Intercepter-NG is an Android penetration testing app.
by using Intercepter-NG you will be able to intercept and analyze un-encrypted communications over WiFi network.
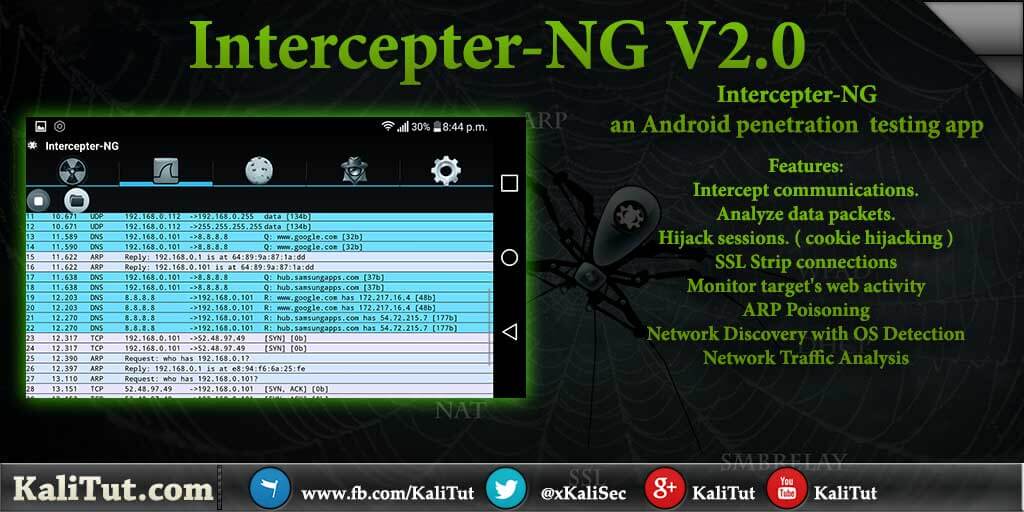
Intercepter-NG is a network toolkit for various types of IT specialists and an easy-to-use application to intercept communication.
it’s an MiTM attacks tool , you can perform different kinds of MiTM attacks using this android app
Requirement:
- Android 2.3.3+
- Root
- Busybox
Intercepter-NG v2.0 Features:
- Intercept communications.
- Analyze data packets.
- Hijack sessions. ( cookie hijacking )
Session hijacking, also known as TCP session hijacking and cookie hijacking , is a method of taking over a Web user session by surreptitiously obtaining the session ID and masquerading as the authorized user.
- SSL Strip connections.
SSLStrip is a type of MITM attack that forces a user browser into communicating with an adversary in plain-text over HTTP, it simply watch for HTTPS links and redirects, then map those links into look-alike HTTP
- Monitor target’s web activity
- ARP Poisoning
ARP stand for “Address Resolution Protocol” this type of attack sends falsified ARP messages over a local area network to link the attacker MAC address with the IP address of a legitimate computer or server on the network.
- Network Discovery with OS Detection
- Network Traffic Analysis
- Passwords Recovery
- Files Recovery
How to use intercepter ng
Installation
- Download Intercepter-NG V2.0 from Github
https://github.com/intercepter-ng/intercepter-ng.github.io - Install Busybox from Google Store
Remember your Android phone must be rooted
Install and open the app click on the Radar icon in the upper left corner of IntercepterNG.

3.After you click on the radar icon It will scan the network and list all the connected devices
4 Now select the Devices you want to spy on from the list , it will show the operating system next to the IP address
- Click the Play icon on the top right then Select the Settings icon
Now tick the check box of Save pcap session and change the memory location to SD Card if you want the file to be saved on your SD card.

