How Wifiphisher Works
Wifiphisher uses social engineering to get a password for WiFi and websites the method is called Evil Twin Attack. You do not need a powerful hardware for a long time for bruteforce password.
The principle of the tools:
- the access point is selected, its settings are copied (name, channel, etc.)
- on the WiFi card of the attacker, a clone (Evil Twin) of this access point is launched, which repeats the original except for one thing – you can connect to it without a password
- users are disconnected from the original access point by deauthentication attack
- the original access point is continually muffled. For this, the attacker needs a second wireless card.
- when a user connects to the Evil Twin, he is asked for a WiFi password (for example, to update the firmware) under various pretexts. The password thus received is sent to the attacker.
If we compare the Evil twin from Wifiphisher with the Evil twin from Fluxion , then we can pay attention to the fact that Wifiphisher does not check the data received from the user. This greatly reduces automation. The attacker, during the attack itself, must somehow verify the password received and decide whether to continue or stop the attack. Recently in Wifiphisher appeared -qS key . If you specify it, then Wifiphisher stops its work after the first received credentials, even if they are incorrect. As seen in the example of the attack with Fluxion, the tools can be left to work for a long time and it will not allow the user to connect to the original access point until he enters the correct WiFi password, but after entering it, it “falls off” immediately.
Another feature of Wifiphisher is that the tools allows you to get passwords from websites under the pretext of accessing a free Internet connection. The tools has already implemented a script for obtaining a password from Facebook, but you can write your own script for any site. By the way, with this attack, one wireless interface is enough – the one on which the access point rises with free WiFi; during an attack, you do not need to jam other access points.
How to install wifiphisher kali linux
Now Wifiphisher is available in the standard Kali Linux and BlackArch repositories, so the installation can be done in one command.
Installation on Kali Linux
sudo apt-get install wifiphisher hostapd dnsmasq python-pyric python-jinja2
Installation in BlackArch
sudo pacman -S wifiphisher dnsmasq hostapd net-tools python2-pyric python2-j2cli --needed
Although Wifiphisher makes all the necessary settings and puts the right interface into monitor mode, it does not unload the Network Manager, which can affect the success of the attack. It is recommended to do it manually:
sudo systemctl stop NetworkManager
Run the tools with administrator rights:
sudo wifiphisher
When you start the tools, you can see the message:
There is not enough wireless interfaces for the tool to run! Please ensure that there is no need for wireless adapters. Master mode (AP) mode and another must support Monitor mode.
Otherwise, you can try the deauthentication phase option.
The message reads as follows:
Not enough wireless interfaces to run the tool! Please ensure that at least two devices are connected and that they are compatible (the driver must support netlink). At least one must support Master Mode (AP), and the other must support Monitor mode.
Otherwise, you can try the option –nojamming , which disables the deauthentication phase.
If everything is in order with your WiFi adapters, the following window will appear:
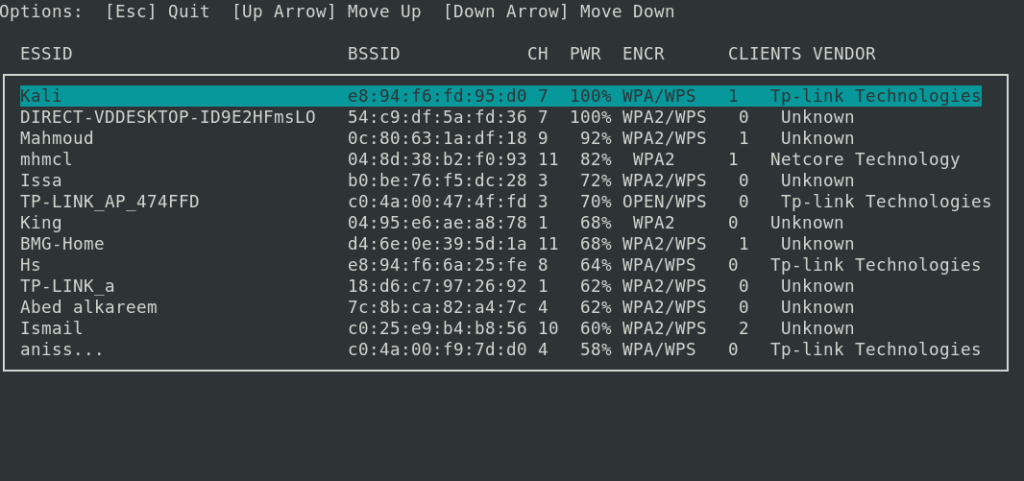
In it, select (up-down arrow) the wireless network to attack and press ENTER. To exit press ESC.
