How rogue access point work?
The attack using a fraudulent access point (Rogue access point) is to create a wireless network without encryption so that anyone can connect to it, they are man-in-the-middle attacks.
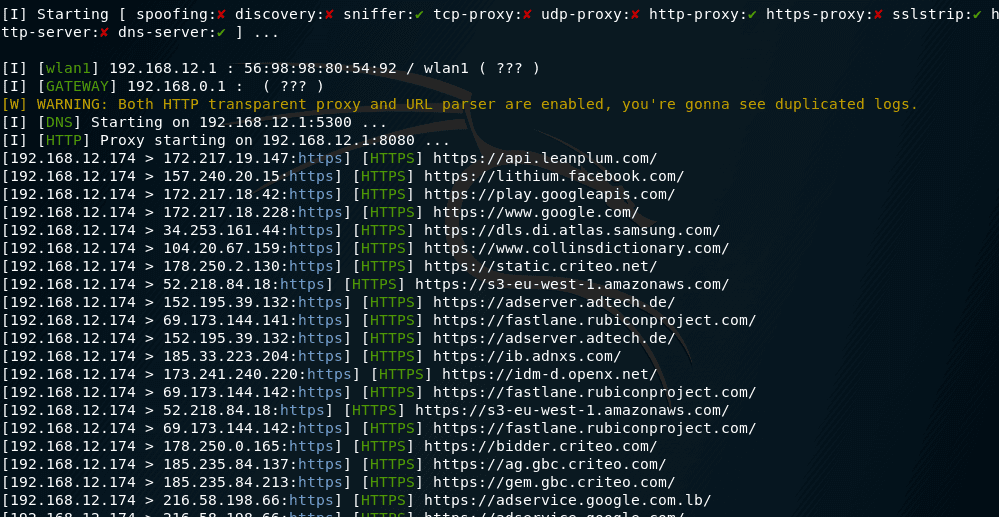
Unlike the Evil Twin attack and most other WiFi attacks, the purpose of the fraudulent access point is not WiFi passwords. The main goal is the traffic of the user against which the mediator is attacking. For this situation, apply absolutely all methods of attack man-in the middle.
[Read more…] about Rogue access point guide