6.Return to main menu and then select the play button
now it will start downloading packs

7 To see graphical capturing of data click the Wireshark icon click the play button
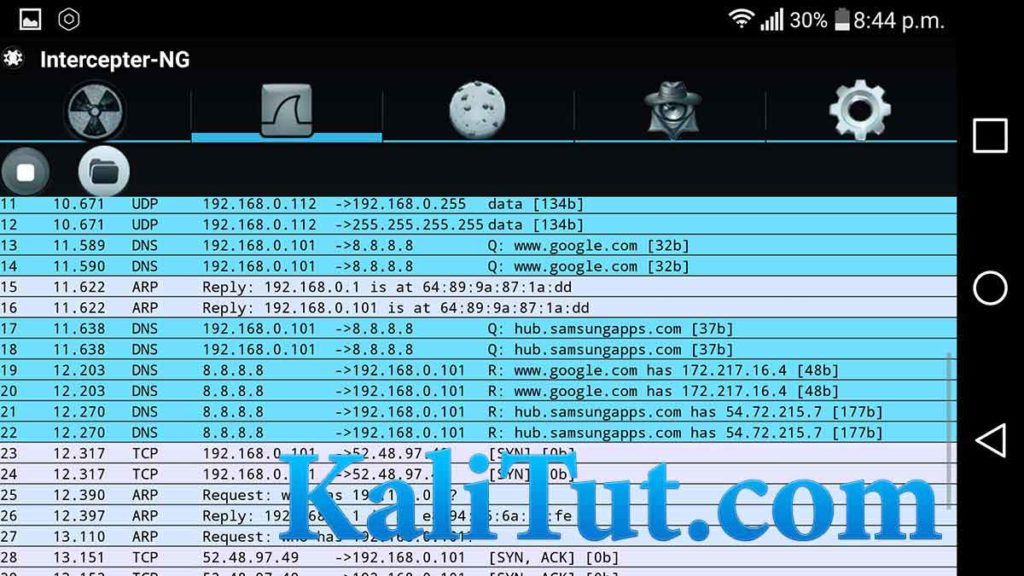
8.Click the cookies icon and wait for the cookies to load then select any one of the IP shown it will load the web page your victim are in.
Last update: 16.04.2020
Intercepter-NG [Android Edition] v2.5
- Automatical Save&Restore of routing rules and iptables
- Preloaded results of the last scan + prescan on startup
- Text resize by gestures, tab switch by swipes, vibro reactions
- OS Fingerprinting system based on Satori format
- Port Scan upgraded to X-Scan with EternalBlue checker
- Scanning engine is greatly improved
- HSTS Spoofing with improved sslstrip
- Self-diagnosis for troubleshooting
- LOTS of other fixes and improvements
- UI updated
- libpcap updated to 1.9.1 (for API >=24)
- No more SuperSU and Busybox dependencies -> Magisk
- Android support from 4.4 up to 10+ (x86, ARM, ARMv8)

The two basic functions of Intercepter-NG They are:
1. interception traffic data from, such as passwords, files, correspondence
2. Interception of traffic through MiTM attacks.
Scan Mode
Scanning mode is active by default after starting tool.
The main objective of this regime is in the ARP
scanning to identify other members of the network (computers,
phones, other network equipment), for which you need to run
ARP Scanning.
26.09.2016 – Intercepter-NG [Android Edition] v2.0
Added:
+ SelectCopy packet data in RAW Mode
+ Pcap filter on reading *.pcap
+ Save cookie button
+ Show HTTP Requests
+ HTTP Injects
+ ARP Cage
Updated:
A lot of improvements and fixes
– ResurrectionGallery
Tested on 4/5/6/7 Android. Should also work on 2/3.
PS: Don't forget (!) to install SuperSU and BusyBox!
07.09.2016 – Intercepter-NG v1.0
Added:
+ FATE: FAke siTE + FAke updaTE
+ X-Scan (network security scanner)
+ Bruteforce Mode: VNC, VMWARE, RDP
+ Reverse Shell Inject
Updated:
Raw Mode
Multiply Extra SSL Ports
A lot of fixes and improvements.
09.11.2015 – Intercepter-NG [Android Edition] 1.7
Added:
+ Android 5 support
+ Portrait mode compatibility
+ Cookie Killer
+ Forced Download
+ Fast poisoning
+ Address bar in Cookie Viewer
+ Data view in Raw Mode
+ Updated scanning engine
+ Fixed sdcard issues
+ Improvements and fixes
29.07.2015 – Intercepter-NG v0.9.10
Added:
+ Group Policy Hijacking
+ Forced Download and JS Inject
+ HSTS Spoofing
+ Traffic Changer
+ Smart Scan: NBNS + Bonjour resolve + hostnames cache.
+ Bruteforce mode: SMTP TLS, POP3 TLS, TELNET and Single Mode.
+ Auto ARP Poison
Updated:
SSL Strip improved.
SSL MiTM rewritten:
+ Fast and stable
+ New certificates generation algorithm.
