If you plan to study everything that is generalized, it is customary to call information security, then sooner or later (and rather sooner) you will hear or learn about such a utility as Nmap. Someone may say: “Ah, what’s there? Just scan the ports. ” Do not listen to these people. Knowing the capabilities of Nmap commands and the ability to use it, in itself already gives serious opportunities in the practice of pentest. And in this article I will try to show you the basics and give the most necessary recipes for using Nmap, as well as explain how it works.
if you are really into pentesting you should learn How to use nmap
When a software get ported to all those OS it’s a mark for how important that software is,
Whatever you are trying to do as a network Administrator or a Penetration Tester you will need to work with Nmap one day
What is nmap?
Nmap is an abbreviation of “Network Mapper”, a tool for researching the network and checking security. The utility is cross-platform, free, it supports Linux, Windows, FreeBSD, OpenBSD, Solaris, Mac OS X operating systems.
Nmap can scan using various methods – for example, UDP, TCP connect (), TCP SYN (half-open), FTP proxy (break through ftp), Reverse-ident, ICMP (ping), FIN, ACK, SYN and NULL scanning. The choice of the scanning option depends on the specified keys, the nmap call looks like this:
nmap <keys> target
For experiments, we take a special experiment host created by the nmap developers themselves – scanme.nmap.org. Run as root It is
not necessary to specify scan keys – in this case nmap will check the host for open ports and services that listen on these ports.
Run the command:
nmap scanme.nmap.org
After a few seconds, we get the result: Nothing unusual, ssh on the standard port and http on 80. Nmap recognizes the following port states: open , filtered
Interesting ports on scanme.nmap.org (74.207.244.221):
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
closed , or unfiltered . Open means that the application on the target machine is ready to accept packets on this port. Filtered means that a firewall, filter, or something else on the network is blocking the port, so Nmap cannot determine if the port is open or closed. Closed – are not currently associated with any application, but can be opened at any time. Unfiltered ports respond to Nmap requests, but you cannot determine if they are open or closed.
Hint: If you press the spacebar during a scan, you can see the current scan progress and how many percent it has been completed.
What does nmap do?
Nmap used for rapidly scan large networks, yet it works fine against single hosts.
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
With Nmap you can find:
- What computers are running on a local network.
- What IP addresses are running on a local network.
- What is the operating system of your target machine.
- What ports are open on the machine that you just scanned. ( port scanner )
- Find out if the system is infected with malware or virus.
- Search for unauthorized servers or network service on your network.
- Find and remove computers which don’t meet the organization’s minimum level of security.
While Nmap is commonly used for security audits, many systems and network administrators, find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
To accomplish its goal, Nmap sends specially crafted packets to the target host and then analyzes the responses.
The software provides a number of features for probing computer networks we will try to learn some of the features together
Nmap originally written by Gordon Lyon first release in September 1997 Written in C, C++, Python, Lua
How to use Nmap
The logic of using the utility is quite simple.
nmap [Scan Type (s)] [Options] {scan target}
By launching the nmap utility, we can immediately set the scan target, with the settings we need. It is important to understand that everything that is not a program’s functionality i.e. options and arguments, nmap will be regarded as a target, which means we can enter several objects as targets, and targets can be network addresses, ip addresses, ranges of ip addresses, networks, subnets, etc.
Also an important point: to perform many types of scans, you need superuser rights, I will try to mark the commands for which this is a prerequisite, but it is better to start working with Nmap immediately with elevated rights, so as not to get nervous every time he asks for root.
By the way, if you think that ports can be open or closed, then you are certainly right, but due to the peculiarities of packet transmission and responses to them by different protocols, to more accurately determine the state of the target under investigation, Nmap identifies six port states, they must be known to understand the results of scanning:
| Status | What it means |
|---|---|
| 1. open | Application accepts packet or connection requests to port |
| closed | The port responds, but is not used by any application. |
| filtered | Requests do not reach this port, which means it is impossible to determine whether it is open or not. |
| not filtered unfiltered |
The port is available, but Nmap cannot determine whether it is closed or open. Using a different scanning method usually helps. |
| open | filtered | I can’t determine if the port is open or is being filtered. Occurs if the open port is not responding. Using a different scanning method usually helps. |
| closed | filtered | I can’t determine whether the port is closed or is being filtered. Using a different scanning method usually helps. |
At the very beginning of work with a goal, we, as a rule, know very little about it, which means we need to obtain primary data, shorten or expand the list of goals of interest (depends on the task) and determine the further direction of movement. For each specific task, the algorithm of actions can change and there are no recipes guaranteeing success, but there is a basic set of actions that you should know right well, I will try to focus on these and not get into the wilds.
