Man in the Middle Attack (MITM) is a long-standing network intrusion method, and there is still a wide range of development space today . Attacks such as SMB session hijacking and DNS spoofing are typical MITM attacks. In short, the so-called MITM attack is to intercept normal network communication data, and tamper with and sniff the data , but both parties of the communication are unaware.
With the continuous development of computer communication network technology, MITM attacks are becoming more and more diverse. Initially, as long as the attacker puts the network card into promiscuous mode and pretends to be a proxy server listening to specific traffic, the attack can be implemented, because many communication protocols are transmitted in plain text, such as HTTP, FTP, Telnet, etc. Later, as switches replaced hubs, simple sniffing attacks were no longer successful, and ARP spoofing was necessary. Today, more and more service providers (online banking, E-mail) began to use encrypted communication, SSL (Secure Sockets Layer) is a widely used technique, HTTPS, FTPS are all built on the basis of its
What is man in the middle attack?
Man in the middle attack are methods (which have been discussed since 1995), in which the attacker latches into a communication link, and then sits in the middle between the two communication endpoints. Previously, when data communication was still done via leased lines, this meant that the attacker would interrupt the line, hang in between, and thus be able to see and change all transmitted data. Today it is easier.
This physical placement between the two communication endpoints is no longer necessary with networking on the Internet and because of the philosophy behind the Internet that the data itself finds its way to the opposite point. The attacker only needs to change the signposts that the data packages use to find their way, i.e. he makes sure that the data packets come to him after he has looked at them or changed them, he redirects them to the endpoint.
This is the basis of all modern man in the middle attack.
This article combines several topics, namely the technical background to man in the middle attack and the purposes to which they are then used. These purposes range from interception activities of the intelligence services , to the interception of access data by users from public WLANs to the large area of electronic bank robbery, which used to be purely phishing attacks, but have been widely used since SMS TAN of man in the middle attack,
MITM can be used not only for financial gain. Because of the increasing importance of the Internet as well as for politics, governments are increasingly taking advantage of the fact that their citizens are also being read. The NYT reported in August 2011 that Iran apparently has falsified Google Web certificates and therefore can read the data traffic to Gmail. But not only Google was affected by these attacks.
A good example of a political man in the middle attack is documented in a study on the intrusion of Diginotar. There, false SSL certificates and a “bend” of the DNS resolution were used for an attack against Iranian internet surfers. At 300,000, it can be shown that they were surfing via the man-in-the-middle access. The Iranian government got access to all email accounts of the users of Gmail and other web mailer.
And not just the Iranian government: documents from Snowden on the NSA issue show how the NSA performs exactly the same (or the Diginotar problems themselves): NSA Mimics Google to Monitor “Target” Web Users. These are probably fake SSL certificates used (see also illustration right). More details can be found in the second part of the Brazilian video NSA Documents Show United States Spied Brazilian Oil Giant in which pictures from the NSA powerpoints are shown.
Type of man in the middle attack
Attacks must be scalable for the attacker
There are quite different forms of attack around the man in the middle concept. It is important for the attacker that “the attack scales”. This means that the attack can be automated and executed as on the assembly line (exception: a government wants to monitor 1 certain locations). An example of scaling: It is not very difficult to figure out the date of birth of a certain person using social engineering techniques. However, such an attack does not “scale”, it can not be used massively and automatically.
Another example: In 2006 I had written that mobile phones with some effort listener can be. But this is always only in the vicinity of the handheld, not covering the area (differently, if the authorities with the mobile phone provider the lines tap, the scaled of course very well). This technology has now made the technology obsolete. More and more bank customers have smartphones and the infecting of a smartphone, especially if it is based on Android and the customer eagerly installed apps, 2011 is no longer a problem at all. This allows SMS TANs to be intercepted very nicely.
When assessing such protective measures, it is important to take into account that any protective measures can be leveled out at any high cost (if necessary, someone can be bribed), but if the protection measure achieves that the attack is not “scaled”, this is usually in the Internet banking is sufficient.
April 2006: heise.de reports about a gang in Germany, who worked on bank trojan (ie man-in-the-middle on the computer of the customer) and in this way spied on PIN and TAN.