You will be offered a choice of phishing scripts:
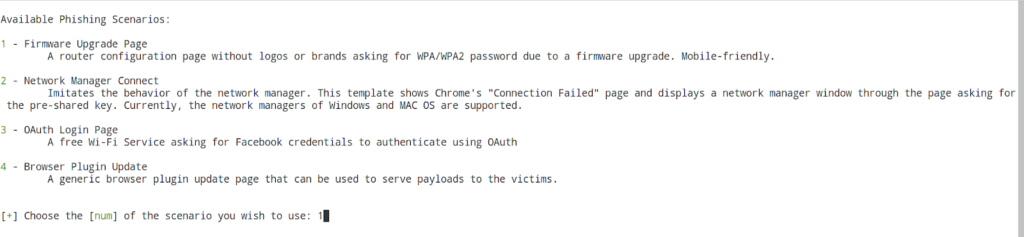
Phishing Scripts Available:
1 – Firmware Upgrade Page
The configuration page of the router without logos and brands, asks WPA / WPA2 password to update the firmware. Also adapted for mobile phones.
2 – Network Connection Manager
Simulates the behavior of a network manager. This template displays the Chrome “Connection Failed” page and displays the network manager window on top of the page that asks for a WiFi key. Currently, Windows and MAC OS network managers are supported.
3 – Oauth login page
Free Wi-F service asks Facebook credentials to authenticate using OAuth
4 – Update Browser Plugin
A browser plugin update page that can be used to deliver a payload to a victim.
Enter the number of the script you want to use. Let’s start with the first.
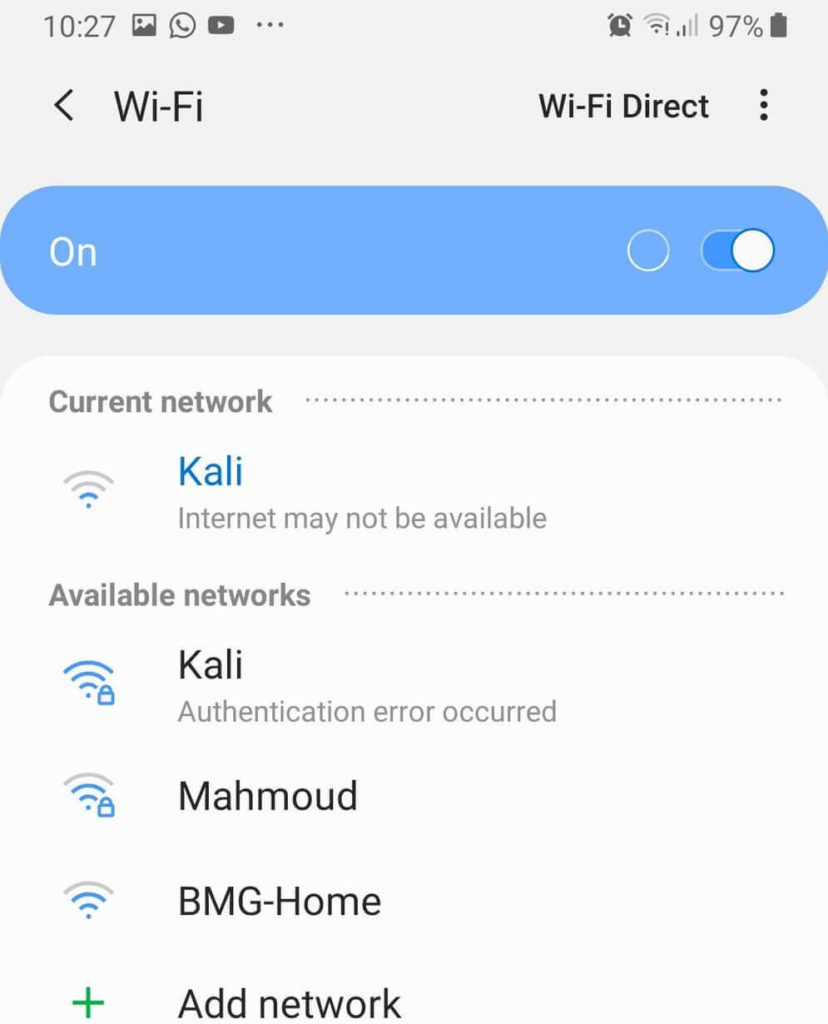
The victim will see two APs with the same name. And it is impossible to connect to the original one (which is with a password). The second (Evil Twin) allows you to connect without a password.