To begin with, we will analyze the basic commands from the help, this is necessary to learn the basics of using Nmap. In some examples, we will use the site scanme.nmap.org as a target for scanning. This site is specially created by Nmap developers to test the capabilities of the program.
Host discovery
host discovery , this concept is quite broad, and consists of the initial discovery of active IP addresses, this stage is also called ping scanning, here you need to understand that you can scan as, with all the usual, ICMP requests, and combining them with TCP, UDP and ARP requests. Upon detecting the host, Nmap will automatically scan its ports if no option is set to cancel this action.
Nmap host discovery options:
- -sL Scan to list.
Selecting this option will list the entire range of IP addresses on the network with the names assigned to them (if any). At the end of the list, the total number of IPs found will be displayed. If the domain name is set as the target, then IP and its Reverse DNS will be displayed. - -sP ping scan.
This option defines active hosts i.e. those that respond to requests and list them out. If you run this option with root privileges, then ARP requests will also be involved, thanks to which we will find out the mac addresses of working devices on the network. - -Pn Skip ping scan.
Using this option, Nmap will assume that all IPs in the network under study are active and will scan the entire range of IP addresses, including all ports on each IP - -PS / -PA / -PU
These are commands to get a list of ports. The only difference is the packets that will be sent to the host: PS is TCP SYN, PA is TCP ACK. There is actually no fundamental difference, but if there is a chance that the connection is blocked by the firewall, it is better to use the TCP ACK. Well, and PU (you need root) – this is UDP ping – is used to receive an ICMP packet with an error “port is not reliable”, all other errors, including the lack of an answer, indicate that the host is not working.
In addition to the specified options, you can specify which types of ICMP packets to use, this is done with the -PE options ; -PP; -PM – this is an echo request, a request for a time stamp and a request for an address mask, respectively, I will not dwell on them because such requests will most likely be blocked by the host or firewall. - -PO
Command to get a list of protocols by pinging using the IP protocol (root is required to run). In this case, answers should be received according to the protocol specified in the request, this means that the protocol is active, if the response comes that the host is not reachable, it makes it clear that the protocol is not supported. - -PR
This is ARP ping. The most optimal scanning method that allows you to determine the active hosts, services and ports they use (root is required to start). - –Traceroute
Option that allows you to perform tracing ie track the path to the host, it is used together with any type of scan and works on the basis of data received as a result of it (root is required to run)
Scanning Techniques
We come to the section on port scanning techniques. Almost all the options listed in this section require root to run, this must be taken into account. You can also use only one method at a time (exception UDP scan (-sU), it can be combined with any type of TCP scan.
- -sS
TCP SYN scan. This is the most popular and rather inconspicuous type of scan. when using it, the TCP connection is never established to the end. It works like this: Nmap sends a SYN packet, for the host it looks like they want to establish a real connection with it. If the response comes SYN / ACK, then the port is open, and if RST is closed, if the response does not come or an ICMP error message is received, then the port is filtered. - -sU
UDP scan. Allows you to scan ports used by UDP services, can be combined with TCP scanning (for example: -sS -sU). It works by sending an empty UDP header to the appropriate ports. If the error “port is unreachable” arrives, then depending on the type of error, Nmap determines whether the port is closed or filtered, if UDP received a reply, the packet means the port is open, and if there is no answer, it will be given the status open | filtered, in this situation, to clarify data can use the versioning option (-sV). UDP scanning works extremely slowly, because to speed up the process, it makes sense to specify a list of ports of interest (for example, -p U: 53) - -sA
TCP ACK scan which is used to determine the firewall rules and the ports they filter. - -sO
Scan IP protocol, this way you can determine which IP protocols are supported by the target. Upon receipt of any response via any protocol, such a port is marked as open, if an ICMP error is received, the “protocol is unreachable” error, it will be marked as closed, and sometimes filtered, if the response does not arrive, it is “open | filtered”.