July 2006: the first attack by Trojans in Austria. Details on ARGE data. It is still unclear how the Trojan came to the affected computer, but the program waits for the user to connect with Raiffeisen, Erste / Sparkassen or Bawag / PSK. Then it exchanges individual parts of the displayed websites (frames), leaves the framework intact. This means that the user still sees the closed padlock and the certificate is also the real one. The customer can notice the attack by promptly requesting 4 TANs. (If a website uses frames, it can not be guaranteed that all parts of the website are genuine).
ARGE data reported that the attackers were professional: since the end of June, Austria has been massively flooded with emails, in which easy activity and high profit for simple financial management was promised. It is about the fact that the phishers first want to make sure that they have found enough “fools” for money laundering, which must bleed for them (and go to jail if necessary)
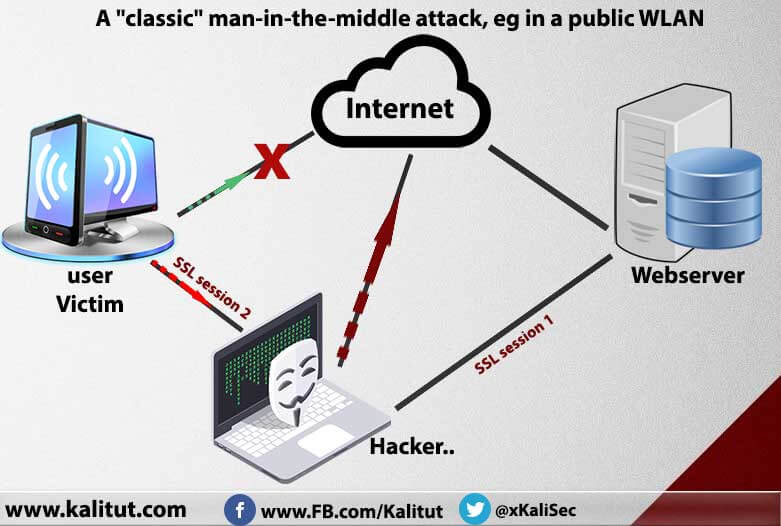
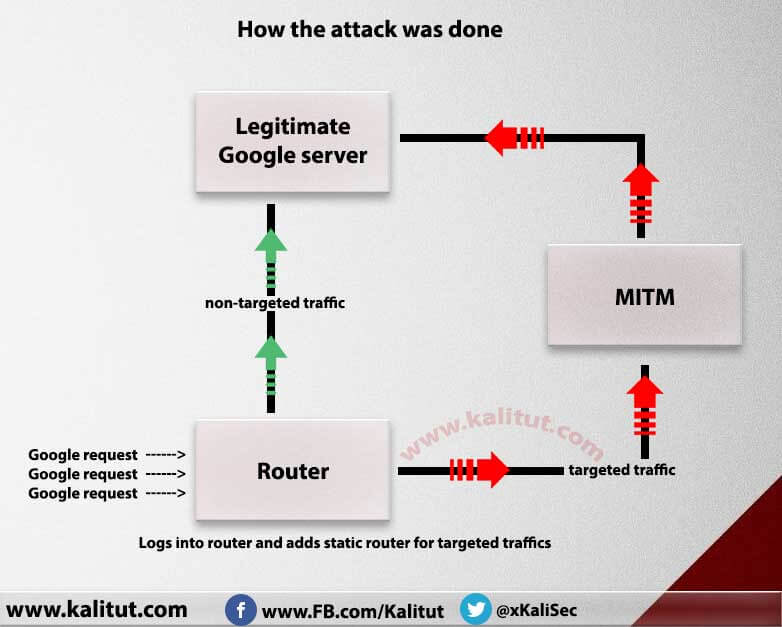
Such an attack as shown on the left is transparent to the bank and to the user. The customer sees (almost) the same screens as always because he is connected to the correct website – but if he is attentive, he will see that the certificate of the website is wrong, because the attacker can not imitate so easily. The attacker can intervene very selectively in the interaction of the customer with the website and very specifically change data, eg amount and account number of a transfer.
Such an attack is difficult to thwart because whatever the bank passes to the customer as an inspection question (authorization), the attacker gets the correct answer from the customer and simply passes it on. For example, the bank asks for the password, the man-in-the-middle forwards the question to the user, the password is entered, and the man-in-the-middle acknowledges and sends it further. This is also possible with complex authentication, eg one-time passwords, which are constantly changing (eg via so-called tokens).
