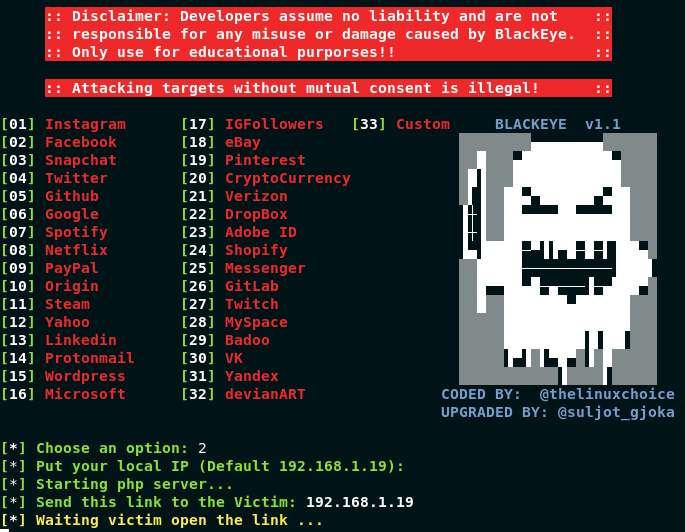
BLACKEYE The most complete Phishing Tool, with 32 templates +1 customizable
Description
BLACKEYE is an upgrade from original ShellPhish Tool (https://github.com/thelinuxchoice/shellphish) by thelinuxchoice under GNU LICENSE. It is the most complete Phishing Tool, with 32 templates +1 customizable. WARNING: IT ONLY WORKS ON LAN! This tool was made for educational purposes!
Legal disclaimer:
Usage of BlackEye for attacking targets without prior mutual consent is illegal. It’s the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program. Only use for educational purposes.
Usage:
git clone https://github.com/thelinuxchoice/blackeye
cd blackeye
bash blackeye.sh
Coded by: @linux_choice (https://github.com/thelinuxchoice/blackeye)
Give me the credits if you copy ANY part from this code. Don’t be NOOB!!
Upgraded by: @suljot_gjoka (@whiteeagle0)
Credits (Copyright) Don’t copy this code without giving the credits!!!
Phishing Pages generated by An0nUD4Y (https://github.com/An0nUD4Y):
Instagram
Phishing Pages generated by Social Fish tool (UndeadSec) (https://github.com/UndeadSec/SocialFish):
Facebook,Google,SnapChat,Twitter,Microsoft
Phishing Pages generated by @suljot_gjoka:
PayPal,eBay,CryptoCurrency,Verizon,Drop Box,Adobe ID,Shopify,Messenger,TwitchMyspace,Badoo,VK,Yandex,devianART

When i run the server it gives me a blank ipadress? what do i do
What is username
And password
I did I have to do there
Hello, Due to the file no longer existing, it askes you to sign in to make sure you are the owner of this directory because the file is now private that’s why
i click on numbers and its another thing showing, its not allowing me to choose numbers
I click the NUMBERS its not showing what do i need to do again to make it proper
I choose an option and it didn’t press the number in stead another thing was showing entirely
blackeye is down i made a backup but whenever i select an option it goes invalid
which backup are you using to use a phishing tool? After the downfall of blackeye, x3rz, script shell, It is almost impossible to do a phishing attack.
which backup are you using to use a phishing tool? After the downfall of blackeye, x3rz, script shell, It is almost impossible to do a phishing attack.
it is asking for username and password. What should be username and password?
Hello every one when I install blackeye. Phising tool can’t send the link victim