Nmap port scan
Port Definition and Scan Order Sometimes it becomes necessary to scan a specific port or range of ports, and if you immediately know which ports are the target, it’s better to do so, this can seriously reduce time and leave fewer traces. If you do not specify the ports that we want to scan, then Nmap, by default, will scan all ports up to and including 1024 and all ports specified in the * /nmap/ nmap-services file for the protocol that will be scanned.
In order to manually select the ports or port range for scanning, the option:
-p
means that we want to scan only certain ports. We must first specify the type of scan, and then the ports that we want to scan, you can also specify the TCP protocol (option T :) or UDP (option U :) (if you do not specify both), do not forget that UDP scanning must be applied the -sU option is used, and the -sS option (or similar) is used for TCP scanning, for example:
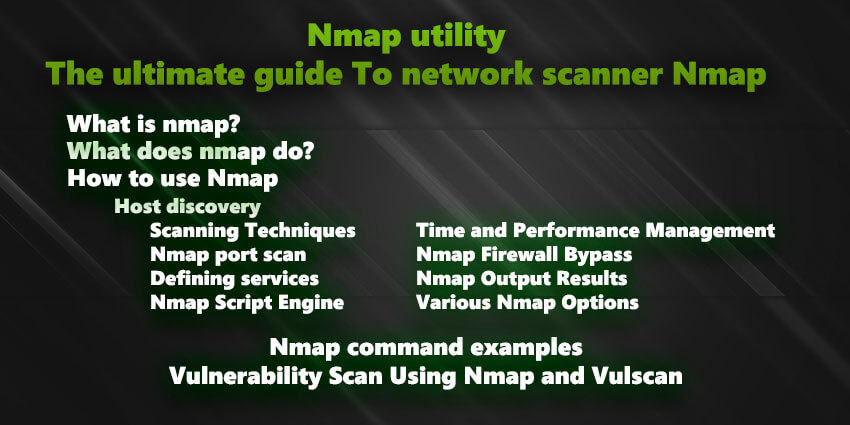
sudo nmap -sS -sU -p 22,80,111,53,137 scanme.nmap.org
Note
There are also slightly less common methods for determining target ports. If we specify the -F parameter, then the 100 most common ports will be scanned, and if -p- , then all 65535.
more about nmap port scaning : nmap port scan example
Defining services, their versions, and operating system
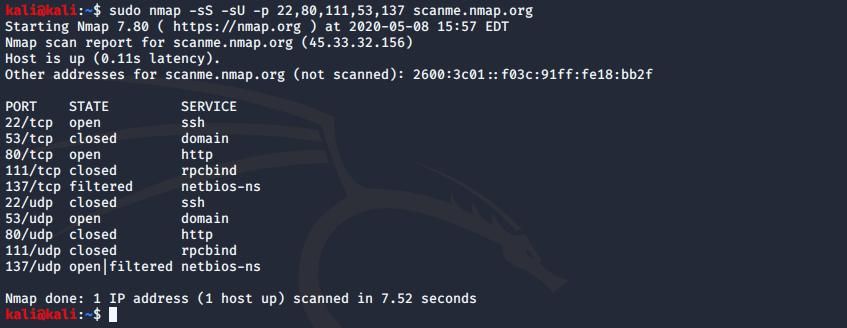
As can be seen from the screenshots shown above, Nmap determines not only the port number and status, but also the service that is running on this port, of course, in most cases this is reliable information, but there are tricky system administrators who run services on non-standard ports. Fortunately, Nmap makes it possible to determine whether such a service really works on the found port, and also to obtain additional information, such as host name, application name, version number, device type and OS family.
-sV Versioning
Having discovered the port, Nmap starts sending appropriate requests to it in order to determine which service this port is using, for this, information from the nmap-service-probes database (located in the nmap folder) is used, where the requests are contained and the types of responses to them are listed, to recognize the corresponding services.
–Version-intensity
The option setting the intensity determines which queries will be used during scanning. You can set the value from 1 to 9. The lower the value, the faster the scan will go, the higher – the slower, but more likely to correctly determine the service. If the option is not specified, the default value is 7, which is sufficient in most cases. If you want to use the maximum intensity, use the –version-all parameter , this ensures that every single request will be directed to each port (and be patient, this may take some time)
-O
Enable OS detection mode. When this option is enabled, Nmap sends several TCP and UDP packets to the host, and the results are compared with the data from the nmap-os-db file (located in the Nmap folder) and if it finds a match, it shows the answer for which OS and which version its typical behavior. Using the same matches, Nmap will try to determine the type of device and its manufacturer.