This also works via so-called secure SSL connections. For SSL, as it is usually used today, only 1 digit, ie the server with its certificate, is authenticated. Because the theoretically possible client certificates are virtually non-existent, the server does not matter who is the opposite. In an SSL connection, the attacker simply presents the user to the web server, and the user plays the web server to the user. This is what is usually called a proxy function. This means that the attacker builds an encrypted SSL connection from his computer to the web server and another encrypted connection from himself to the user. The user then plays an incorrect SSL certificate. In between, the man-in-the-middle has the information in the plain text. Such invalid certificates can be easily created by any attacker, but then these are self-signed, so no one vouches for the correctness. Or he can issue the certificate from one of the certification agencies (CA) who does not require any supporting documents, except that the customer pays a small fee.
The user can discover this attack because the attacker is not able to present the correct certificate. The risk is the attacker because the chance that the user is looking at the certificate is unfortunately low (which Internet user knows how to check a certificate ?). This link also contains examples of how phishers have managed to make valid certificates from more or less well-known providers.
Possibly. it sounds like it is difficult to carry out such an attack. But there are already phishing kits that make it easy to redirect an e-banking session (eg, Rock Phish) . Here is an example of one of these attack techniques in detail: Citibank Phish Spoofs 2-Factor Authentication and that already in July 2006.
The Swiss Reporting and Analysis Center for Information Assurance (Melani) reported. “Classic” enter phishing attacks via e-mail with the invitation passwords, have declined sharply in Switzerland In addition, all were unsuccessful For successful attacks using malware have increased… Two- Factor authentication systems (eg, strike lists, SecurID, etc.) do not provide protection against such attacks and must be considered unsafe as soon as the customer’s PC has been infected with malware “.
They report incidents in which such a malicious program is embedded in the browser and manipulated there before the encrypted transmission of the transfer data name and account number of the recipient and also the amount. Even the confirmation of the bank is intercepted and displayed incorrectly. They report that the infection is very simple: “As a path of infection, web sites that visit malware are installed on the computer (drive-by infection) without the user’s intervention, resulting in security gaps in the operating system, browser, or other “The detection rate of the malware through anti-virus software remains deep.”
Also, many of the phishing attacks on e-mails that are forwarded to fake sites are man-in-the-middle attacks, namely, when they pass on the correct website after entering the wrong information.
Another phishing attack is through Google. Today, there are travel portals, which are not at all. They offer extremely cheap flights, but ultimately it is about the moment when the customer enters the credit card number and possibly other sensitive information. Such a fake website can display current flights without any hassle, even the search engines can display current flights, the operator of the fake website simply has to forward the queries to a real travel portal and then forward the answers from there. After the customer has entered the credit card then simply an error message can be issued and thus the dialog can be canceled. But I also heard of an attack that even got a ticket by post from a legitimate provider, but with an additional bill.
In order to logically bind a web browser and a web server, there are many techniques. The technical attacks described in the following describe how an agent switches on in the communication channel. Another technique is described below, with the middleman sitting on the customer’s PC .
The course of such a man-in-the-middle (MITM) attack when the transfer is secured by mobile phone TAN:
- the customer connects to the bank, but is redirected via the MITM computer, which decrypts the entire SSL data traffic, modifies it if necessary, and then sends it back encrypted to the bank. Likewise, all responses are decrypted by the bank, modified as required and then encrypted again to the customer. Authentication via one-time password succeeded without problems, for which did not even need a change of the data to be carried out.
- the customer now encounters a transfer, enters the amount, the BLZ and the account number. The attack in the middle changes the amount and the account information and passes this modified transfer to the bank
- the bank uses a very modern procedure, so the bank generates a random number and forwards it to the customer’s mobile phone (mobile phone TAN or mTAN).
- the attacker can not intercept the mobile TAN, but he can intercept the account information for the screen and restore it back to the original values of the customer. This means that the customer sees from the bank a confirmation window with the information which he has entered, but which is not the information that the bank has received.
- the customer sees that the confirmation window is correct and enters the cell phone TAN which the attacker forwards, but only after returning the account information to the wrong value
However, secure protection is also possible here if the bank sends the transfer data, ie the account information of the recipient account back to the customer for confirmation by means of the mobile phone TAN (“out-of-band transmission”) and the customer looks at it Customer sees the wrong amount and the account number of the bureaucrat and breaks the interaction with the bank.
