Due to the exponential growth of malicious code, much time and manpower are required for malicious code analysis. In particular, as the use of mobile devices increases, Android malicious codes are also steadily increasing. Automated malicious code analysis is becoming important as a way to deal with these explosive malicious codes. Analysts can use the CuckooDroid system developed on the same platform as the Cuckoo Sandbox system, a PC-based malware dynamic analysis platform, for dynamic analysis of malicious code in the Android environment.
CuckooDroid Overview
CuckooDroid is a platform for analyzing malicious code on Android. After 1.0 version was launched at the Black Hat Asia Conference in 2015, CuckooDroid was continuously developed and distributed until 2.0 version as of 2017.
In this issue, we introduce Sandbox concept, Cuckoo Sandbox, and CuckooDroid before explaining CuckooDroid, and run the malicious code sample actually obtained in the CuckooDroid analysis environment to confirm the analysis result.
Introduction Sandbox
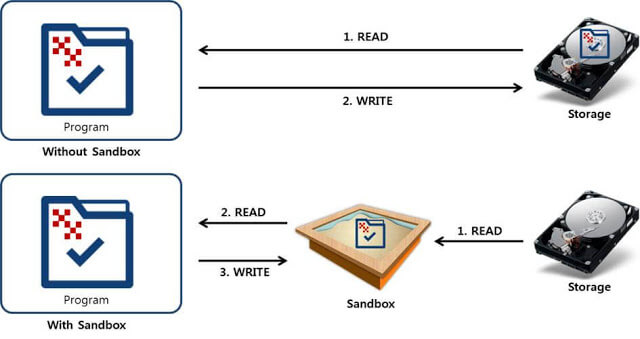
The Sandbox originally originated in a US home, and it means a place where sandboxes were made to provide space for children to play outside. In computer security, the Sandbox uses the term and place where it can play safely.
According to Wikipedia, Sandboxing is defined as ‘a technique to isolate a running program and is used to run untrusted programs’. Applying this concept to malicious code analysis can be defined as running an unknown application or file in an isolated environment and obtaining information about the program.
Sandboxing can be used to determine how malicious code affects a network or program. Therefore, static and dynamic analysis can be performed through sandboxing in the early stage to detect malicious code behavior.
However, Sandboxing uses a virtualization operating system, so it has traces that can be easily tracked. Therefore, malicious code may detect malicious code, and malicious code may not be executed normally or maybe bypassed, such as termination, and analysis may not be smooth.
What is Cuckoo?
Cuckoo is a project that has been started to automate and analyze malicious code quickly. To analyze PC malware, Cuckoo Sandbox was developed in 2010, and CuckooDroid, a Sandbox for Android malware analysis, was developed in 2012.
Cuckoo Sandbox is an automated tool for analyzing PC malware, allowing dynamic and static analysis. Dynamic analysis provides functions such as networking and changes to processes. Static analysis provides functions such as malicious code information, API call information, and resources. However, Cuckoo Sandbox has a limitation in Android malicious code analysis with PC-based analysis. So, we are providing the same CuckooDroid platform for Android as Cuckoo Sandbox platform. As shown in [Figure 3], we have an analysis process in Cuckoo Sandbox, and CuckooDroid is analyzed as shown in
CuckooDroid provides the same Android app launch and analysis as the Cuckoo sandbox analysis process.
CuckooDroid is a guest OS, an Android emulator that allows you to see the behavior and goes through a process similar to Cuckoo SandBox. Malicious apps can detect various actions such as encryption key extraction, SSL inspection, API call trace, and signature. The malicious behavior of malicious app can be grasped by the analysis result. CuckooDroid plays an important role in the initial analysis of Android because malicious behavior information can be grasped quickly in initial response when malicious application is infiltrated.
CuckooDroid Installation
Easy integration script:
git config --global user.email "[email protected]" git config --global user.name "Your Name" git clone --depth=1 https://github.com/cuckoobox/cuckoo.git cuckoo -b 1.2 cd cuckoo git remote add droid https://github.com/idanr1986/cuckoo-droid git pull --allow-unrelated-histories --no-edit -s recursive -X theirs droid master cat conf-extra/processing.conf >> conf/processing.conf cat conf-extra/reporting.conf >> conf/reporting.conf rm -r conf-extra echo "protobuf" >> requirements.txt
Documentation
- CuckooDroid – http://cuckoo-droid.readthedocs.org/
- Cuckoo Sandbox – http://cuckoo.readthedocs.org/
CuckooDroid features and functions
CuckooDroid supports analysis through various virtualization managers. Cuckoo Sandbox supports KVM, Xen, VirtualBox, and VMware for virtualization systems. CuckooDroid additionally supports AVD virtualization manager for Android emulator support.