The attacker sees at this time:
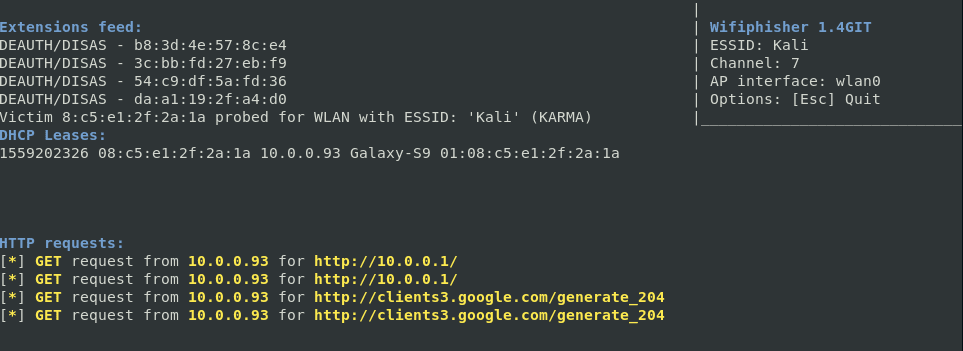
The line deauthenticating clients shows clients for which to turn off WiFi (i.e., an obstacle is created to connect to the original access point). A line of DHCP Leases shows those who have already connected to the Evil Twin. HTTP requests show requests that were made by clients.
