In this article, we will analyze what WiFi card specifications are important for a security audits of WiFi networks, what indicators to study before buying WiFi, what you can learn about a WiFi adapter connected to your computer, and a lot of attention will be paid to virtual wireless interfaces.
Monitor Mode, Wireless Injections, Access Point Mode (AP)
The most important feature required for hacking WiFi networks is whether the wireless card supports monitor mode. To understand what a monitor mode is, you need to turn on the adapter’s operation in the “normal” (it is called “managed”) mode: the wireless card sends data to the Access Point and receives data from it that is intended for this wireless card. In monitor mode , the wireless card is not connected to a specific access point, it “listens”, i.e. It receives absolutely all wireless data packets that “fly” on the radio at the frequency that the wireless adapter is currently tuned to.
Monitor mode is the ability of a WiFi card to receive any packets that are available in the reach range at its frequency.
If the wireless card does not support the monitor mode, then it is practically useless for wireless pentesting (unless, with the help of it, you can perform online attacks that have very little efficiency).
Those. If the wireless adapter has a monitor mode, it can intercept a four-step handshake, with which you can later crack the WiFi password.
Note: throughout the article, I will use such terms as “Access Point”, “Station”, etc., these concepts are disclosed in the section ” Terms of WiFi networks .”
A handshake can be intercepted at the moment when the client connects to the access point, and this can happen very rarely. To speed up this process, a deauthentication attack is used . To perform it, it is necessary for the adapter to be able to make wireless injections.
It is important to know that having a monitor mode ≠ ability to make wireless injections .
Those. Some wireless cards will be able to intercept a handshake, but will not be able to disconnect clients (perform a deauthentication attack).
And that is not all.
Programs such as Fluxion and WiFi Pumpkin require WiFi cards that support the Access Point mode, i.e. AP mode . In the Access Point mode, the wireless card works as a wireless router: stations can be connected to it.
The wireless card can support the monitor mode, be able to make wireless injections, but not have the Access Point mode. The capabilities of WiFi cards depend on the chipset and driver. usb wifi adapter monitor mode
WiFi Adapter Chip and WiFi Adapter Driver for Linux
As already mentioned, exactly which modes the wireless adapter supports depends on:
- chipset installed in it
- Linux driver capabilities (since in most cases this OS is used, since it allows you to perform all of the possible wireless attacks)
A large amount of information about chipsets and drivers is collected in two tables:
- Table of wireless adapters / chipsets (Wireless adapters / Chipset table)
- Table of existing Linux drivers (Existing Linux Wireless drivers)
The cap of the first table:
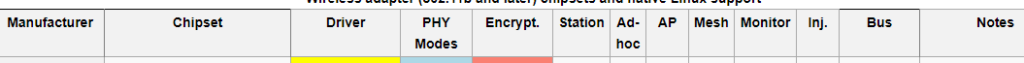
Entries mean the following:
- Manufacturer (manufacturer)
- Chipset (chipset – it is for this field that we will look for information about the device we are interested in)
- Driver (Driver)
- PHY Modes (PHY modes, i.e. a / b / g / n / ac)
- Encrypt . (types of supported encryption)
- Station (ability to act as a station)
- Ad-hoc
- AP (ability to act as an access point)
- Mesh
- Monitor (monitor mode support)
- Inj. (ability to make wireless injections)
- Bus (connection type: USB or something else)
- Notes (Notes)
How to find out if the chip supports monitor mode and wireless injection
It is convenient to search in this table according to the chipset installed in the Wi-Fi card. In the first place for hacking Wi-Fi networks are important fields: AP , Monitor and Inj.
For example, take a card like Panda Wireless PAU09 N600 . We are looking for information about the chipset installed in it: you usually have to google, sometimes detailed technical information can be found on the store’s website.
We find that the Ralink RT5572 chipset is installed in it. We are looking in the table “RT5572“:
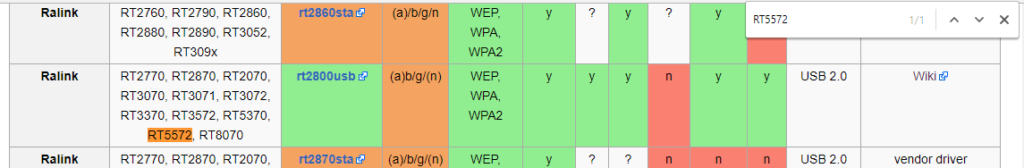
As you can see, supported by AP, Monitor and Inj – i.e. This card is perfect for wireless testing.