Note:
I talked about the options for determining versions and OS because you need to know about them for completeness of review, but in practice, in most cases, it’s better to use the -A option instead , which immediately includes the definition of OS, versions, tracing scanning using scripts.
Nmap Script Engine
One of the key features of Nmap is the use of scripts when scanning. A huge number of scripts are supplied, they are about 600 and they are in * /nmap/ scripts, the scripts database in the script.db file is in the same directory. For ease of use, all scripts are divided into categories. The trick is that you can run scripts immediately in categories (one or several), this eliminates the need to remember the names of individual scripts, although some scripts should be remembered (but more on that later). It is also important to remember that some scripts leave many traces on the target system, and therefore it is worth using them carefully and remembering the means of anonymization.
A complete list of scripts and their description can be found here: https://nmap.org/nsedoc/index.html
- auth
Category of scripts that works with authentication credentials on the system under study - broadcast
These scripts are needed to detect hosts not listed on the command line by broadcasting on the local network. When using the newtargets argument, found hosts will be automatically added to the scan queue - brute
Scripts for brute force attacks to obtain authentication credentials. - default A
basic set of scripts defined by developers as “default scripts” to extend the functionality of Nmap. They are started by the command -sC or -A - discovery
Scripts of this category collect accounting, registration and statistical data about the investigated system. - dos
These scripts test the system under investigation for vulnerabilities to denial of service attacks - exploit
Nmap will try to exploit some known vulnerabilities - external
These scripts send information to third-party databases or resources, for example: whois, virus total, robtex, geoplugin, ipinfo, etc. for more information about the target understudy - fuzzier
Scripts to send unexpected or randomized fields in each packet to the server software. Typically used to identify vulnerabilities or configuration errors. These are quite aggressive scripts, the use of which can lead to server failures - intrusive
This category contains the most aggressive scripts aimed at identifying many common vulnerabilities, both services and password auditing. Using scripts of this category leaves a lot of traces in the target system and, as a rule, will be regarded by administrators as an attempt of unauthorized interference - malware
These scripts scan the target system for malware infection and backdoors. - safe
Scripts from this category are designed to collect general information and research the network; they do not perform active actions aimed at identifying or exploiting vulnerabilities; they do not imply negative consequences for the operability of the target system - version
These are scripts for expanding the functionality of the versioning option, they cannot be run separately, they work as needed when selecting the versioning option (-sV) - vuln
Scripts checking for known vulnerabilities, the results will be shown only if they are detected
Using Nmap Scripts
Despite the huge number of available scripts, the logic of their use is quite simple and understandable. Moreover, in most cases, it is worth running a script-based scan along with port scanning, because some scripts work depending on a particular port state.
-sC
Script based scanning. The same as script = default, i.e. launches a scan using a set of scripts from the default category (as I wrote above, it is better to use the option – A )
–Script-help
Script or category information. If you select this option, you can specify a specific script or category, and the description of the script (category) and a link to the help page for it will be displayed on the screen.
–Script
category of scripts, file
Using this option, you can specify a specific script, or several scripts to run, separated by a comma, you can also specify a category (or several), or run a script from the specified file, for example:
sudo nmap –script whois- domain scanme.nmap.org
will run only the whois-domain script, and
sudo nmap –script default, safe, whois-domain scanme.nmap.org
will run all the scripts from the default and safe categories and the whois-domain script.
In general, the point is that you can combine categories and scripts as you need, there are no restrictions here, even if you’re something Wrong Nmap will tell you where the error is.
–Script-args name1 = value1, name2 = value2
This option allows you to pass arguments to scripts, for more fine-tuning. You can specify several arguments at once, listing them separated by commas; as a value, you can specify either fixed values or values from a file. For instance:
nmap -p 3306 --script mysql-audit --script-args mysql-audit.username = 'nselib/data/usernames.lst', mysql-audit.password = 'nselib/data/passwords.lst', mysql-audit .filename = 'nselib/data/mysql-cis.audit' no-jus.com
A similar command will check the settings of the MySQL database server in comparison with the CIS standards Oracle MySQL Benchmarks, while user names will be enumerated from the list from the usernames.lst file, and passwords will be sorted through the passwords.lst dictionary (both dictionaries are standard Nmap dictionaries , you can specify your dictionaries or separately specify the desired values).