Man in the Middle attacks on HTTPS connections
In the following text, I describe how the attacker manages to “logically” into the Internet connection. This is only half the attack – after that, the attacker has to reckon that it has to do with an encrypted HTTPS connection. In this case, it can appear against the web server as a client and against the web browser as a web server. The challenge with HTTPS connections is that the browser checks whether the certificate presented by the attacker against the browser is included in the list of trusted certification authorities (CAs). If so, there is no warning. If it is a self-signed certificate issued by the attacker itself, the user gets a warning that the website is uncertain. At this point, according to studies,
Attackers sometimes solve this challenge by hacking a CA, as has happened since 2011. For example, an attacker could issue certificates in the name of Google, Microsoft, and Facebook, and the Iranian government authorities were able to read the data traffic of probably more than one million citizens, save the passwords, and access their emails,
A simpler method is SSL stripping. In doing so, the attacker does not bother to make an HTTPS connection to the user, he simply directs traffic through HTTP and trusts that users will not notice that the URL line does not look as usual. This attack can be thwarted if the website uses HSTS to inform the browser that their content will never be accessed via HTTP, but this is still extremely rare today.
Elsewhere, I describe the fundamental weaknesses in the HTTPS ecosystem.
Man in the Middle technical attacks on the net
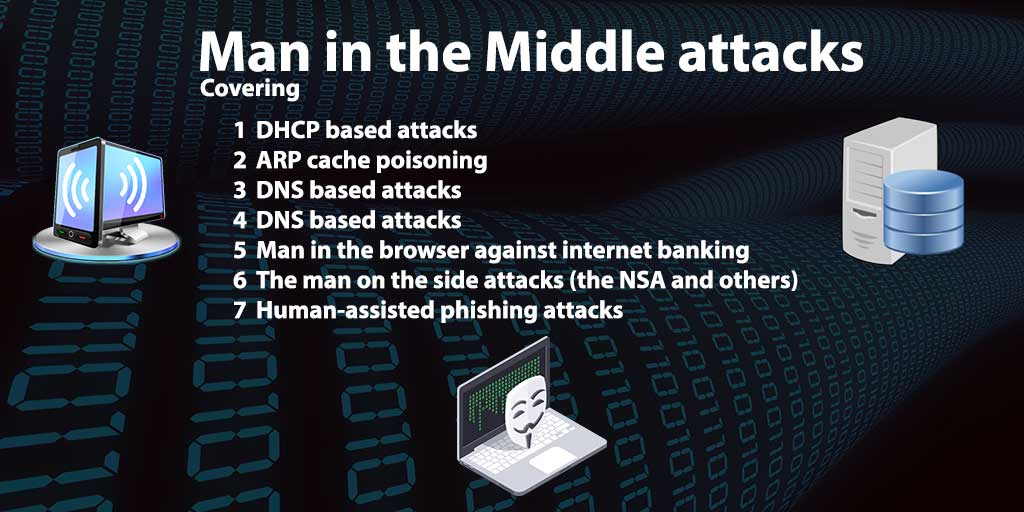
To understand other techniques, you need to know how a web browser actually finds the web server. Let’s take a concrete example: someone is connected to the Internet via a telephone modem, cable modem or xDSL / ADSL via an Internet provider (ISP). If the user enters an address in the web browser, for example, www.orf.at, the web browser looks up under which numerical IP address this web server can be found. To do this, he queries a DNS server. Where the DNS server is to be found, it has previously been told by the DHCP server of the provider. [The DHCP server provides more information to the user’s PC when he logs in. He gives him a (possibly temporary) IP address for this session, under which other IP address the access to the Internet is to be found (gateway address) and under which address the DNS server is located]. The DNS server is then, the “www.orf.at” can translate into a numeric IP address. This means we already have a whole series of points of view because all these signposts can be adjusted.