Take another card – Alfa AWUS036NHA . use Atheros AR9271 chipset. Looking for “AR9271”:

It is seen that all the necessary modes are also supported.
How to know Linux chipset and wireless card driver
Using the command
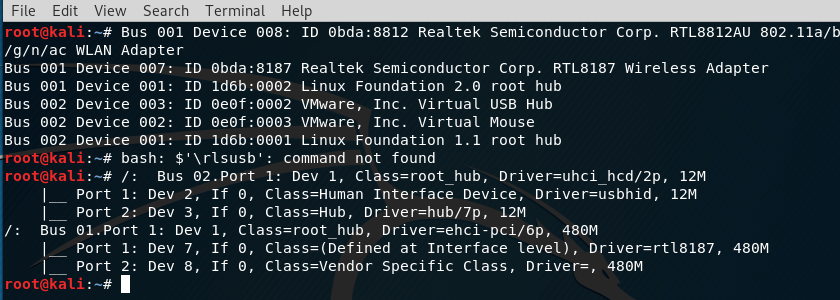
lsusb
You can find out the USB wireless chipset. A team
lsusb -t
You can see the driver of the wireless USB card:
The same information about the chipset and the driver (for both USB and embedded cards) can be viewed with the command:
airmon-ng
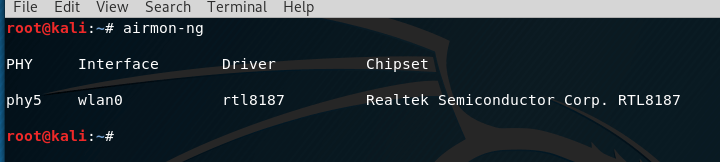
For integrated wireless cards, driver information can be seen in this way (look for the Kernel driver in use line
lspci -v
With lshw, you can see a variety of information about hardware:
sudo apt install lshw
sudo lshw
The chipset table does not contain information about all drivers. For example:
airmon-ng
PHY Interface Driver Chipset
phy0 wlan0 iwlwifi Intel Corporation Centrino Advanced-N 6235 (rev 24)
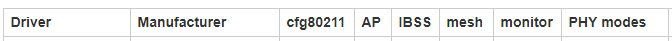
The wireless card uses the iwlwifi driver , which is missing from the first table. Referring to the second table , it has columns:
- Driver (Driver)
- Manufacturer (manufacturer)
- cfg80211 ( cfg80211 support available)
- AP (access point mode support)
- An IBSS (support an IBSS)
- mesh
- monitor ( monitor mode support)
- PHY modes (support for a/b/g/n/ac modes)
- Buses (connection type: USB or something else)
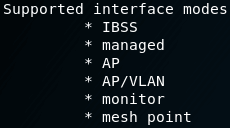
Iw list commandThe capabilities of your wireless hardware on your system can be found with the command:
iw list
It displays a lot of information. Pay attention to: Supported interface modes :
And one more example:
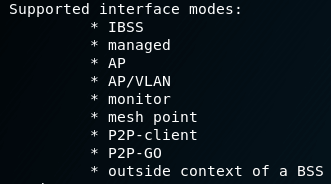
Here the main entries are monitor and AP .
- modes interface software (software interface modes)
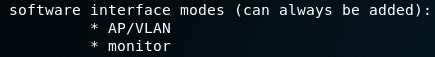
- valid interface combinations (allowed interface combinations):
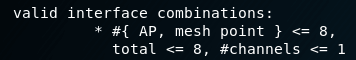
Check, monitor mode, wireless injection and AP in LinuxAbove, it was shown how to collect information about the modes it supports even before purchasing a wireless device and, based on this information, determine whether a WiFi card is suitable for Kali Linux. There are also commands to view the WiFi hardware capabilities of the device.
Now we will look at how to test in practice whether the monitor mode and other modes are supported by the specific WiFi card you have on your hands on the particular system to which you connected it .Connect your WiFi card to your computer: we will enter a series of commands that will confirm which modes it supports or does not support.
