The Internet of Things (IoT) also helps the concept of the Smart Home through more and more networked devices to a greater extent. However, smart home networks have at least one connection interface that can potentially be used by attackers. To prevent this, a proven hardware security concept is required.
With the rise of IoT devices, the environment of our home networks has drastically changed in recent years. Five years ago a home network consisted of a router, which was connected to the Internet via ADSL or cable connection. This was mainly connected to devices such as desktop computers and laptops. Today, more and more intelligent devices have an Internet connection so their data can be collected and controlled. However, any device that is attached to the home network can actually constitute an access point for attacks and thus a security risk.
In addition, radio networks in today’s Smart Home are not limited to WLAN. Radio standards such as Bluetooth, ZigBee and Z Wave spread quickly. The more different radio standards exchange data, the more potential areas of attack arise. Therefore, additional protection on system level is essential.
Numerous intelligent devices with different microcontrollers also work with proprietary real-time operating systems (RTOS). The security level of such solutions varies from provider to supplier. In addition, malicious software can be played on these devices if firmware updates are required, provided that sufficient protection is not available.
It is important that manufacturers of these devices, the threats and the protective mechanisms available to them are familiar with and understood.
Significant security risks in Smart Homes
The security risks for SmartHome can be roughly divided into four categories
Fake device identifications: Most SmartHome devices have a device identifier as a unique identifier or certificate. However, a unique identifier can be easily replicated without encryption protection as soon as the attacker knows how it is generated. In this case, the attacker would be able to gain immediate access to the network via a simulated device and initiate subsequent attacks from there. Also, verifying the identity of the server is equally important. If a device is connected to a malicious server, critical user data might be stolen. In the worst case, the entire home network can be attacked.
Listening to data: Most of the communication interfaces used in SmartHomes are based on wireless technologies such as Bluetooth, ZigBee, or WLAN. Although these usually have certain protective mechanisms, they are often not stable enough because of the limitations which the applications involved. For example, Bluetooth often works with a simple password, to establish the coupling (so-called pairing). This increases the risk of spying critical and confidential user data over the communications interfaces. It is also common to encrypt transmitted data with cryptographic keys to ensure that they remain confidential and not tampered with. However, it is then crucial to protect the cryptographic keys against theft and spying.
Manipulation of data: There is also a risk of data manipulation. Therefore, the protection of data integrity in smart home environments is also an important security issue. Critical information such as billing data, confidential configuration data or resource use must not be transmitted and stored in a manipulated form.
Infection with malicious software: After an attacker has access to the network, he usually installs malicious software with which he initiates the next stage of the attack from the affected device. When networked devices are sabotaged and infected with malicious software, they can be taken into a botnet and used for DDoS attacks. Thus, many Smart Home devices – not just computers – become the potential starting point of DDoS attacks. The number of such smart home devices (such as smart cameras or routers) is significantly greater than the number of computers connected to the network. Therefore, both the range of damage and the speed with which damage is caused by DDoS attacks from botnets can be significantly greater.
Basic cornerstones of safety engineering
These security risks can be countered by observing three basic security aspects: Confidentiality by encrypting sensitive data; Integrity by the protection of data with cryptographic message authentication code or digital signature; and authenticity through the use of strong cryptographic authentication systems.
At the core of these three cornerstones are the cryptographic keys, which are used for the encryption and decryption, for the calculation of the CMACs (cipher-based message authentication codes) and for the support of the strong cryptographic authentication systems. Still, if an attacker succeeds in stealing or replicating these cryptographic keys, it would be possible to listen to the transmitted data, manipulate it, and issue a fake device as the “correct” one.
It is therefore extremely important to keep these cryptographic keys protected in tamper-proof, hardware-based “security anchors”.