Note:
Please note that I did not put spaces after commas, this is necessary so that Nmap understands which arguments belong to which option, this happens because the shell interprets each element separately. You can put spaces, but then you need to enclose the argument groups in quotation marks so that the interpreter interprets it as a single object, for example:
–script-args “ mysql-audit.username = ‘nselib/data/usernames.lst’, mysql-audit.password = ‘nselib/data/passwords.lst’, mysql-audit.filename = ‘nselib/data/mysql-cis.audit’ “
Time and Performance Management Options
Some types of scans take a lot of time, this can be due to a large number of tests or, for example, due to the settings of the firewall of the target. And, although, Nmap is trying to optimize the scan, but this process, to some extent, can be controlled. We will not consider manual time management, because it is too precise and quite complex element. We will deal with the use of time management settings templates. The template is set by the parameter:
- -T pattern
There are 6 templates themselves, you can choose them just by specifying a number from 0 to 6:
- paranoid (paranoid) (0) – used to bypass IDS i.e. intrusion detection systems;
- sneaky (sly) (1) – similar to the previous one;
- polite (polite) (2) – reduces the scanning intensity in order to reduce the consumption of bandwidth and machine resources;
- normal (3) – the mode used by default;
- aggressive (aggressive) (4) – mode of increased scanning intensity, demanding on speed and reliability of the connection;
- insane (5) – the fastest and most inaccurate mode
Nmap Firewall Bypass
The issue of bypassing protection and filtering is very extensive and controversial. All intrusion detection systems are constantly evolving and improving, so you should understand that there is no kind of magic recipe or a single algorithm for bypassing the firewall or other means of protection, each new situation is somewhat unique, and therefore, the directness of hands to a greater extent solves it, and even more experience and skills, but this article is not about this, but about Nmap. The developers took care of us and included in the program components that allow you to fool the means of protection:
- -f Packet fragmentation. When this option is enabled, Nmap will use small fragmented IP packets for all types of scans. This means that the TCP header will be split into parts, and these parts will be sent to the target in various packets, in such a situation there is a possibility that the filter simply does not understand what we want to do, and therefore will not respond. By default, Nmap breaks packets into 8-byte portions. This value can be set manually using the –mtu option (size must be a multiple of 8)
- -D dummy_host1, dummy_host2, dummy_host3, ME, dummy_host5
Scan using dummy hosts. For the purpose, it will look like it is scanned by all the hosts listed by you, while it will be quite difficult to understand where the real scan came from. Fictitious hosts must be specified with a comma, without spaces. You can set the ME parameter to what your real address will be in the list if this parameter is not specified, Nmap will put it randomly - –Data-length number
This option adds the specified number of bytes to the packet. Sometimes confusing filter systems - –Spoof-mac MAC Address
Substitute mac address. You can specify the desired mac address as a value, if you specify 0, a random mac will be generated, you can also specify a prefix or manufacturer name (a list of manufacturer prefixes is in the nmap-mac-prefixes file in the program package) then Nmap will use the prefix for the first part mac addresses and random value for second
Nmap Output Results
If you do not specify any parameters for outputting results, Nmap will exit the received data in the terminal. This is quite acceptable for scanning a single target, but it is not always convenient (or rather, always not convenient) for the analysis of large amounts of data. For our convenience, the developers made it possible to save the results immediately to a file, and there are several options:
- -oN file_name
Standard output. Scan data will be saved to the specified file in the form in which we see it in the terminal - -oX filename
XML output. The format is convenient for subsequent processing of results by third-party parsers or ZenMap - -oG file_name
Grepable output. With this output, the data of each host will be displayed on one line, it is needed if there is a need to use the lines grep, cut, etc. to process the utility with the command. - –Resume file_name
Continue the interrupted scan. If the scan, for whatever reason, was not completed, but its results were saved to a file (only -oN or -oG), you can continue it from the moment you finish with the command: nmap –resume file_name. Other options do not need to be set, scanning continues with the same options with which it was originally started
Various Nmap Options
- -6
Enable IPv6 scanning. With this scan, the same options are used as with the usual one, with the difference that the IP address must be specified in IPv6 format - -A
Aggressive scan options. As I mentioned earlier, it runs OS detection (-O), scan with target, version detection (-sV), script scan (-sC) and trace (–traceroute) - -v
Increase verbal level. When this option is enabled, more information will be displayed on the screen (and in the results) i.e. it will be more detailed. With a long scan, the approximate completion time will be shown, and the results will be displayed as they are received, and not after the scan is completed.