CuckooDroid is an extension of Cuckoo Sandbox the Open Source software for automating analysis of suspicious files, CuckooDroid brigs to cuckoo the capabilities of execution and analysis of android application.

CuckooDroid’s analysis capabilities are divided into static, dynamic, and traffic analysis depending on the method. According to the analysis classification, information is gathered according to each function. Table 1 summarizes the analysis functions.
Classification | Give 1.0. | Give 2.0. |
|---|---|---|
silence | • APK File Tree • APK Static info • Certificate | • APK File Tree • APK Static info • Certificate • + Manifest |
dynamic | • Crypto • Strings • Reflection calls • Files can be accessed • Shell Commands • SMS Messages • Accounts • Loaded Files | • Crypto • Strings • Reflection calls • Files can be accessed • Shell Commands • SMS Messages • Accounts • Loaded Files • + Shared Preferences |
traffic | • TCP • SMTP • UDP • HTTP • SSL • DNS • IRC | • TCP • SMTP • UDP • HTTP • SSL • DNS • IRC |
Static analysis provides data for static API calls through data structure collection through file structure and application decompilation. It also provides general information about the Android file and provides overall components for the application such as Activity or Service.
Dynamic analysis provides results monitored through the Droidmon module. Droidmon is a monitoring module that connects Dalvik API calls to extract behavior information of an app. If the app is malicious, it prints the actual output or the path of the accessed file. In addition, if the encrypted content is present, the encryption key and the encrypted content are output as plain text. It then provides a screenshot of the overall app movement to show the actions and impacts that can occur on real devices.
It also provides analysis of network traffic. It parses the communication protocol through the URL output to the app and outputs the protocol-specific information.
Finally, through the behavior analysis, the results of the previous analysis are sorted by the related string. It extracts settings based on Androguard, or categorizes them by their associated signatures using information gathered from running apps for dynamic extraction.
Malicious APK analysis and results
- Analysis process and result
- Selection of analysis target
A smsing text message was recently received from an in-house employee. The letter impersonated a courier to attract the attention, and in order to make it difficult to analogize the web site, the malicious app was installed through the Google short URL. We will analyze the malicious behavior based on the CuckooDroid analysis platform to analyze the malicious APK file.
- (2) Analysis environment
HOST | • Ubuntu 14.04 (64bit) On VMware 12 • 4GB Memory • Quad-core |
|---|---|
AVD (Android Virtual Device) | • Nexus One • Android 4.1.2 (API Level 16) • 512MB Memory • 512MB Disk Device |
CuckooDroid | • CuckooDroid 1.0 On Cuckoo Sandbox 1.2 |
- (3) Analysis process (1/5) – Run CuckooDroid
Run CuckooDroid for malicious APK file analysis. If the execution is normally completed, AVD (Android Virtual Device) machine is loaded without any error as shown in [Figure 4-6] and the analysis is waited.
![[Figure 6] Running CuckooDroid for malicious APK analysis](https://www.kalitut.com/wp-content/uploads/2020/05/APK-file-analysis.jpg)
- (3) Analysis process (2/5) – Run Dashboard
To request malicious code analysis and confirm the analysis result, input CuckooDroid Dashboard as shown in.