In order for the data to be accurate, it is necessary to close the programs that may interfere with our actions with wireless cards:
sudo systemctl stop NetworkManager
sudo airmon-ng check kill
Monitor mode check
Run the command
sudo iw dev
It should show the name of the wireless interface on your system. If nothing is displayed, then the wireless card is not connected, or the system for any reason cannot recognize your WiFi card.
In the information received, find the name of the wireless interface, for example, it could be wlan0 .
Next, follow the sequence of commands
sudo ip link set down
sudo iw set monitor control
sudo ip link set up
replacing with the real name of your wireless interface (mine is wlan0):
sudo ip link set wlan0 down
sudo iw wlan0 set monitor control
sudo ip link set wlan0 up
Run the command again.
sudo iw dev
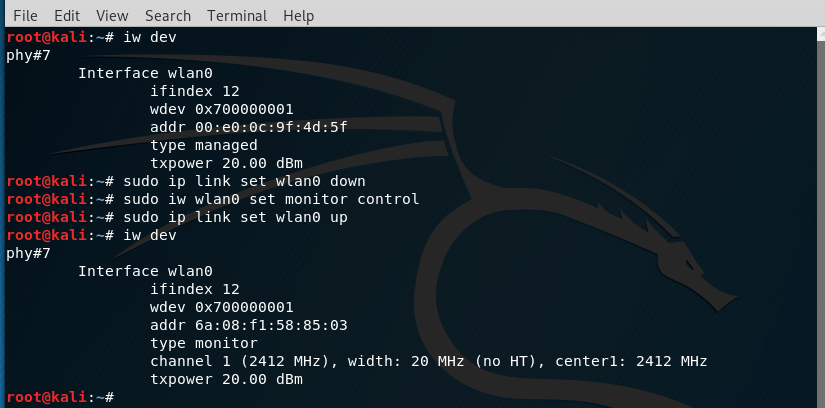
The type monitor indicates that the wireless card supports monitor mode.
Return to the controlled mode (do not rush with this – we will need the monitor mode to test the wireless injections):
sudo ip link set down
sudo iw set type managed
sudo ip link set up
For the wlan0 interface , the real commands look like this:
sudo ip link set wlan0 down
sudo iw wlan0 set type managed
sudo ip link set wlan0 up
Wireless injection test
Check if the wireless card supports injection (injection) on the wlan0 network interface (if necessary, replace the interface name with the name on your system):
sudo aireplay-ng -9 wlan0
The result of the command:
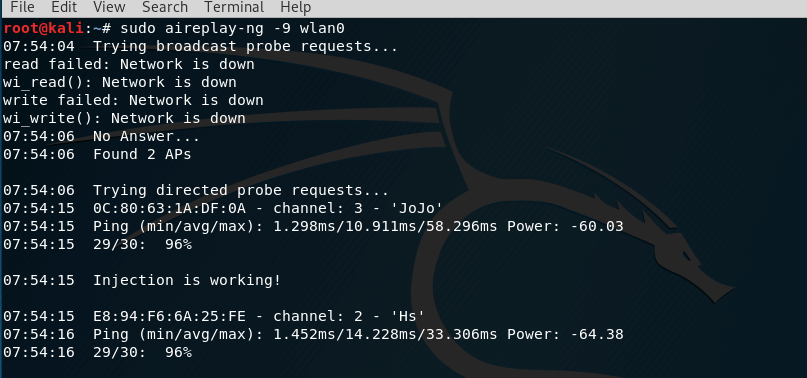
The main thing in the output is the string Injection is working! which says that the injection works.
Checking access point mode (AP, master mode)
The access point mode is also called the master mode.
The access point mode is required for social engineering-oriented programs that create access points (an evil twin attack, a fraudulent access attack). This, first of all, such programs as: Fluxion , airgeddon , WiFi Pumpkin , create_ap and other similar.