Nmap command examples
Nmap Scan a single host or an IP address (IPv4)
### Scan a single ip address ###
nmap 192.168.1.1
## Scan a host name ###
nmap exmple.com
## Scan a host name with more info###
nmap -v exmple.com
The output will show you some interesting open port and the MAC Address
Scan multiple IP address or subnet (IPv4)
nmap 192.168.1.1 192.168.1.2 192.168.1.3
## works with same subnet i.e. 192.168.1.0/24
nmap 192.168.1.1,2,3
## You can scan a range of IP address too:
nmap 192.168.1.1-20
## You can scan a range of IP address using a wildcard:
nmap 192.168.1.*
## Finally, you scan an entire subnet:
nmap 192.168.1.0/24
Read lists of hosts/networks from a file (IPv4)
The option allows you to read the list of target systems using a text file.
This is use of the -iL ul to scan a large number of hosts/networks.
Create a text file as follows:
Your Text file should look like this ( Test.txt )
facebook.com
Yahoo.com
192.168.1.0/24
192.168.1.1/24
10.15.23.7
localhost
Lets say the text file is in tmp here is your commend
nmap -iL /tmp/test.txt
Excluding hosts/networks (IPv4)
When scanning a large number of hosts/networks you can exclude hosts from a scan:
nmap 192.168.1.0/24 --exclude 192.168.1.5
nmap 192.168.1.0/24 --exclude 192.168.1.5,192.168.1.254
OR exclude list from a file called /tmp/exclude.txt
nmap -iL /tmp/scanlist.txt --excludefile /tmp/exclude.txt
Turn on OS and version detection scanning script (IPv4)
The results of a scan might determine that a machine is listening on port 80, without knowing its corresponding OS and Web Server version makes the task of attempted compromise a “shot in the dark” methodology.
NMap solve this dilemma by using OS and Version detection. The following commands:
nmap -A 192.168.1.254
nmap -v -A 192.168.1.1
nmap -A -iL /tmp/scanlist.txt
Check if a host/network is protected by a firewall
nmap -sA 192.168.1.254
nmap -sA exmple.com
Scan a host when protected by the firewall
nmap -PN 192.168.1.1
nmap -PN exmple.com
Scan an IPv6 host/address
The -6 option enables IPv6 scanning. The syntax is:
nmap -6 IPv6-Address-Here
nmap -6 exmple.com
nmap -6 2607:f0d0:1002:51::4
nmap -v A -6 2607:f0d0:1002:51::4
Scan a network and find out which servers and devices are up and running
This is known as host discovery or ping scan: nmap host discovery
nmap -sP 192.168.1.0/24
Sample outputs:
Host 192.168.1.1 is up (0.00035s latency).
MAC Address: BC:AE:C5:C3:16:93 (Unknown)
Host 192.168.1.2 is up (0.0038s latency).
MAC Address: 74:44:01:40:57:FB (Unknown)
Host 192.168.1.5 is up.
Host nas03 (192.168.1.12) is up (0.0091s latency).