Security hardware for the protection of smart homes
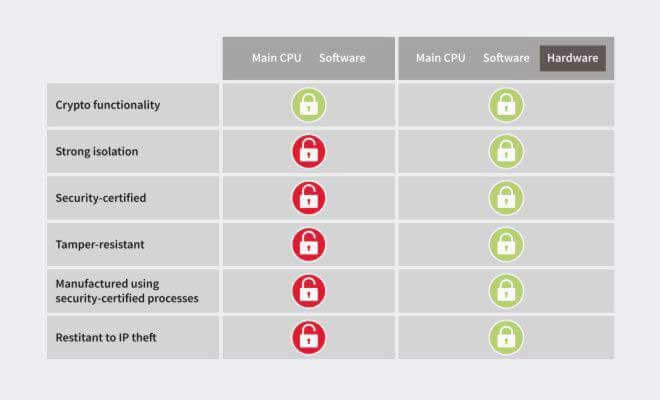
Secured identities are obtained by using secret keys and by applying encryption methods that work with secret keys. Secret keys are a basic root of trust for the entire chain of security measures that are required to protect smart home systems. Hardware-based security solutions, in contrast to pure software-based implementations, are capable of providing the required robust security level and a higher level of trust.
Purely software-supported solution concepts often have overgrown vulnerabilities such as programming errors and are vulnerable to attacks by malicious software. Typically, it is comparatively easy to read and overwrite software. This makes it easy for attackers to spy secret keys.
In contrast, hardware-based security concepts can be used to store access data and keys at the same security level that provides a safe for keeping confidential documents (Figure 3). The spatial separation of the software applications and the cryptographic keys creates a cost-efficient and extremely effective barrier against the spying out of the keys and certificates in case of an infection with malicious software.
Typical applications in Smart Home
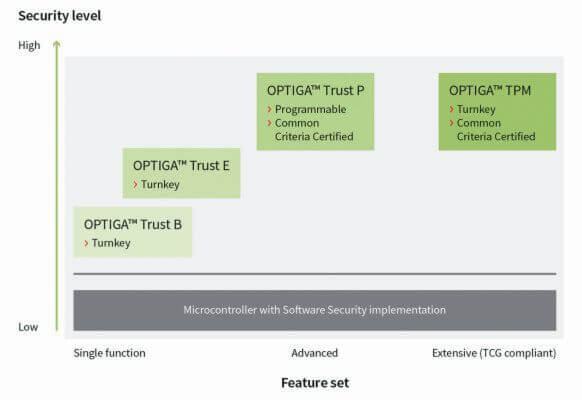
The authentication is the process is identified in grids where users, computers, appliances and machines and access to authorized persons and not manipulated devices is limited. Hardware-based protection mechanisms can support authentication by making sure that access data from devices (cryptographic keys or passwords) are stored securely. Infineon has developed a wide range of OPTIGA products that build a root of trust in hardware devices to enable secure device and system authentication.
In typical architectures with embedded systems, devices are interconnected through heterogeneous networks that operate with different standardized and proprietary protocols. In order to ensure secure data transmission, for example, protected against interception and distorted messages, it must be protected between these systems. The OPTIGA family from Infineon is suitable to store the keys and certificates used in data transfer protocols and to support cryptographic procedures.
Confidential user data is often stored in embedded systems. Security and confidentiality can be protected by encrypting or signing stored data. The difficulty is to store cryptographic keys securely. Data can be easily decrypted if the attacker succeeds in reading the keys. The Infineon product families OPTIGA Trust and OPTIGA TPM offer solutions by encrypting data and storing cryptographic keys securely. They also support software- and hardware-based integrity
Software and firmware in embedded systems usually need to be regularly updated. However, it may be difficult to protect both the software itself and the system being updated. Firmware updates that are solely protected by software are potentially endangered, as software can be read, analyzed and modified to sabotage the update or the system. However, the software can become trustworthy when combined with security hardware. Secure hardware from the OPTIGA ™ product family from Infineon protects the processing and storage of program code through encryption, error and manipulation detection as well as secure storage of program code and data.
Protection against the four important attack scenarios
In SmartHome, more and more devices are networked with one another. These connections can be used by attackers as an access point to enter the system and to steal sensitive information such as passwords, manipulate data, or inject malicious software.
In most cases, users are not aware of the vulnerabilities and security risks (for example by DDoS attacks) of purchased products. It is therefore essential that equipment manufacturers take protective measures in the development of their products.
Protection against the four important attack scenarios – fake identity of devices, monitoring of data, manipulation of data and attacks by malicious software – provide hardware-supported security anchors such as the OPTIGA product family from Infineon. On this basis, a secure foundation can be built, on which manufacturers of embedded systems and networked devices can build.

Leave a Reply