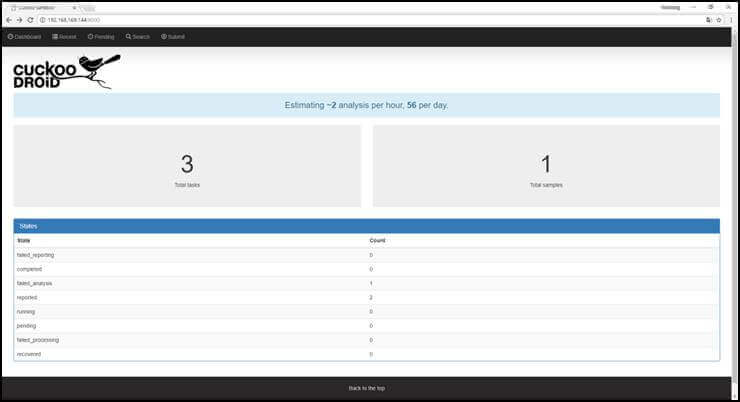
- (3) Analysis process (3/5) – Dashboard main
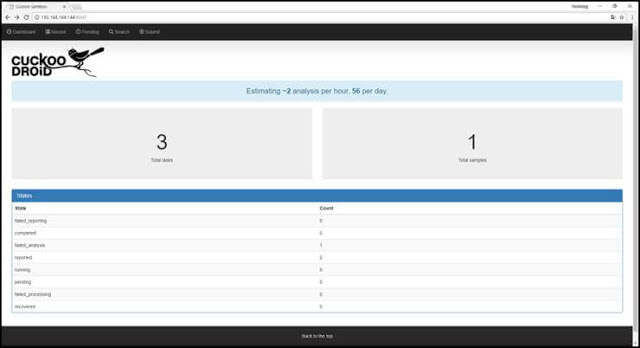
The CuckooDroid Dashboard main page allows you to view the status of waiting, running, and completed tasks as a counted value.
- (3) Analysis process (4/5) – Malicious code analysis request
- (3) Analysis process (5/5) – Check the analysis status
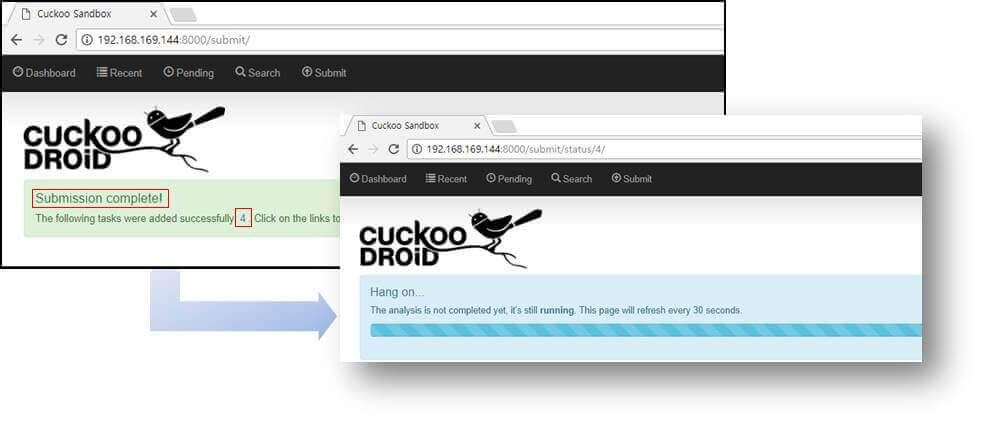
When the analysis is uploaded normally, it is added to the analysis task together with the character “Submission complete!”, And the status of the work can be confirmed when the analysis number is clicked.
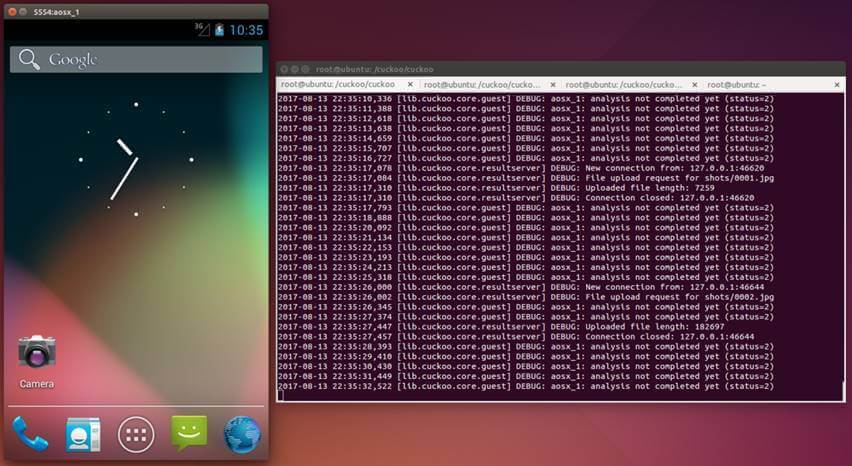
CuckooDroid can check status logs in real time on the host PC running it.