To check whether your WiFi card can act as an access point, we will try to create a software access point. To do this, create a hostapd.conf file with the following contents (replace wlan0 with the name of the You can be sure that the quality is set to AP ( type AP string ): being checked):
interface=wlan0
driver=nl80211
ssid=TestAP
channel=1
Save and close it, start hostapd as follows:
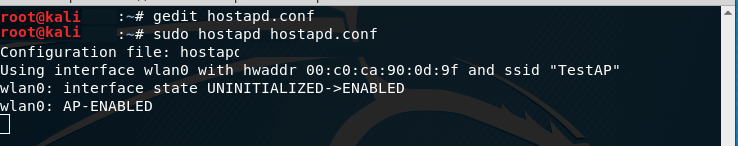
sudo hostapd hostapd.conf
In the terminal, the following should be displayed:
Configuration file: hostapd.conf
Using interface wlan0 with hwaddr 00:c0:ca:90:0d:9f and ssid "TestAP"
wlan0: interface state UNINITIALIZED->ENABLED
wlan0: AP-ENABLED
If everything is so, then with the help of another device (phone, tablet) look for a new one in the list of available networks, named TestAP.
This access point does not route traffic (since we have not made the appropriate configuration). This means that if you connect to it, you will not have an Internet connection. However, it should still be visible as available networks.
If everything went smoothly and you can see the new wireless network, it means that your driver supports the master mode with hostapd.
sudo iw dev
You can be sure that the quality is set to AP ( type AP string ):
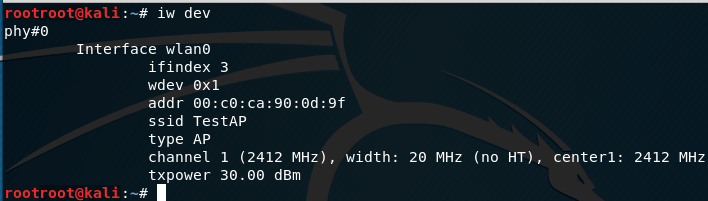
To stop hostapd, just press ctrl + c.
Verify the functionality of the virtual interface
Fluxion can use one wireless card with virtual network interface support, or two wireless cards at the same time. This means that you do not need a virtual interface if you have a second wireless adapter. If you went this way (two WiFi adapters), make sure that the selected interface supports injection, and the second interface supports the master mode (access point mode, discussed just above), it is needed to launch the Captive Portal attack ).
When fluxion uses one interface, a virtual network interface is required. This is due to the fact that some attacks, such as Captive Portal, require two different actions with wireless networks for successful execution: jamming the target AP and launching your own access point (rogue AP).
To do this, we need to create an additional interface from our main interface. First we need to select the interface with which we would like to work, and “reserve it” by setting it in monitoring mode (replace wlan0 with the name of the selected interface):
sudo ip link set wlan0 down #Deactivate the interface
sudo iw wlan0 set monitor control #Switch interface to monitor mode
sudo ip link set wlan0 up #Activate the interface
The above commands should not generate any output. If after starting any of the command something is displayed on the screen, it means that something is going wrong.
Next, we add a second virtual interface from the main interface:
sudo iw dev wlan0 interface add wlan0ap type monitor
Here:
- wlan0 is the name of the network interface present on your system
- wlan0ap is the name of the new interface, you can choose another arbitrary name
This command should not display anything on the screen; if any output is shown, then something goes wrong.
sudo iw dev
you can check that a second interface has really been added:
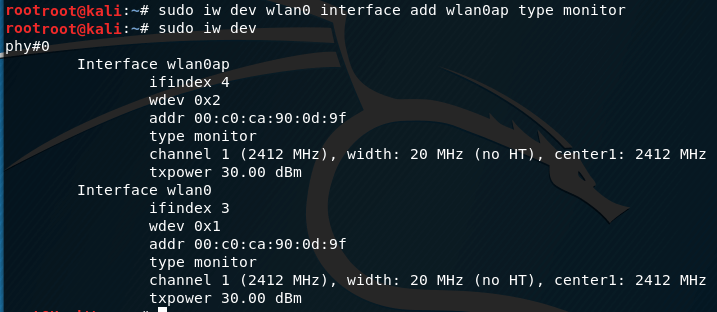
Now we have both interfaces ready and we will try to use them simultaneously.
When using virtual interfaces, there are usually the following limitations:
- both interfaces must be on the same frequency (i.e., the software TD rises at the same frequency at which the true TD is attacked)
- the interface to the AP mode can be combined with the interface in the monitor mode (i.e., after starting the software access point, the second interface is automatically transferred to the monitor mode)
As an experiment that everything works as described in theory, the main interface ( wlan0 in my example ) will launch a jammer, while the second interface ( wlan0ap in my case ) will launch a fraudulent access point.
