
1. DROID-HUNTER
Android application vulnerability analysis and Android pentest tool
A. Support
- App info check
- Baksmaling android app
- Decompile android app
- Extract class file
- Extract java code
- Pattern base Information Leakage
2. How to Install?
A. Download(clone) & Unpack DROID-HUNTER
git clone https://github.com/hahwul/droid-hunter.git
cd droid-hunter
B. Install Ruby GEM
gem install html-table
gem install colorize
C. Set external tools
Editing "./config/config.rb"
# Tool path
$p_adb = "/usr/bin/adb"
$p_aapt = "/usr/bin/aapt" # Path aapt
# macOS > (https://github.com/hahwul/droid-hunter/issues/12)
$p_dex2jar = File.dirname(__FILE__)+"/../ex_tool/dex2jar-0.0.9.15/dex2jar.sh"
$p_apktool = File.dirname(__FILE__)+"/../ex_tool/apktool/apktool_2.3.1.jar"
$p_jad = File.dirname(__FILE__)+"/../ex_tool/jad/jad"
$p_grep = "/bin/grep"
$p_unzip = "/usr/bin/unzip"
$p_sfilter = File.dirname(__FILE__)+"/../string_filter"
D. Run Droid Hunter
ruby dhunter.rb
3. How to Use?
Usage: ruby dhunter.rb [APK]
Command
-a, --apk : Analysis android APK file.
+ APK Analysis
=> dhunter -a 123.apk[apk file]
=> dhunter --apk 123.apk aaa.apk test.apk hwul.apk
-p, --pentest : Penetration testing Device
+ Pentest Android
=> dhunter -p device[device code]
=> dhunter --pentest device
-v, --version : Show this droid-hunter version
-h, --help : Show help page
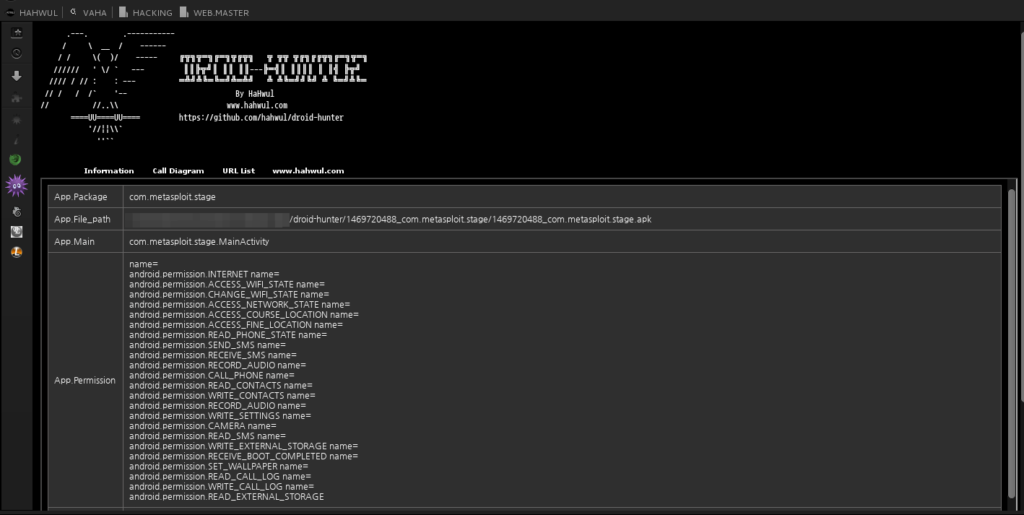

Nice
How can I download this app