- (3) Analysis result (1/8) – Analysis result list
Through the [Recent] menu, you can check recent malicious APK analysis history as shown in [Figure 4-12]. The states that can be confirmed in the analysis result are briefly confirmed as “running”, “reported” (normal analysis), and “failed_analysis”. In addition, when the link of the MD5 hash value of the analyzed APK file is clicked, analysis details can be checked
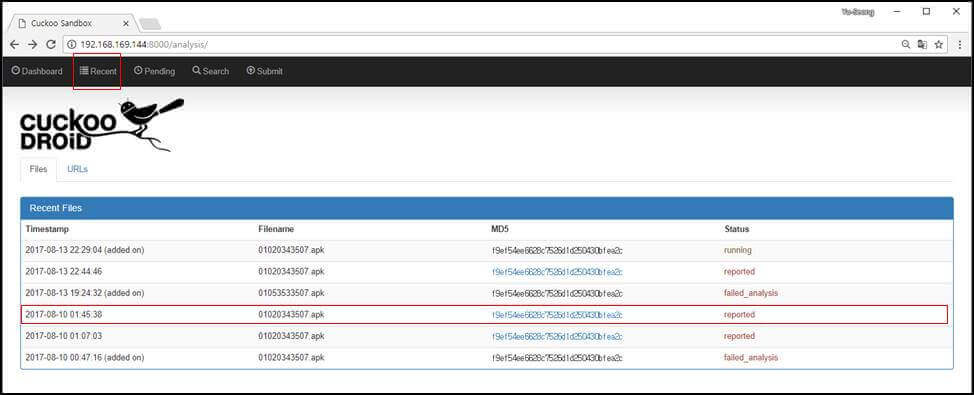
You can find general summary of malicious code information in [Quick Overview] menu.
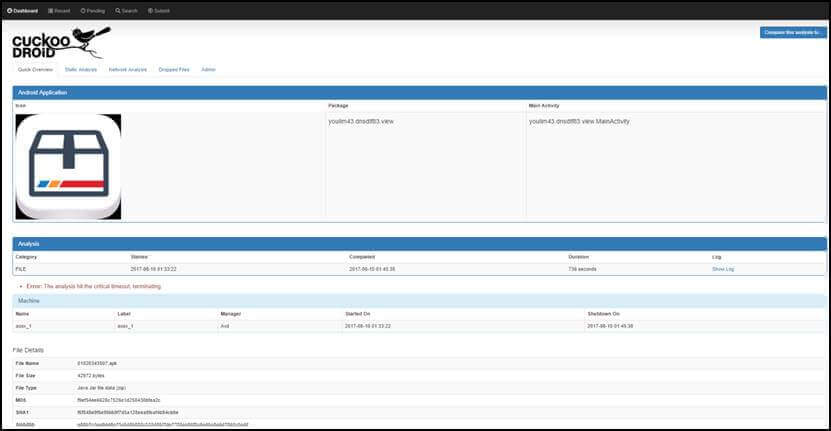
- (3) Analysis result (2/8) – [Quick Overview] menu (1/4)
Through the [Quick Overview] menu, it is possible to check malicious code malicious code through file basic information, signature information, network information, and screen shot information.