We need to start by searching for a target for silencing, so let’s translate the main interface into monitor mode:
sudo ip link set wlan0 down
sudo iw wlan0 set monitor control
sudo ip link set wlan0 up
And on the main interface (wlan0), run airodump-ng :
sudo airodump-ng wlan0
Suppose I choose the MiAl network as the target, it is on the tenth channel (remember this) and has BSSID 50: 46: 5D: 6E: 8C: 20 (also remember it):
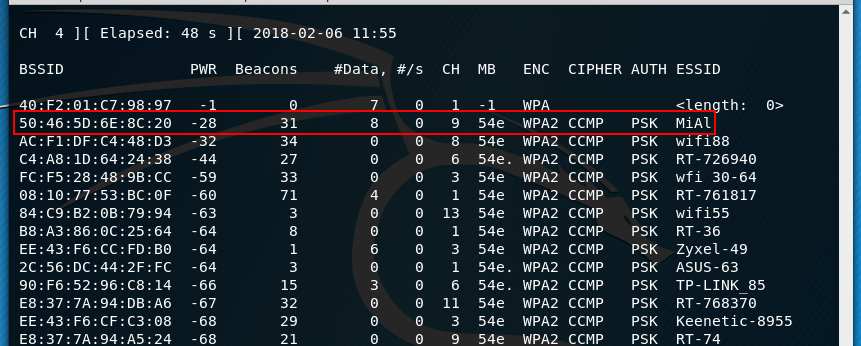
Let’s move on to create a new access point. To do this, create a hostapd.conf file with the following contents (note that we now use wlan0ap as the interface name — if you chose a different name for your wireless interface, use it; also notice that I changed the network name and set the ninth channel):
interface=wlan0ap
driver=nl80211
ssid=MiAl
channel=9
Run hostapd:
sudo hostapd hostapd.conf
sudo iw dev
You can view the current status of wireless interfaces:
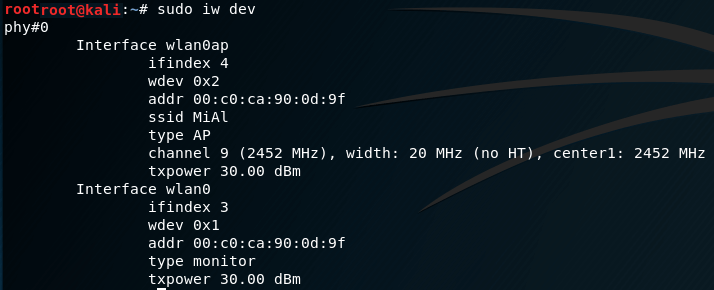
For deauthentication (muting) you can use, for example, mdk3 . On the main interface (wlan0 is mine), run mdk3 like this:
sudo mdk3 MAIN_INTERFACE d -c CHANNEL_TITLE_TD -t BSSID_Target_TD
In my case, the command looks like this:
sudo mdk3 wlan0 d -c 9 -t 50:46:5D:6E:8C:20
As a result, while mdk3 is working, it will be impossible to connect to the true access point, but the second AP with the same name will be visible, which can be freely connected without a password. And both of these operations are performed using a single Wi-Fi adapter.
If everything is normal, mdk3 and hostapd should work simultaneously without stopping and departures. If everything went well for you too, then fluxion will work fine with your wireless card.
What else you need to pay attention when buying Wi-Fi for Kali Linux
There are other characteristics of wireless cards that are important for wireless Pentesting:
- supported frequencies: Wi-Fi cards can work on one frequency (2.4GHz) or on two (2.4GHz and 5GHz)
- Supported protocols: Wireless cards can support various combinations of a / b / g / n / ac. Currently, the n protocol is already widely used, while ac is still not widely used.
- signal strength: powerful cards are better, but usually they have a larger size and a larger antenna, which is not suitable for everyone.
- the presence of an external antenna, the number of antennas: there may be one or more antennas; if the antenna is disconnected, you can connect a more powerful antenna or install a directional antenna.
Conclusion
Quite a lot of wireless cards are suitable for Kali Linux

Where is this table that you have screenshots from? Looks awesome, but with the stylesheet applied to this blog it's impossible to identify links without hovering over every bit of text. I did a search from inspecting elements on "wiki" and tried to do href but there are so many references, I am not patient enough to look through them all.
I’m also very interested in such compatibility table.