In this cewl kali Linux tutorial, we will learn how to use CeWL to generate Custom Word List

The generator can create dictionaries based on the expressions found on the website provided in the parameter. The user can define the depth of search on the site, the minimum number of characters from which the password should be composed. In addition, the application as a crawler / spider tool can also collect e-mail addresses found on the website.
As befits such applications, it also allows you to define a proxy server or log in using the HTTP Authentication mechanism.
Parameters of the Custom Word List generator program
It seems to us that there is no point in describing all the parameters of the program because we assess the level of required English at the level of the preschooler’s troglodyte. Below is a list of arguments for the Custom Word List generator for the lazy.
root@kali:~# cewl --help
CeWL 5.1 Robin Wood ([email protected]) (http://digi.ninja)
Usage: cewl [OPTION] ... URL
--help, -h: show help
--keep, -k: keep the downloaded file
--depth x, -d x: depth to spider to, default 2
--min_word_length, -m: minimum word length, default 3
--offsite, -o: let the spider visit other sites
--write, -w file: write the output to the file
--ua, -u user-agent: useragent to send
--no-words, -n: don't output the wordlist
--meta, -a include meta data
--meta_file file: output file for meta data
--email, -e include email addresses
--email_file file: output file for email addresses
--meta-temp-dir directory: the temporary directory used by exiftool when parsing files, default /tmp
--count, -c: show the count for each word found
Authentication
--auth_type: digest or basic
--auth_user: authentication username
--auth_pass: authentication password
Proxy Support
--proxy_host: proxy host
--proxy_port: proxy port, default 8080
--proxy_username: username for proxy, if required
--proxy_password: password for proxy, if required
--verbose, -v: verbose
URL: The site to spider.
root@kali:~#
CeWL example
Below is an example of using the CeWL hack program. The program is written in Ruby and already installed in the latest version of Kali Linux 2018 at the moment.
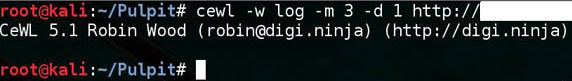
cewl -w log -m 3 -d 1 http://ADDRESS/
In the above command, the individual parameters mean:
- – in log is a result file with dictionary entries,
- -m 3 is the minimum length of the word to be added to the dictionary,
- -d 1 depth of search penetration ( recursive entering URLs found ).
The dictionary generated by the CeWL tool
Below is an example of a generated dictionary. You can further process it with other tools such as pw-inspector, or a simple proprietary Python script that adds appropriate prefixes or suffixes to words.
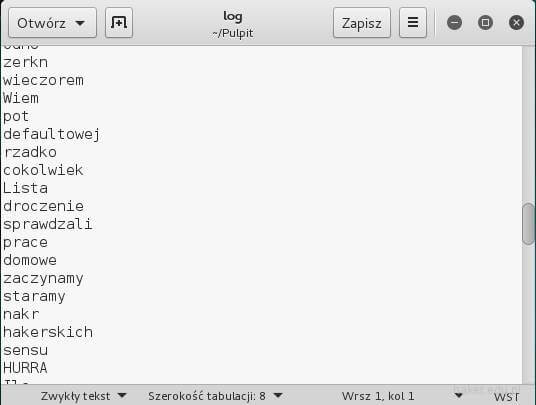
| Created a personalized dictionary using the Custom Word List generator crawler in Kali Linux. |
Summary about dictionary word generators
As you can see, you do not need to use only the attached default dictionaries with passwords from the /usr/share/wordlists folder in Kali Linux. Such generators as CeWL, crunch, pw-inspector enable you to personalize passwords for a given penetration test. Most auditors create proprietary password dictionaries for a given safety test.
There is no point in checking the big password vector because your goal is not to break super strong passwords only to determine if your operating system, service or server is secure.

Leave a Reply