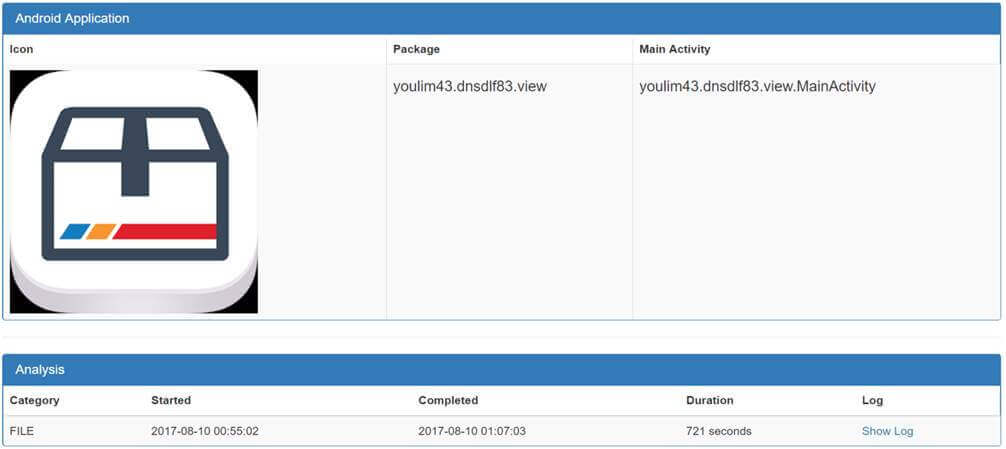
- (3) Analysis result (3/8) – [Quick Overview] menu (2/4)
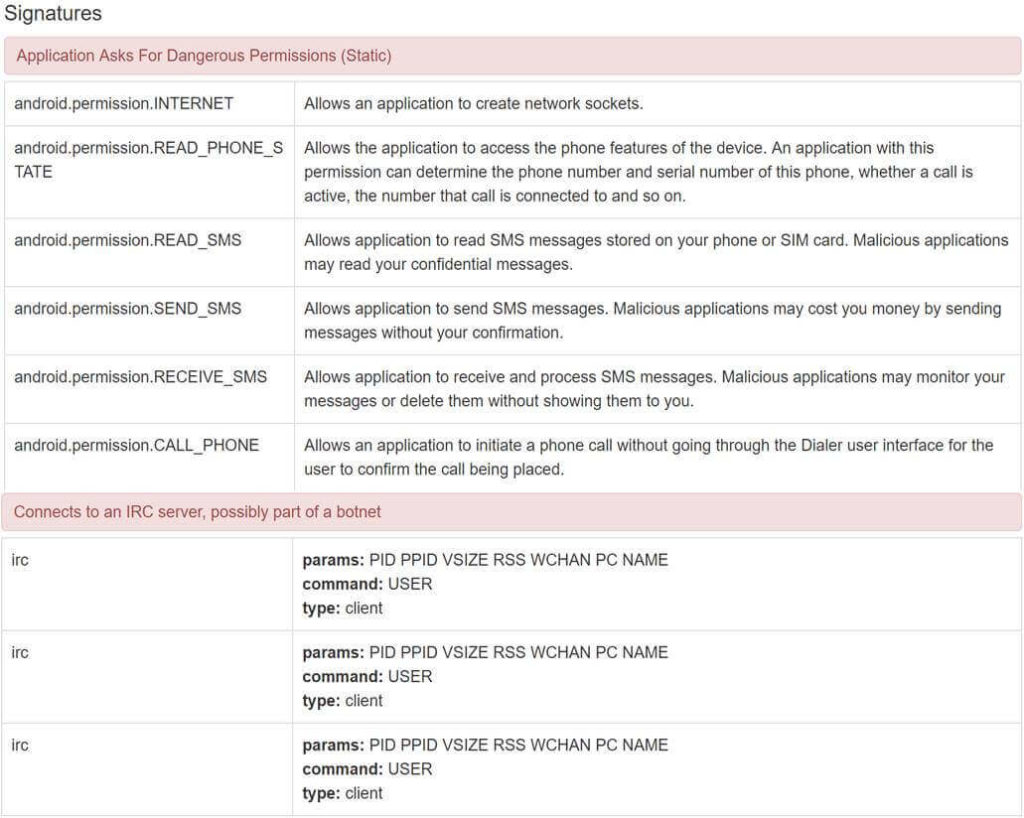
- (3) Analysis result (4/8) – [Quick Overview] menu (3/4)
![[Figure 4-16] Network Information](https://www.kalitut.com/wp-content/uploads/2020/05/CuckooDroid-Analysis-result2.jpg)
- (3) Analysis result (6/8) – [Static Analysis] menu (1/2)
Through the [Static Analysis] menu, you can see the main analysis information as shown in [Figure 4-18 ~ 22]. The Static Analysis menu provides the ability to view information such as Android Static Analysis, Certificate, File, Strings, and Antivirus. The CuckooDroid version does not provide API Static API Calls.
