If you operate Raspberry Pi as an IPv6 tunnel endpoint or IPv6 gateway , then “every computer on the LAN” can be reached worldwide with its own global IPv6 address. Everyone can access these computers from the outside if an IPv6 address is known from the LAN. It is not the way you know it from IPv4, it can hide behind a router via NAT.
The consequence of this is that you have to make sure that an appropriately configured IPv6 firewall is active on Raspberry Pi.
task
- Set up an IPv6 firewall on Raspberry Pi to prevents unwanted external access and permits desirable access.
- Check if the firewall works.
solution
This solution is based on Raspberry Pi running as a SixXS tunnel endpoint or IPv6 gateway. This solution is a suggestion that has to be adapted depending on the application.
There are many ways to run a firewall with Linux. In this case we opt for “ip6tables”. It is a packet filter, which is sufficient for a simple firewall.
First, let’s create a setup file for the firewall rules.
nano ip6tables.rules.sh
In this file we write in the following rules:
#! / Bin / bash
# File: ip6tables.rules.sh
# Test: IPv6 stateful firewall for an IPv6 tunnel or gateway
# As of: 2014-12-16
# Delete all rules
ip6tables -F
ip6tables -X
ip6tables -t mangle -F
ip6tables -t mangle -X
# Discard all packages with RH0 headers
ip6tables -A INPUT -m rt --rt-type 0 -j DROP
ip6tables -A FORWARD -m rt -rt-type 0 -j DROP
ip6tables -A OUTPUT -m rt --rt-type 0 -j DROP
# Allow connections to the localhost
ip6tables -A INPUT -i lo -j ACCEPT
ip6tables -A OUTPUT -o lo -j ACCEPT
# Allow all connections to the local network
ip6tables -A INPUT -i eth0 -j ACCEPT
ip6tables -A FORWARD -i eth0 -o eth0 -j ACCEPT
ip6tables -A OUTPUT -o eth0 -j ACCEPT
# Allow all link-local connections
ip6tables -A INPUT -s fe80 :: / 10 -j ACCEPT
ip6tables -A OUTPUT -s fe80 :: / 10 -j ACCEPT
# Allow all multicast connections
ip6tables -A INPUT -d ff00 :: / 8 -j ACCEPT
ip6tables -A OUTPUT -d ff00 :: / 8 -j ACCEPT
Allow # ICMPv6
ip6tables -I INPUT -p icmpv6 -j ACCEPT
ip6tables -I FORWARD -p icmpv6 -j ACCEPT
ip6tables -I OUTPUT -p icmpv6 -j ACCEPT
# Allow forwarding (only useful in gateway mode)
ip6tables -A FORWARD -m state --state NEW -i eth0 -o sixxs -j ACCEPT
ip6tables -A FORWARD -m state --state ESTABLISHED, RELATED -j ACCEPT
ip6tables -A FORWARD -m state --state INVALID -j DROP
# Allow packets to forward with no-next headers
ip6tables -A FORWARD -p ipv6-nonxt -m length --length 40 -j ACCEPT
# Allow all outgoing connections through the tunnel
ip6tables -A OUTPUT -o sixxs -j ACCEPT
# Allow all internal connections through the tunnel
ip6tables -A INPUT -i sixxs -m state --state ESTABLISHED, RELATED -j ACCEPT
# Default settings
ip6tables -P INPUT DROP
ip6tables -P FORWARD DROP
ip6tables -P OUTPUT DROP
These rules have been checked to the best of our knowledge and belief. I assume no liability for damages caused by these rules and also do not guarantee the accuracy and completeness of the rules. There is no guarantee that these rules are correct in every case and for all time.
Then save and close: Ctrl + O, Return, Ctrl + X.
Then the file has to be made executable first in order to execute it afterwards.
chmod 744 ip6tables.rules.sh
sudo ./ip6tables.rules.sh
One does not get confirmation for the success. If the command line returns without an error message, it means that no error occurred.
The IPv6 firewall is now configured. However, only temporarily. After a restart, these rules would be gone again. That’s just fine. Before we take over the rules permanently, we want to know if the firewall rules work.
For this we go to a website that runs an IPv6 scanner: https://www.ipv6scanner.com .
Enter the IPv6 address of Raspberry Pi here. The address you get with “ifconfig”. Look here for the interface “eth0” and the line with “inet6-Adresse”, marked with “Global”.
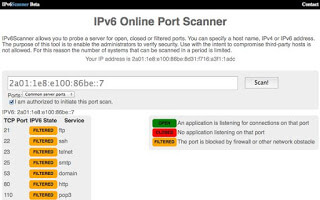
During the scan, several ports appear in succession (not all). If the “IPV6 State” of a port is set to “Filtered”, then everything is fine. In principle, a port may also be “open”. But then you should know which service “listens” to this port and what it does. An “open port” is always a possible point of attack.
The file with the firewall rules can be modified and added at any time. Just remember to run it again if you want to apply the changes. And most importantly, you should check the rules to see if they work.
You can get a statistic for that. Here you can see how many and which connections were blocked or allowed.
sudo ip6tables -nvL
The IPv6 firewall is now configured. However, only temporarily. After a restart of Raspberry Pi these rules would be gone. If you want to permanently apply changes to the rule set, they must be saved.
sudo sh -c "ip6tables-save> /etc/iptables/rules.v6"
Again, there is no confirmation. If successful, simply return the command line. To be on the safe side, look at the latest firewall rules for IPv6 in the following file:
cat /etc/iptables/rules.v6
If you want you can do a reboot to test if the rules are really used after a reboot. That is not necessary.
Important instructions
The way the firewall is configured here is usually discouraged. By writing the ip6tables commands in a shell script and then executing them in one piece, a process is started for each ip6tables command that requires processing power and time. When the script is run, the packet filter is deleted and reset. For less than a few milliseconds, the firewall is working with an unfinished packet filter, which is not a good idea.
Given that the command list or the shell script is relatively short, one can just accept this solution. But if the script gets even longer, for example, with personal settings, you should do without this solution and make the ip6tables configuration directly and NOT by script.
These instructions and the firewall rules used in them do not claim to be correct and complete. Both the instructions and the rules are only suggestions.
Configuring a firewall securely and correctly succeeds only with a lot of experience and in which again and again the established rules are checked and adapted to the current security situation.

Leave a Reply