapd.conf
Do not worry, with the user “pi” you can change and save the file at any time.
Check WiFi-AP-Host configuration and put it into operation (hostpad)
Before we start setting up the WLAN router, we first put the WiFi host into operation. Only if that works, worth the further steps. If the WiFi host does not work, you do not even need to set up the router functions.
To start up the WiFi host, we start “hostapd” in debug mode. We will see “all” error messages.
sudo hostapd -dd /etc/hostapd/hostapd.conf
Note: With “Ctrl + C” you can stop the running hostapd instance if necessary.
“hostapd” will produce messages in any case. If the configuration is correct and the WiFi adapter plays along, the configuration runs through. The program will not be finished. That is, “hostapd” does not return for command input. If the following messages appear, then everything is in the green area:
wlan0: interface state COUNTRY_UPDATE-> ENABLED
wlan0: AP-ENABLED
This is a good opportunity to test the WiFi AP. For this one tries with a WiFi client to find the WiFi and log in there.
In the command line, you can observe how the WiFi client logs in (AP-STA-CONNECTED) and also logs it out again (AP-STA-DISCONNECTED) when it ends the connection to the WiFi.
Note: If you make the configuration via SSH, then you should make the testing of the wireless AP with another client, otherwise you shoot yourself by changing the wireless network, the SSH connection.
If “hostapd” aborts with error messages and returns to command input, then something is wrong. However, the errors are extremely diverse and the associated error messages are not always clear. A popular error is the missing “sudo” when calling “hostapd”.
Other sources of error can be ruled out if you make sure that the wireless adapter works in principle and mastered the AP mode.
Another source of error is the distribution used. It will work in any case with the original Raspbian.
For the “hostapd” to start as a daemon in the background, you have to tell the daemon where to find its configuration.
If “hostapd” is still running, then we end it with “Ctrl + C”. Then we open a configuration file:
sudo nano /etc/default/hostapd
In it we add the following parameters:
RUN_DAEMON = yes
DAEMON_CONF = "/etc/hostapd/hostapd.conf"
Then save and close with Ctrl + O, Return, Ctrl + X.
The “hostapd” is then put into operation with the following command.
sudo systemctl start hostapd
sudo systemctl enable hostapd
The status of the daemon can be checked with the following command.
sudo systemctl status hostapd
Router and firewall configuration for the Internet connection
Up to this point, one has in the best case a connection to the WiFi and an IPv4 configuration received. What does not work yet is a connection to the internet. That’s what we care about now.
For this we supplement the network settings.
sudo nano /etc/network/interfaces
Here you add the following lines to the already existing configuration:
# Delete existing firewall rule
up /sbin/iptables -F
up /sbin/iptables -X
up /sbin/iptables -t nat -F
# Allow loopback
up /sbin/iptables -A INPUT -i lo -j ACCEPT
up /sbin/iptables -A OUTPUT -o lo -j ACCEPT
# Enable NAT and Masquerading
up /sbin/iptables -A FORWARD -o eth0 -i wlan0 -m conntrack -ctstate NEW -j ACCEPT
up /sbin/iptables -A FORWARD -m conntrack -ctstate ESTABLISHED, RELATED -j ACCEPT
up /sbin/iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
# Enable IP forwarding
up sysctl -w net.ipv4.ip_forward = 1
up sysctl -w net.ipv6.conf.all.forwarding = 1
# restart hostapd and dnsmasq
up service hostapd restart
up service dnsmasq restart
NAT, masquerading and IP forwarding are activated here. Both are important router functions.
Then the services “hostapd” and “dnsmasq” are restarted.
Then you have to save and close the file: Ctrl + O, Return, Ctrl + X.
A restart of Raspberry Pi is finally required.
sudo reboot
Check WiFi, router and DHCP / DNS function
If Raspberry Pi is restarted, you should check whether the services “hostapd” and “dnsmasq” run before you log on to the newly established wireless router.
sudo systemctl status hostapd
ps ax | grep hostapd
sudo systemctl status dnsmasq
ps ax | grep dnsmasq
If the services are running and the processes for the two services are displayed, then you can try to log in to the WiFi router with a WiFi client and set up an Internet connection.
Note about Raspberry Pi as a WiFi router
No matter which solution, as a WiFi access point, Raspberry Pi is not suitable for its interface performance. The facility is error prone, cumbersome and may not be safe. Apart from that, the Raspberry Pi with the necessary equipment is more expensive than a wireless router. If you seriously and permanently want to operate a wireless access point, you should take a look at OpenWRT and get a cheap compatible router to do so. Price, but also from the comfort is much more interesting.
Safety instructions
Anyone who sets up and starts up their own network components also takes responsibility for this. With this solution, you can possibly shoot yourself in the knee. If you think that the solution presented here is finished, then that is a mistake. If you do not take any extra security measures, then you break yourself with this wireless router a security hole in the local network.
Please observe the safety instructions for operating a WiFi access point.

Leave a Reply