convert cap to hccapx Solve the problem “Old hccap file format detected! You need to update
If you crack WiFi password in Hashcat, then you know that Hashcat cannot work directly with network capture files (.cap or .pcap), these files need to be converted to a special Hashcat format. For conversion to the format in the .hccap format, a bunch of wpaclean programs (for cleaning extra data) and aircrack-ng (for the conversion itself) were usually used.
But in the new version of Hashcat, when trying to find the password to the .hccap file, we are met with an error:
Old hccap file format detected! You need to update
Let’s start with a little background. The aircrack-ng and cap2hcap programs that are commonly used to convert handshakes to Hashcat format do not check the repeat counter attribute, which is used to distinguish different WPA handshakes for the same access point and station. At least they don’t do it right. The result is what may turn out to be a .hccap file that looks correct, but will never be hacked, even if your dictionary contains the correct password.
Especially if you launch a deauthentication attack to speed up the process of capturing a handshake, then it is possible to launch several simultaneous WPA handshakes in parallel (and their capture) from the same TD and Station. Each of them will have different nonce (random data), which are part of the calculation that hashcat performs to verify whether the password candidate is correct or not. To perform a successful verification, it is important to use the correct nonce, and for this to be so, it is important to correctly check the consistency of the handshake packages.
This atom problem (by hashcat) was reported to the Aircrack-NG team: http://trac.aircrack-ng.org/ticket/651
Since this ticket was opened 8 years ago and the last changes to cap2hccap were made 3 years ago, atom decided to write its own converter. At the moment, the converter is finished and is called ” cap2hccapx “. It has been added as a new tool in hashcat-utils .
cap2hccapx checks if a handshake has been made up of several.
To break the password, as is known, the captured so-called four-stage handshake (handshake). It consists of four elements. But not all of these items are required to crack a password. Now hashcat can crack and incomplete handshakes (the so-called WPA2 Half Handshake).
These new features (more precisely, new information) forced us to create a new capture format for hashcat. The developers called it “hccapx”. You can find details about it here: https://hashcat.net/wiki/hccapx (and if you prefer, you can compare it with the old hccap format https://hashcat.net/wiki/hccap ).
In general, several new entries were added to allow hashcat to determine if the handshake file was valid (“HCPX” was added to the beginning of the file), a version about the format was added and, of course, information about whether the authentication was successful and, therefore, The third message is captured (the third element of the handshake). If the handshake is complete, then hashcat will crack two types of records from the handshake. This does not require additional costs, since all verification is done after the slow part of PBKDF-HMAC-SHA1.
The hccapx format is new. Of course you have a lot of .hccap files in the archives. But without the changes made, it was impossible to be sure even that the data converted into a hash can be compromised altogether due to missing checks and incorrect matching algorithms. For this reason, it makes absolutely no sense to convert from hccap to hccapx.
If you used an old online converter, update your link to: https://hashcat.net/cap2hccapx/
If you prefer to convert the capture files (handshakes) to hashcat format on your computer, then let’s take a closer look at the cap2hccapx utility . As already mentioned, it is part of the hashcat-utils package .
The tool is used to generate .hccapx files from network capture files (.cap or .pcap) for hacking WPA / WPA2 authentication. The .hccapx files are used as input for the hash type -m 2500 = WPA / WPA2.
Additional options allow you to specify a network name (ESSID) to filter unwanted networks and to provide cap2hccapx network name prompts (ESSID) and MAC address of the access point (BSSID) if no beacons were captured. Using:
./cap2hccapx.bin input.pcap output.hccapx [filtering by essid] [additional network essid: bssid]
In Kali Linux and BlackArch hashcat-utils, utilities are available in standard repositories and even pre-installed on systems. However, at the time of writing there are old versions in which the cap2hccapx program has not been added yet.
The hashcat-utils package is portable and cross-platform.
You can download binary files here: https://github.com/hashcat/hashcat-utils/releases
After downloading, just unpack the archive and run the required * .bin or .exe files for Windows.
