Most modern devices remember the name of the WiFi network to which they successfully connected at least once, and immediately connect to it if they “see” it in wireless. This feature of wireless technology is increasingly being used by attackers – they create so-called rogue AP (fake access point).
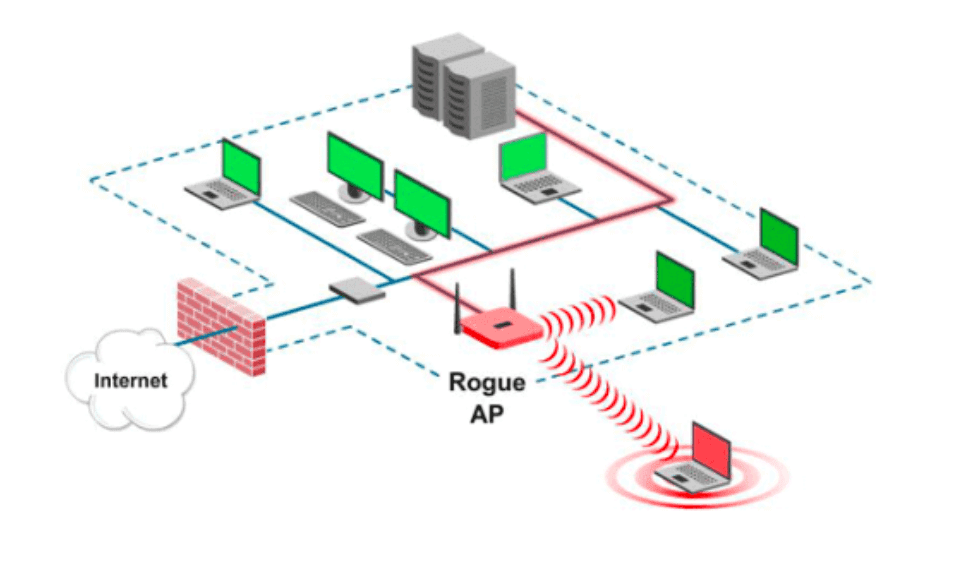
Such attacks are becoming more and more large every year, taking into account the ever-increasing market for BYOD devices and the amount of critical information contained in them.
Fake wifi
When setting up the wireless adapter to automatically connect to well-known wireless networks, the user exposes himself to the risk of falling victim to man-in-the-middle attacks. An attacker can create a trusted WiFi access point. As a result, the client device will automatically connect to such an access point and will work through it, and the attacker will be able to intercept the “entire traffic” of his victim, or attack the device that is with him on the same network segment.
To detect access points, a device equipped with a WiFi module scans the radio for the presence of Beacon frames transmitted by the access point, which contain an indication of a known SSID. Probe Request broadcast frames are sent across all channels, awaiting the response of a known access point. The Probe-Request frames may or may not indicate the SSID of the network that the mobile device is looking for. Responding to the Probe-Request, the access point sends Probe Response frames containing similar information as the Beacon packets.
Relying on the received data, such as the network name, signal-to-noise ratio, supported 802.11 standards, the device makes its decision to connect to one of the available known networks (access points).
The attacker’s task is to “raise” a clone of the network, to which the potential victim can be configured to access (both with wired and without). Also, if there is a legitimate access point nearby, an attacker can try to “extinguish” it in order to redirect clients to their access point.
Examples of fake access points:
- name and / or model of the router: DIR-300, ASUS;
- default name: default,% provider_name%;
- Free WiFi: MosMetro_Free, Beeline_Free_Wi-Fi;
- access points stitched by the operator: attwifi;
- access points of various establishments:% airport_name_free%, McDonalds_WiFi_Free;
- access points with no encryption: h0lyava, MaminHackir, blondinka.
After successfully connecting to the access point, the attacker implements one or more attack vectors, including using social engineering tactics:
- “Classic” Man in the Middle attacks, data interception;
- “Complex” Man in the Middle attacks – sslstrip, HSTS bypass and SSL pinning, etc .;
- traffic modification (URL and content spoofing);
- access page to the router / web panel to enter the password, captive-portal;
- fake Radius to intercept MS-CHAPv2 hashes (many users easily “accept” a fake or untrusted certificate);
- direct attacks on devices in one network segment.
Fake access points Attack examples
Employees of Avast on the eve of the international exhibition Mobile World Congress 2016 conducted a kind of experiment. The day before the opening, several Wi-Fi access points with SSID-identifiers Starbucks, Airport_Free_Wifi_AENA and MWC Free WiFi were deployed at the Barcelona airport. Avast’s goal was to demonstrate how users put themselves at risk when using public Wi-Fi points.
In just four hours, Avast experts intercepted more than 8 million data packets from more than two thousand users. To preserve the privacy of users, all data was immediately deleted. The company managed to collect the following statistics during the experiment:
- 50.1% of users used the Apple device, 43.4% – a gadget running Android, 6.5% – devices with Windows Phone;
- 61.7% of exhibition visitors searched Google and checked their Gmail mail;
- 14.9% used Yahoo search;
- Facebook application was installed on 52.3% of devices, and Twitter was less popular – only 2.4%.
According to experts, many people know that an open WiFi network is fraught with danger, but nevertheless continue to use them. The success of the experiment is also due to the fact that many airports are roaming and cannot use the mobile Internet, so they are trying to find free networks.
Often users are attacked the most common networks of hooliganism:
Hackers hacked the free WiFi network of the Moscow metro around 11:30. As a result of hooliganism, thousands of passengers saw porn on the screens of their phones and tablets instead of the usual start page and an invitation to enter the network.
When connecting to the WIFI network, as it became known to REN TV journalists, an obscene inscription appeared on the mobile phones of the passengers: “Go to x … bits and buckets! X … you, not the Internet. “
MaksimaTelecom spokesman Ilya Grabovsky said that the possibility of hacking their network is out of the question. According to him, one of the passengers created a WI-FI network without access to the Internet, called it a similar name. Grabovsky noted that some of the citizens had mistakenly connected to this network.
Tools
To date, there are quite a few utilities for conducting such attacks, below is a brief description of the most popular of them.
Important: the use of some of them may be prohibited by law and prosecuted.
Mdk3 is a utility that contains several client deauthentication technologies and an access point attack technician, leading to its “hanging” (DoS) or rebooting.
Mana toolkit is a modified hostapd (software access point) and several scripts that allow you to create and use fake access points: KARMA- attack; various types of MitM attacks; HSTS bypass; cookies capture; intercept EAP.
Wifi phisher – designed for phishing attacks on WiFi networks in order to obtain passwords from the access point and other personal information. This tool is based on the attack of social engineering.
Wifi pumpkin – the tool creates a fake Wi-Fi access point, while affecting the legitimate access point (disables clients). It can be used to capture credentials using Man in the Middle attacks, also uses such attacks as (including social): DHCP Starvation; phishing; Windows Update; HSTS bypass; transparent proxy, etc.
Linset is a utility that combines a fake access point and a socio-technical component. The tool is interesting, but requires some improvements.
Bdfproxy – the tool allows to modify binary files “on the fly”, for example, for the introduction of malicious functionality or backdoors. The functionality works fine with all sorts of update-services that deliver updates in the form of executable files.
Waidps – a tool for detecting attacks in Wi-Fi networks. It is a multipurpose tool designed to audit networks, detect wireless intrusion (WEP / WPA / WPS attacks), and also prevent intrusion (stop communication of a station with an access point). In addition, the program collects all information about the surrounding Wi-Fi networks and stores in the database.

Love