DHCP based attacks
The next method would be to play DHCP servers, which is very easy in a cable network (eg in a hotel LAN)- WIRELESS INTERNET ACCESS). The customer’s computer queries in the local network via a so-called broadcast, if someone could give him an IP address. The DHCP server that responds the fastest is accepted by the computer. This means that if the wrong DHCP server specifies the wrong way to the Internet (gateway address), the customer’s computer sends all Internet requests to this wrong address. The computer, which is there, can then read, change and distribute the data. Or the attacker lies with the DHCP response when it comes to the DNS server. The attacker gives the customer a DNS server, which he controls himself. Then it can provide the web browser with incorrect IP addresses. All these attacks assume that I am on the same local network as the victim, which is given in cable lanes, hotel LANs and also public WLAN hotspots.
Instead of playing an incorrect DNS server, an attacker can also exchange the “hosts” file on a computer. For this, he must enter the computer, either via a vulnerability or via a virus e-mail. The computer of the Internet user checks, before asking a DNS server, first times this hosts file and also there can already a redirection happen.
An example for the execution of this attack is the so-called drive by pharming, for which finished software is available. The attacker lures the victim to a website that has a javascript attempting to access the wireless access point, router or switch for that home network. The program knows the default passwords for Linksys, D-Link, and NETGEAR and changes the DNS entry there. This means that the attacker can now redirect the Internet traffic of the victim to his own server. The paper: Drive-By Pharming. The answer is, of course, quite easy: change passwords, of course, immediately during the installation.
arp cache poisoning attack
This is a man in the middle attack, known since 2001. The attack uses the Address Resolution Protocol (ARP) and works by routing the other devices on the network to Layer 2, which would be the WLAN access point or gateway to the Internet (in the case of cable networks). For this purpose, the attacker sends suitable ARP packets to devices on the local network (so-called gratuitous ARP). Affected devices then believe that the way to the Internet leads over the attacker. This then redirects the traffic to the real gateway so that the normal functionality is maintained. As with the previous attack, the entire data flow can be read and changed. Programs for this attack are available on the Internet.
In 2012, the whole thing becomes much easier: With the espionage software “WhatsApp Sniffer”, unauthorized persons can view the entire WhatsApp-bound data traffic: sent and received text messages, pictures and videos. This is particularly easy when users communicate via publicly accessible WLANs, such as railway stations, airports or cafés. “WhatsApp Sniffer” on Android redirects all network traffic in the local network through ARP spoofing through the smartphone and analyzes it for WhatsApp messages. This is similar to the app “DroidSheep”, with which one can hijack sessions of Facebook and other web services.
DNS based attacks
A similar attack will take place regularly in the course of 2013: Data traffic redirects on the main roads of the Internet carried out through incorrect BGP (Border Gateway Protocol) announcements. Internal-American data traffic was conducted via Belarus or Iceland and the unencrypted shares were analyzed there. The background is unclear, here further links.
An attack that has been running since mid-March until today (mid-April) is based on DNS cache poisoning, Because of vulnerabilities of DNS servers accesses to individual websites and sometimes even top-level domains such as .com are redirected to an incorrect server. This then redirects the traffic to the correct web server, the customer notes nothing except a delay. Currently, the attack is mainly used to transfer the customer’s computer to pay-per-click websites, such as Google Adwords. But this can also be used to redirect and exploit connections to Internet banks. The customer has no real possibility to protect themselves against it and also the selected web server can not defend itself, the attack takes place in the infrastructure of the Internet instead. The attacks could be prevented if all operators of DNS servers would bring them up to date.
Here the documentation of man-in-the-middle attacks in the anonymisation network TOR (before its use therefore rather discouraged, experts recommend JAP and AN.ON The author has discovered the attacks with a clever trick, he has his own SSL- I’m not sure if this is the case, but I’m not sure if it’s possible to use an SSL proxy, but I’m not sure if it’s true Certificate so you can discover such attacks, as described here, by checking the SSL certificate (like that goes above, and more about TOR and Onion Routing writes Bruce Schneier.
Pretending the wrong WLAN access point
This is a man-in-the-middle attack on the air interface of WLAN, usually in a public WLAN. The attacker simulates an additional access point with a misleading SSID (see below) and possibly better signal quality. He waits for the customers of the WLAN to log on to him and not to the real access point. It can then forward the traffic to the real access point, so that for the victims the impression of a normal connection arises. If the real access point requires an authentication, the attacker also gets the user names and passwords in this way. In this way, the attacker can listen to all traffic or perform other attacks, such as phishing.