Or install from source codes.
git clone https://github.com/hashcat/hashcat-utils.git
cd hashcat-utils/src/
make
sudo mv *.bin/usr/local/bin/
sudo cp -a *.pl/usr/local/bin/
If the capture file (saved with the name RT-726940.cap) contains only one handshake and I want to convert it into hashcat format to crack the Wi-Fi password into a file called output.RT-726940.hccapx, then my command looks like:
cap2hccapx.bin RT-726940.cap output.RT-726940.hccapx
The program will write something like:
Networks detected: 1
[*] BSSID = c4: a8: 1d: 64: 24: 38 ESSID = RT-726940 (Length: 9)
-> STA = 40: 45: da: b9: 3a: eb, Message Pair = 0, Replay Counter = 6
Written 1 WPA Handshakes to: output.RT-726940.hccapx
Consider another case – when there are several handshakes in the capture file (/home/mial/autopwner.cap)
pyrit -r "/home/mial/autopwner.cap" analyze
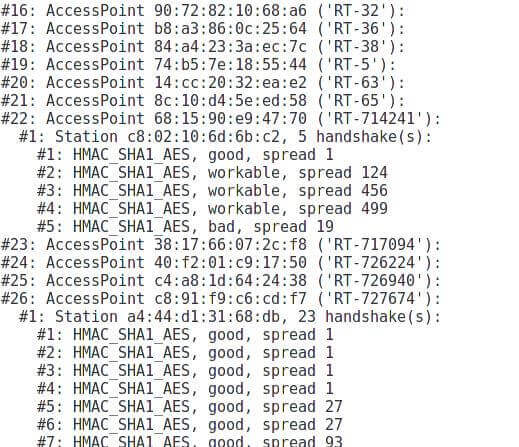
You can see that there are handshakes for access points RT-714241 and for RT-727674.
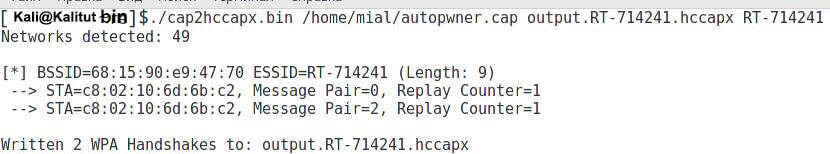
If I am interested in a handshake only for the access point RT-714241 and I want to save the hash to crack the password in the file output.RT-714241.hccapx , then my command will look like this:
cap2hccapx.bin /home/mial/autopwner.cap output.RT-714241.hccapx RT-714241
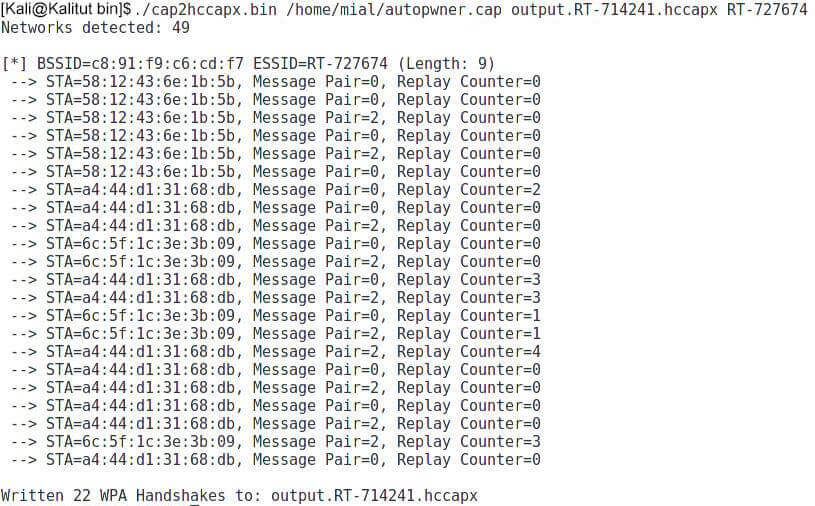
Accordingly, if I am interested in handshakes only for RT-727674, then the team turns into:
cap2hccapx.bin /home/mial/autopwner.cap output.RT-714241.hccapx RT-727674
If I need all the hash handshakes, then it can be done like this:
cap2hccapx.bin /home/mial/autopwner.cap all.hccapx

Is your space bar just not working or what, bruh???
You said to use the command:
“Sudo mv *.bin/usr/local/bin”
THEN you said that we should use the command: “sudo cp -a *.pl/usr/local/bin”
Guess what, jackass?? You CLEARLY left out a SPACE in BOTH OF THOSE COMMANDS. SO PEOPLE LIKE ME, WHO RELY ON ‘EXPERTS’ LIKE YOURSELF, TO GIVE US COPY/PASTE CONNANDS – just get screwed over, huh??
…yeah thanks man