+ Cookier Killer
+ iOS Killer (iCloud, Instagram, VK)
+ Black and White lists
A lot of fixes and improvements.
can I hack whatsapp with interceptor ng
29.07.2014 – Intercepter-NG v0.9.9
Added:
+ LDAP Relay
+ Heartbleed exploit
+ Java injection
+ Plugin detector
+ Bruteforce Mode: FTPIMAPPOP3SMTPSMBSSHLDAPHTTP
+ TFTPSMB2 resurrection
+ TelnetRshRloginRexec logging
+ PPTPPPPoE: PAPCHAP-MD5MS-CHAPMS-CHAPv2 Auth
+ PostgreSQL PlainMD5 Auth
+ MS-SQL Server Auth
+ MongoDB Auth
+ Wine support
+ New skin
Improvements and fixes
11.06.2013 – Intercepter-NG v0.9.8
Added:
+ SMB Hijacking
+ NTLM Grabber in WPAD MiTM
+ Built-in brutforce of hashes via JTR
+ More accurate OS detection
+ Port Scanner
+ POP3 NTLM Auth
+ RADIUS Auth
+ Kerberos Auth (rc4-hmac, aes256-cts-hmac-sha1-96)
+ Kerberos Downgrade (aes256->rc4)
+ Custom .exe for smbrelay
+ MAC Whitelist in DHCP MiTM
Updated:
SMBRELAY CODE FIXED!!!
sslstrip moved from 80 to 8080 port
SMBv2 support
IDN support
OUI base updated
Resurrection mode updated
countless improvements and fixes
15.04.2013 – Intercepter-NG v0.9.7
Added:
+ SSH MiTM
+ IP Forward
+ SaveLoad Cookies
Updated:
WPAD SOCKS4 -> PROXY
fixes and improvements…
22.03.2013 – Intercepter-NG v0.9.6
Added:
+PPPoE PAP Auth
+NBNSLLMNR Spoofing
+Replaying sniffed cookies in browser
+PCAP Over IP
Updated:
DNS Spoofing by mask (*)
WPAD socks support HTTP injection
Expert Mode (dns cache ttl, arp scan timeout, stop injection on nbns)
fixes and improvements…
05.12.2012 – Intercepter-NG [Android Edition] 1.0 + Intercepter-NG [Console Edition] 0.5
Completely new [Android Edition] !
18.09.2012 – Intercepter-NG v0.9.5 + Intercepter-NG [Console Edition] 0.4
Added:
+SSLStrip: Cookie Killer
+DNS Spoofing
+MRA MD5 Auth
+HTTP Auth Heur
+Multiselecting of captures
+Support of pcapng (new wireshark format)
+Expert Mode
+ARP Cage
Updated:
ARP Scan according to netmask
RAW Mode
Resurrection Mode (http proxy support)
HTTP Injection
SSL MiTM + SSLStrip
Countless improvements and fixes
—
manual control of arp poison in CE
and some updates from win version, see CHANGELOG
06.08.2012 – Intercepter-NG v0.9.4 + Intercepter-NG [Console Edition] 0.3
Added:
+IPv6 support
+New feature: http injection
Updated:
The speed of analysis is now 5 times faster
RAW Mode updated
Improvements and fixes
—
New RAW Mode for Console version and a lot of updates
see CHANGELOG for details
18.06.2012 – Intercepter-NG [Console Edition] 0.2
Added:
+ new passwords dissectors
+ grabbing messages ICQAIMJABBERYAHOOMSNIRCMRA
+ recovering files from SMB
+ resizing support
+ locale support via env variable LC_ALL
+ arp code improved
+ MacOS X build
01.06.2012 – Intercepter-NG v0.9.3 + Intercepter-NG [Console Edition] 0.1
Added:
+UAC Manifest added to .exe
+New Resurrection Mode – reconstruction of HTTPFTPSMBIMAPPOP3SMTP files
+Cookie grabber added
+Visit new Wiki page
Updated:
Major update of sslstripping code
openssl+zlib linked statically
IRC moved to Messengers Mode
Updated WiFi Mode and improved MiTMs code
RAW mode updated
Intercepter converts Raw IP Data captures to Ethernet frames
a lot of small changes
New Intercepter Console Edition is available now.
It works on any *nix including IOS and Android.
Special thanks to nimmox for testing and building android version.
Enjoy!
17.04.2012 – Intercepter-NG v0.9.2
Added:
+New SMBRelay MiTM with NTLMv2 support (watch video tutorial).
+NTLM Challenge+Response grabbing (NTLMSSP). Bruteforce it with C&A.
Updated:
*Raw Mode updated (saving .pcap dumps, astronomical time display)
04.04.2012 – Intercepter-NG v0.9.1
Added:
+New WPAD MiTM (watch video tutorials).
+Built-in Socks4 server added
Updated:
*RAW Mode updated
*Minor fixes
11.11.2011 – Intercepter-NG v0.9
Next generation of Intercepter has come.
Besides a new GUI, countless improvements have been made.
The whole process of MiTM attacks is now completely automated.
Added:
+NAT added to Intercepter
+Gateway discovering feature
+Smart Scan with OS detection
+MSNMRA Parsers updated
+Raw Mode is in the style of Wireshark
+Loading pcap dumps by Drag&Drop
Removed:
-MAC Changer and SMTPPOP3 grabber
-Gadu-Gadu support