MAC Address: 00:11:32:11:15:FC (Synology Incorporated)
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.80 second
Display the reason a port is in a particular state:
nmap --reason 192.168.1.1
nmap --reason exmple.com
Only show open (or possibly open) ports :
nmap --open 192.168.1.1
nmap --open exmple.com
Show all packets sent and received
nmap --packet-trace 192.168.1.1
nmap --packet-trace exmple.com
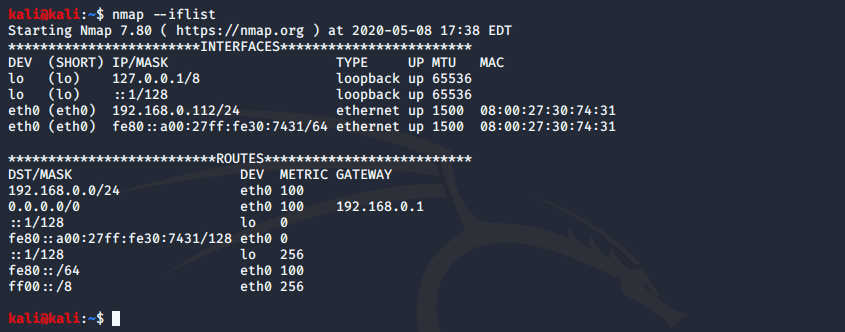
Show host interfaces and routes
This is useful for debugging (IP command or route command or netstat command like output using Nmap)
nmap --iflist
Sample outputs:
nmap port scan example
Scan specific ports
map -p [port] hostName
## Scan port 80
nmap -p 80 192.168.1.1
## Scan TCP port 80
nmap -p T:80 192.168.1.1
## Scan UDP port 53
nmap -p U:53 192.168.1.1
## Scan two ports ##
nmap -p 80,443 192.168.1.1
## Scan port ranges ##
nmap -p 80-200 192.168.1.1
## Combine all options ##
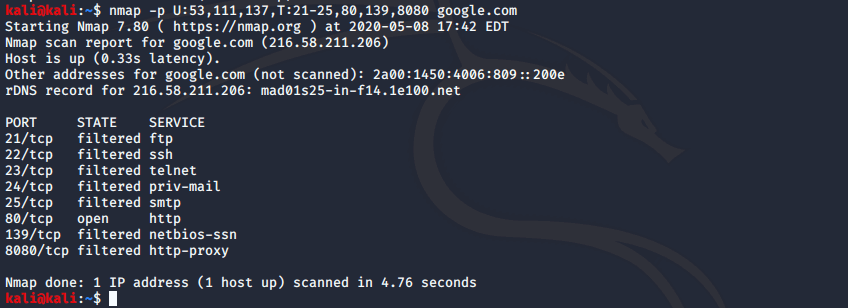
nmap -p U:53,111,137,T:21-25,80,139,8080 192.168.1.1
nmap -p U:53,111,137,T:21-25,80,139,8080 server1.exampl.com
nmap -v -sU -sT -p U:53,111,137,T:21-25,80,139,8080 192.168.1.254
## Scan all ports with * wildcard ##
nmap -p "*" 192.168.1.1
## Scan top ports i.e. scan $number most common ports ##
nmap --top-ports 5 192.168.1.1
nmap --top-ports 10 192.168.1.1
Sample outputs:
Scan all your devices/computers for open ports ever
nmap -T5 192.168.1.0/24
nmap os detection example
You can identify a remote host apps and OS using the -O option:
nmap -O 192.168.1.1
nmap -O --osscan-guess 192.168.1.1
nmap -v -O --osscan-guess 192.168.1.1
detect remote services (server/daemon) version numbers:
nmap -sV 192.168.1.1
Scan a host using TCP ACK (PA) and TCP Syn (PS) ping
If firewall is blocking standard ICMP pings, try the following host discovery methods:
nmap -PS 192.168.1.1
nmap -PS 80,21,443 192.168.1.1
nmap -PA 192.168.1.1
nmap -PA 80,21,200-512 192.168.1.1
Scan a host using IP protocol ping
nmap -PO 192.168.1.1
Scan a host using UDP ping
This scan bypasses firewalls and filters that only screen TCP:
nmap -PU 192.168.1.1
nmap -PU 2000.2001 192.168.1.1
Find out the most commonly used TCP ports using TCP SYN Scan
### Stealthy scan ###
nmap -sS 192.168.1.1
### Find out the most commonly used TCP ports using TCP connect scan (warning: no stealth scan)
### OS Fingerprinting ###
nmap -sT 192.168.1.1
### Find out the most commonly used TCP ports using TCP ACK scan
nmap -sA 192.168.1.1
### Find out the most commonly used TCP ports using TCP Window scan
nmap -sW 192.168.1.1
### Find out the most commonly used TCP ports using TCP Maimon scan
nmap -sM 192.168.1.1
Scan a host for UDP services (UDP scan)
Most popular services on the Internet run over the TCP protocol. DNS, SNMP, and DHCP are three of the most common UDP services. Use the following syntax to find out UDP services:
nmap -sU nas03
nmap -sU 192.168.1.1
Output:
Starting Nmap 7.01 ( https://nmap.org ) at 2015-12-15 12:27 EST
Stats: 0:05:29 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 32.49% done; ETC: 01:09 (0:11:26 remaining)
Interesting ports on nas03 (192.168.1.12):
Not shown: 995 closed ports
PORT STATE SERVICE
111/udp open|filtered rpcbind
123/udp open|filtered ntp
161/udp open|filtered snmp
2049/udp open|filtered nfs
5353/udp open|filtered zeroconf
MAC Address: 00:11:32:11:15:FC (Synology Incorporated)
Nmap done: 1 IP address (1 host up) scanned in 1099.55 seconds
Scan for IP protocol
This type of scan allows you to determine which IP protocols (TCP, ICMP, IGMP, etc.) are supported by target machines:
nmap -sO 192.168.1.1
Scan a firewall for security weakness
The following scan types exploit a subtle loophole in the TCP and good for testing security of common attacks:
## TCP Null Scan to fool a firewall to generate a response ##
## Does not set any bits (TCP flag header is 0) ##
nmap -sN 192.168.1.254
## TCP Fin scan to check firewall ##
## Sets just the TCP FIN bit ##
nmap -sF 192.168.1.254
## TCP Xmas scan to check firewall ##
## Sets the FIN, PSH, and URG flags, lighting the packet up like a Christmas tree ##
nmap -sX 192.168.1.254
Scan a firewall for packets fragments:
The -f option causes the requested scan (including ping scans) to use tiny fragmented IP packets. The idea is to split up the TCP header over
several packets to make it harder for packet filters, intrusion detection systems, and other annoyances to detect what you are doing.