When trying to open any website, the client sees a message about the need to update the firmware of the router.
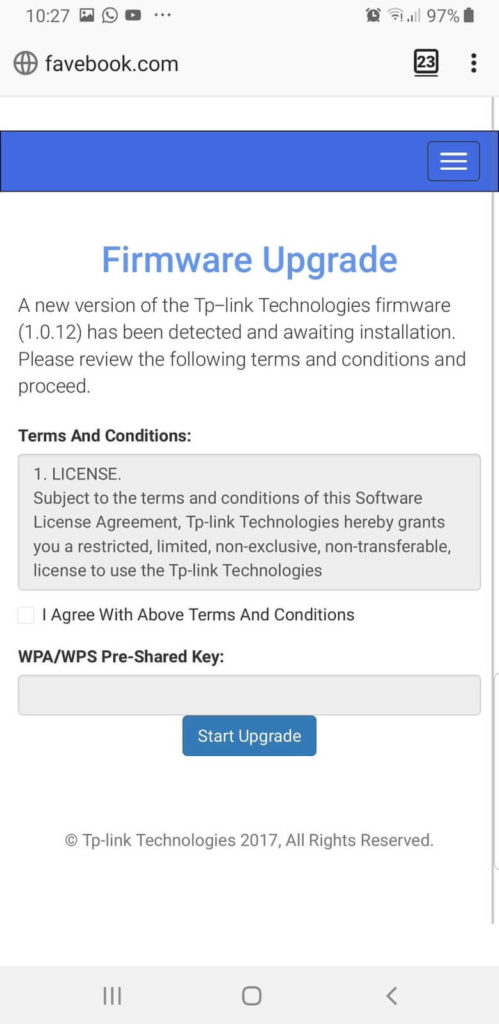
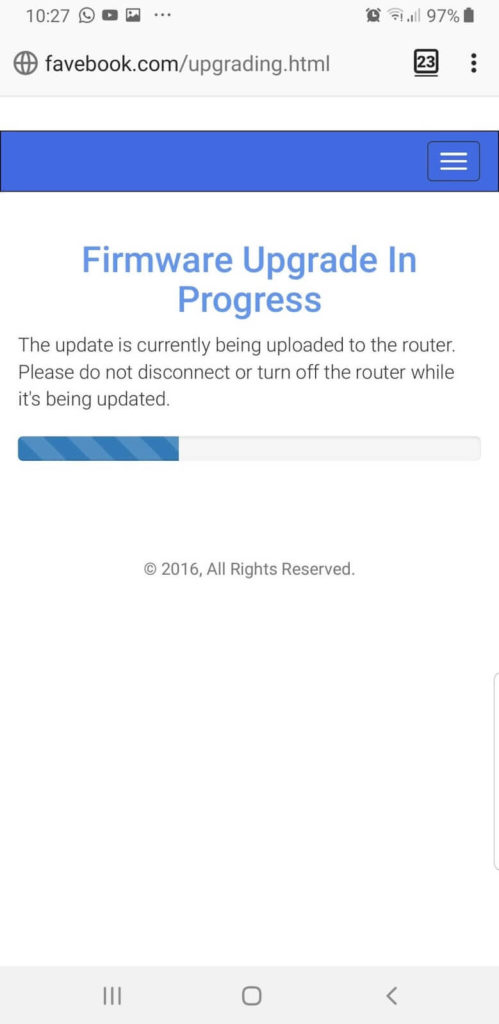
After entering the password, a rather long “update” process is launched:
And the attacker sees:
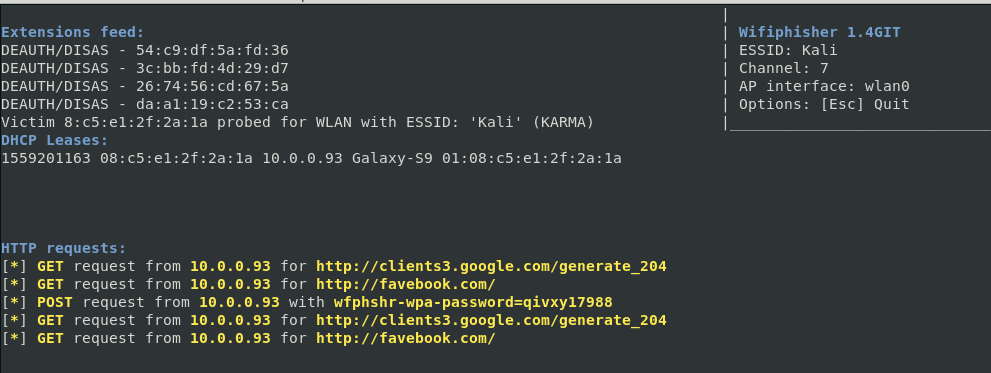
Look at the line where it start with ( Post request ) we got the data we want.