Software for such attacks is today very easily available, here is a guide for a small device called Pineapple. From this article, I learned that WLAN-enabled devices, such as smartphones, constantly “reheat” all SSID of their previous connection. The Pineapple then simulates exactly this SSID and the device of the victim connects itself automatically.
Man in the browser against internet banking
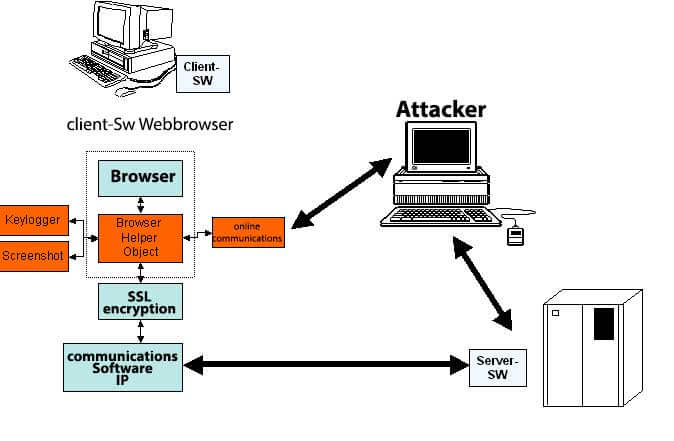
This is a special variant, which becomes more and more important and the other methods have already almost displaced {because it is so simple to infect a not completely updated computer is unfortunately very simple :-(} In this case the communication is already in the PC is either intercepted or modified in the communication software, or in the web browser, when the PC is infected by malicious software (which is, unfortunately, true for a very large number of home PCs, estimates are up to 30% – stands elsewhere, how this infection of the PC is carried out).
In this case, the conventional protection methods (see next chapter) do not interfere with encryption with SSL, since the monitoring and the changes are already carried out before the encryption software becomes active at all. Against this form of attack only helps to prevent the infection by suitable measures. In addition, the protective measures described below apply.
The man on the side attacks (the NSA and others)
Man-on-the-Side is a special variant of attacks used by the NSA as part of its QUANTUM activities – used in cases where they do not want to directly enter the data traffic as a man-in-the-middle. This variant has the advantage that the user does not see any delays in the data traffic because the is not interrupted, but only “supplemented”. This is done by packet injection.
After the NSA is able to tap more or less arbitrarily the nodes on the Internet, they have set up computers at these nodes, which belong to the so-called QUANTUM program. The program is quite clever and is suitable not only for listening but also for taking over the target computers.
The so-called QUANTUM computer of the NSA stands “beside” the data stream, ie it does not interrupt it like in a man-in-the-middle attack, it inserts additional data packets into the data stream from the legitimate website to the browser of the victim. This can be, for example, additional HTML code, which directs the browser to other websites.
2015, it is known that the NSAs are not the only ones to use packet-injection or man-on-the-side attacks . Bruce Schneier writes about it under the Democratization of Cyberattack – any more advanced government can do this, and for the others, for example, hacking team offers something to buy. He also mentions that the SS7 monitoring technology is also available for purchase worldwide. Any dictator can monitor his citizens or the Mafioso his competitors. Bruce Schneier’s point: Vulnerabilities that are installed somewhere at the request of the NSA are then used by other attackers, we become all insecure.
China does not have to buy something like this, they have developed the Great Cannon of China. It is grid-related near the Great Firewall of China and “sees all traffic to China in and want to get out of China. Unlike the firewall will not block here, but as with QUANTUM NSA, data is inserted. The tool used was in March 2015 denial of service tool against sites in the US (see Man-on-the-side attacks from China on GitHub ), but just can also very easily become infected in this way PCs.
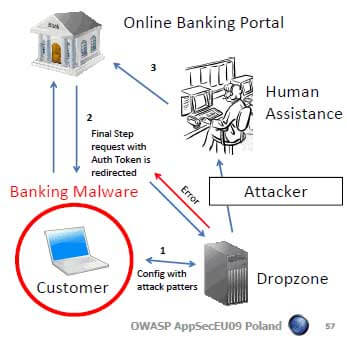
“Human-assisted” attack Dropzone refers to the server on which the data stolen from the computer of the victim is stored. Source: OWASP EU09 Poland The bank in the browser
Human assisted phishing attack
A method that is increasingly used in phishing attacks since 2009 requires an attacker who is active at the same time as the customer. A “conventional” MITM attack occurs according to one of the methods described above, but an alert is sent to the attacker at the moment the customer connects to the bank. The sits on its own computer and gets the authentication information (eg password) transmitted in real-time. These attacks are not a theory, they take place actively and successfully.