nmap -f 192.168.1.1
nmap -f fw2.nixcraft.net.in
nmap -f 15 fw2.nixcraft.net.in
## Set your own offset size with the --mtu option ##
nmap --mtu 32 192.168.1.1
Cloak a scan with decoys
The -D option it appear to the remote host that the host(s) you specify as decoys are scanning the target network too. Thus their IDS might report 5-10 port scans from unique IP addresses, but they won’t know which IP was scanning them and which were innocent decoys:
nmap -n -Ddecoy-ip1,decoy-ip2,your-own-ip,decoy-ip3,decoy-ip4 remote-host-ip
nmap -n -D192.168.1.5,10.5.1.2,172.1.2.4,3.4.2.1 192.168.1.5
Scan a firewall for MAC address spoofing:
### Spoof your MAC address ##
nmap --spoof-mac MAC-ADDRESS-HERE 192.168.1.1
### Add other options ###
nmap -v -sT -PN --spoof-mac MAC-ADDRESS-HERE 192.168.1.1
### Use a random MAC address ###
### The number 0, means nmap chooses a completely random MAC address ###
nmap -v -sT -PN --spoof-mac 0 192.168.1.1
How to save output to a text file
The syntax is:
nmap 192.168.1.1 > output.txt
nmap -oN /path/to/filename 192.168.1.1
nmap -oN output.txt 192.168.1.1
Vulnerability Scan Using Nmap and Vulscan
Nmap can quite successfully be used as a vulnerability scanner. To do this, you need to download the Vulscan script ( https://github.com/scipag/vulscan ) which will greatly expand the standard capabilities of Nmap.
git clone https://github.com/scipag/vulscan scipag_vulscan
ln -s `pwd`/scipag_vulscan/usr/share/nmap/scripts/vulscan
Vulnerability databases are already integrated into the script:
- scipvuldb.csv – https://vuldb.com
- cve.csv – https://cve.mitre.org
- securityfocus.csv – https://www.securityfocus.com/bid/
- xforce.csv – https://exchange.xforce.ibmcloud.com/
- expliotdb.csv – https://www.exploit-db.com
- openvas.csv – http://www.openvas.org
- securitytracker.csv – #
- osvdb.csv – http://www.osvdb.org
This script is launched just like any other script, the only thing to remember is that it needs to be combined with the versioning command (-sV):
nmap -sV --script= vulscan/vulscan.nse 10.0.1.14
Additionally, for the Vulscan script, the –script-args command can pass additional arguments:
- vulscandb = database
Use the specified database (from the list above), by default all existing databases will be used - –Script-args vulscaninteractive = 1
Enable interactive mode
Based on the results of the work of this script, Nmap will show a list of vulnerabilities, i.e. which vulnerability is found and where it is detected, but what to do next is already a question of this article.
On this, our general acquaintance with Nmap can be considered finished, perhaps at first it will seem to you that it is a little difficult, but practice using different options and arguments of this utility and you will see that it is simple, but as efficient as possible and do not forget to return to us to find out very much more a lot of new.

Leave a Reply