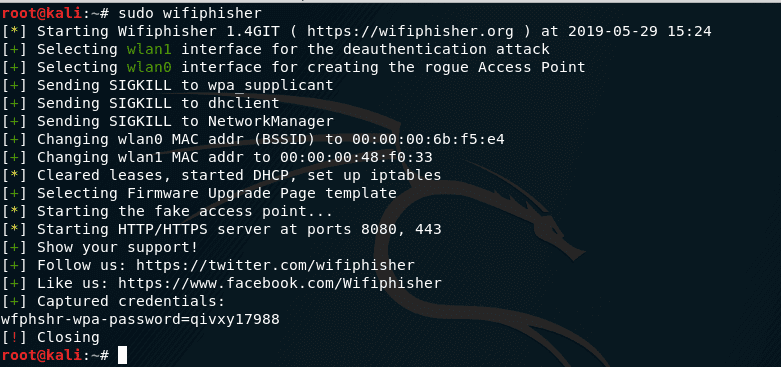
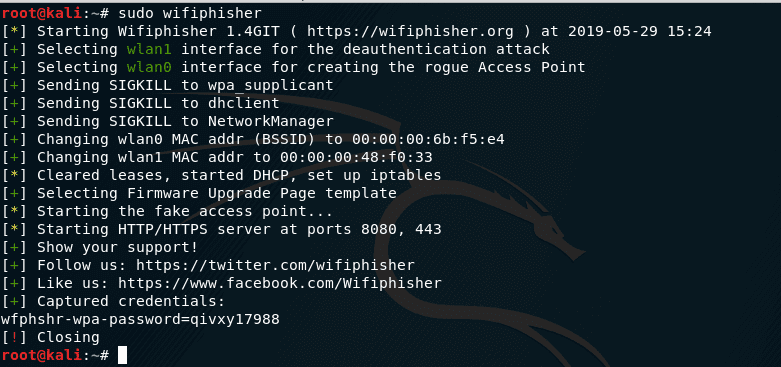
To stop the attack, press CTRL + c . If the credentials have been successfully captured, the following message will be displayed:
[+] Captured credentials:
u'wfphshr-wpa-password=qivxy17988'
As shown in the photo below in last line
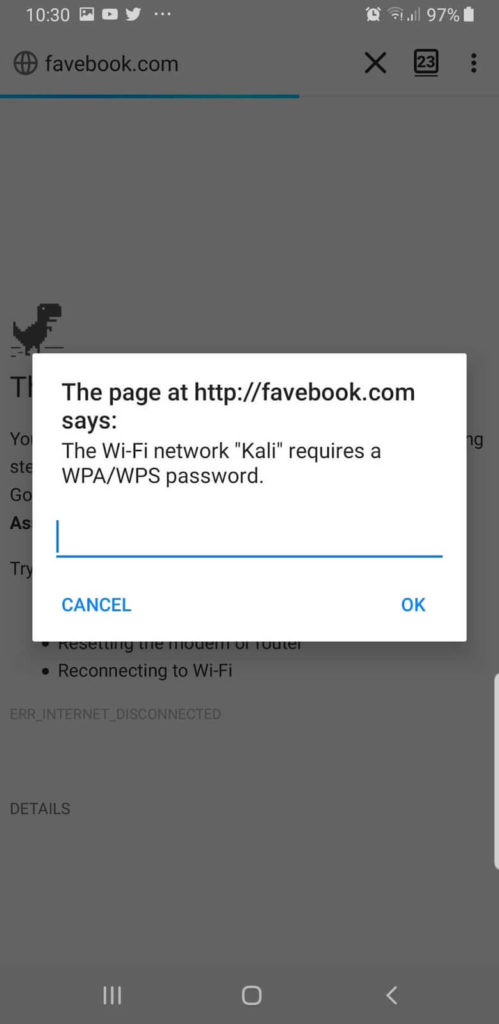
In the second scenario, the victim is prompted to enter the password:
Conclusion
Wifiphisher, when compared to Fluxion Tool with similar functionality, has its advantages (various phishing scripts, including passwords from websites, automatically selected logos for the most popular routers – this significantly increases confidence) and disadvantages (lack of validation of the entered password WiFi, less autonomy, since it requires the constant presence of an attacker to make a decision to stop the attack).

This program works very well, but I wish it has the option to capture hidden A.P.s or allow manual entry of the ESSID and BSSID if known.
I’m not able to install wifiphisher please help me kindly
Hi, dear team I would like to know if Wifiphisher stores the captured credentials in a file?