The first type exploits the fact that the continuity of a bank session is often established via a cookie with a “session ID”. This cookie can be transferred from the attacked computer to the attacker’s computer, then the attacker interrupts the victim’s session, which logs in again, the attacker continues the original session.
The victim can be induced by simulated TAN queries to enter abundant TANs, which are immediately transferred to the attacker, which then performs referrals.
In this way, the account can be cleared much more effectively than through an automated attack. And this “human assistance” is often outsourced to low-wage countries.
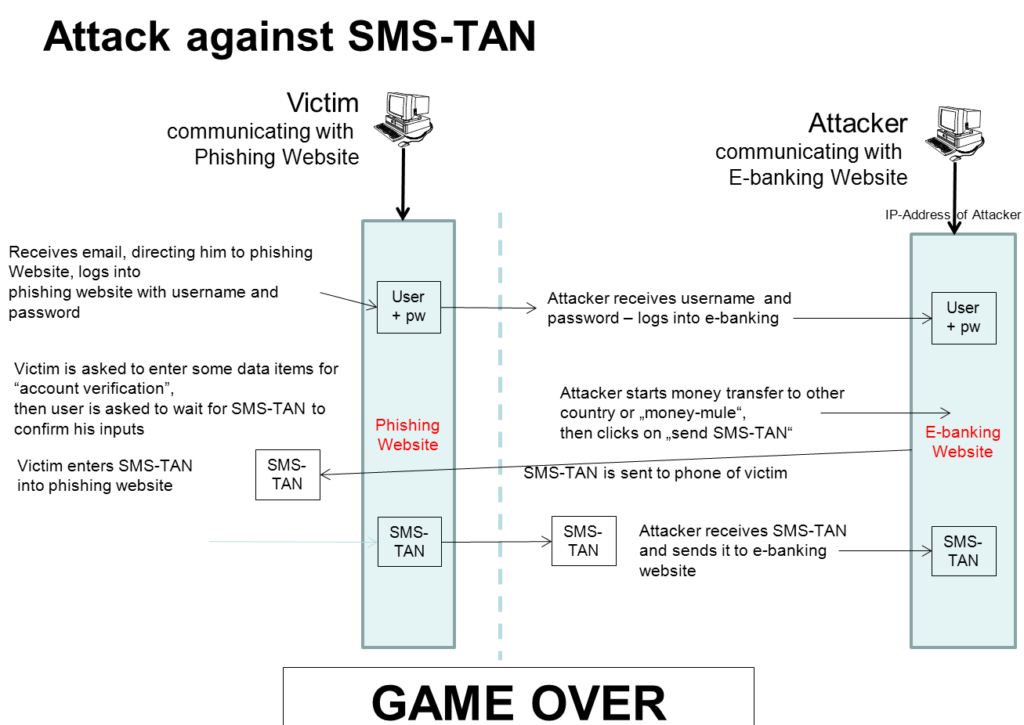
In the attack to the left the victim gets an email and is lured to a fake bank website. There he enters the user name and password and is then occupied by further entries, eg date of birth and email address. The username and password were sent to the attacker at the same time, who logs in to the bank instead of the victim and see if there is something to be fetched on the account. If so, he makes a transfer and requests an SMS TAN.
The victim has now been warned that he would immediately receive an SMS TAN, which he would have to enter for confirmation. Now everything depends on whether the victim is reading through the SMS. Because there is in it that he would transfer money to any account. If the victim does not notice this, the SMS is typed, the attacker gets the message and can confirm his own transfer.
Attack with remote control – Neverquest
There are other variations of such attacks. The Trojan Neverquest installs a remote maintenance software on the victim’s PC and therefore can not only access the user’s data, but also connect it to this computer and execute fraudulent transfers from this computer. This has the big advantage for the fraudster, that for the fraud detection systems of the banks the attacker comes from the right PC, has the same IP address as always and that there are no hints that something is wrong.

Leave a Reply