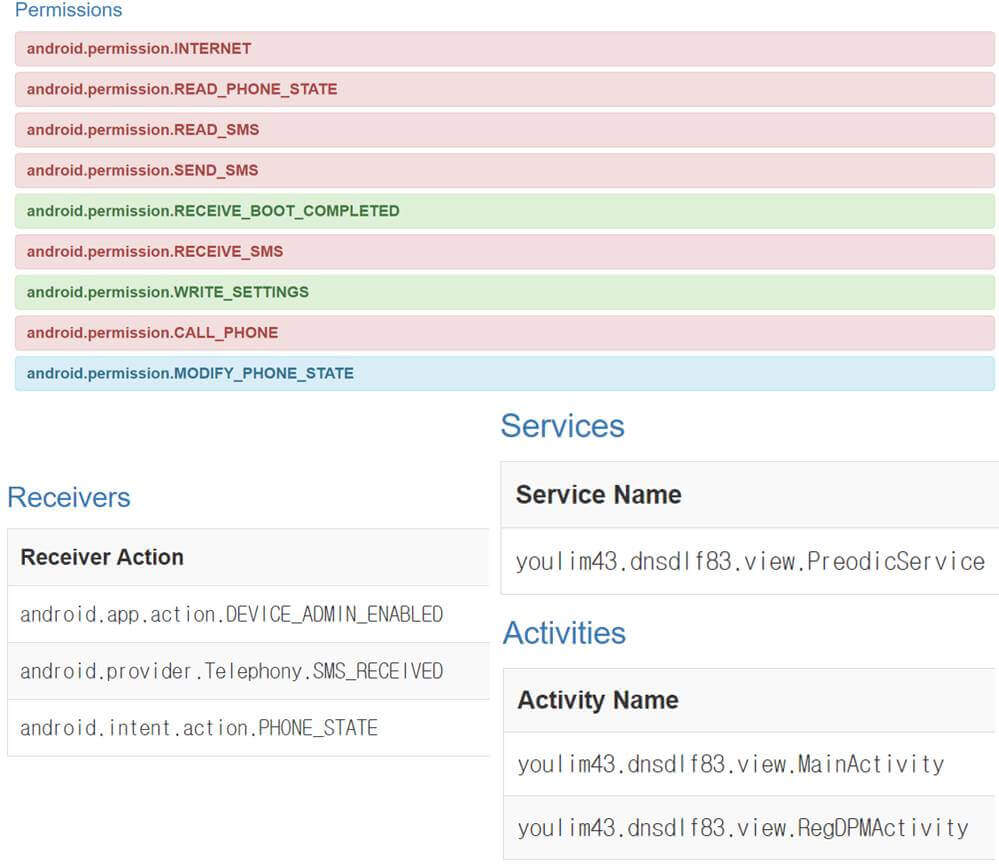
- (3) Analysis result (7/8) – [Static Analysis] menu (2/2)
![[Figure 19] App signature information](https://www.kalitut.com/wp-content/uploads/2020/05/App-signature.jpg)
![[Figure 20] APK decompilation information](https://www.kalitut.com/wp-content/uploads/2020/05/APK-decompilation.jpg)
![[Figure 21] String information](https://www.kalitut.com/wp-content/uploads/2020/05/apk-String-information.jpg)
- (3) Analysis result (8/8) – [Network Analysis] menu
Through the [Network Analysis] menu, you can check the main analysis information as shown in [Figure 4-29]. The [Network Analysis] menu basically provides a PCAP packet file and a function to check Hosts, DNS, TCP, UDP, HTTP, ICMP and IRC protocol information. The hard-coded harmful IP address is currently inactive and connection is not possible and communication is restricted.
![[Figure 22]](https://www.kalitut.com/wp-content/uploads/2020/05/apk-UDP-protocol.jpg)
4. Conclusion
We tried to analyze the actual malicious code by constructing the analysis environment of CuckooDroid 2.0 version which was recently released, but there was a limitation in the test because the stabilization task was not completed yet. Therefore, we tested the CuckooDroid 1.0 environment and completed the analysis. In 2.0 version currently distributed, various functions are added and improved, but there is a problem to be solved such as a memory dump. If it becomes a complete automation analysis system with continuous improvement in the future, it will be possible to quickly identify a large amount of malicious code malicious activity information and maximize the efficiency of analysis. In addition, it can interoperate with the existing security system to determine the threat of malicious code and respond in advance.
make sure to check or list of the best Malware Analysis books

can I run this under android?
I RTFM and the answer is negative.
yes you can
not showing any pending task in the pending window